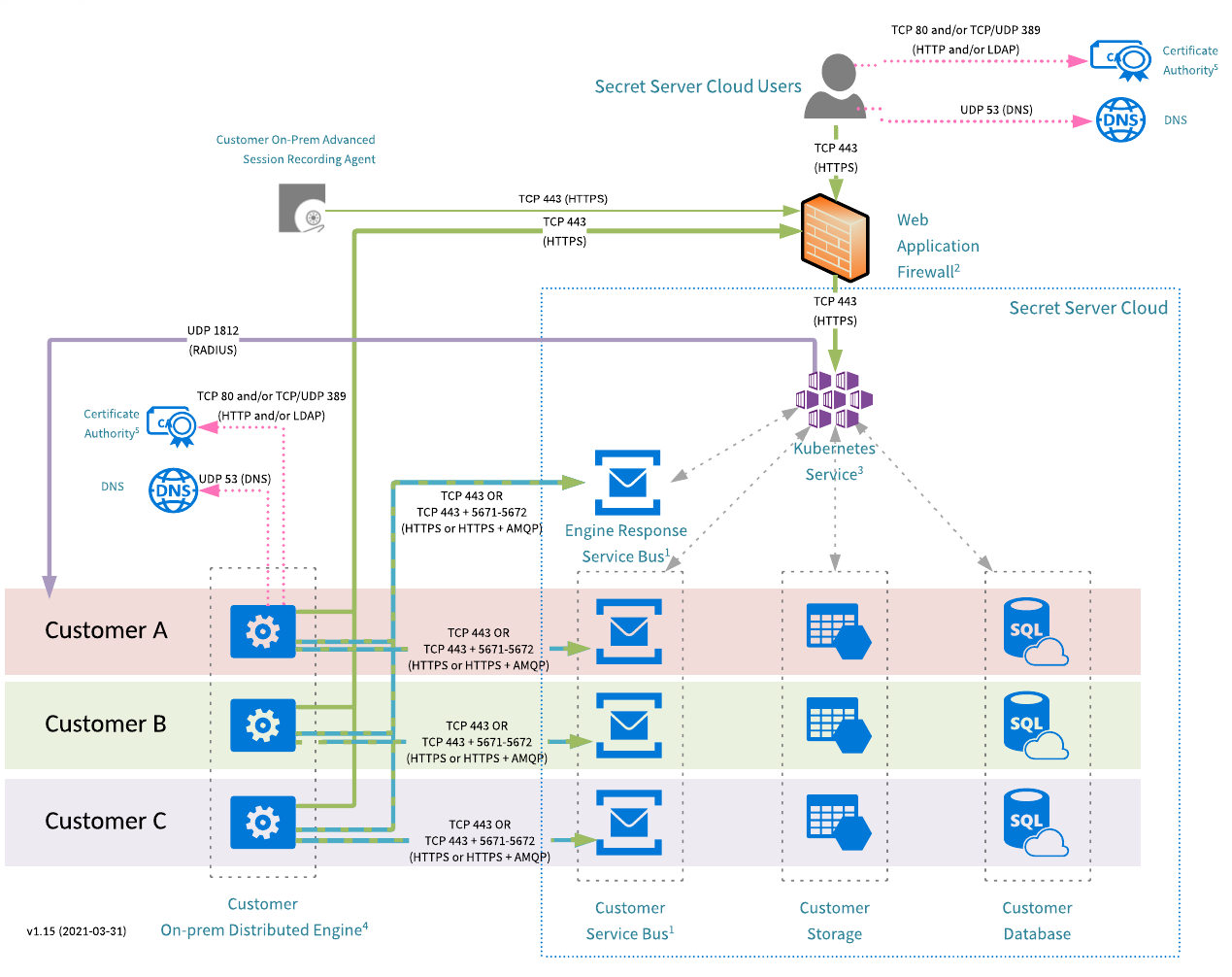
Verify Privilege Vault Hybrid Multi-Tenant Cloud Architecture
If you are a current customer with support hours for Delinea Professional Services, you can discuss any of these diagrams in detail with one of our Professional Services support architects.
This, the standard Secret Server Cloud architecture, is "hybrid multi-tenant" because only the front-end is multi-tenant, it is shared with other customers. The databases, service busses, and storage accounts are single-tenant (dedicated to you).
Diagram
Figure: Verify Privilege Vault Cloud Architecture
Arrows indicate the direction of initial connection.
Details
1: Service Buses
IP Address allowlisting is not necessary unless outbound firewall rules are in place. If IP allowlisting is necessary, you can find your customer-specific service bus IP addresses by navigating to customer.secretservercloud.com/AdminDiagnostics.aspx. The TCP port requirement is based on the transport type configured in the distributed engine settings. The default is Web sockets, which requires TCP 443. If the AMQP option is selected within the application, TCP 5671/5672 ports are also required.
The shared engine-response-bus hostnames are:
-
thycotic-ssc-eu-er-sb-01-prod-g.servicebus.windows.net
-
thycotic-ssc-eu-er-sb-01-prod-b.servicebus.windows.net (Active)
-
thycotic-ssc--er-sb-02-prod-b.servicebus.windows.net (DR)
2: Web Application Firewall (WAF)
IP Address allowlisting is not necessary unless outbound firewall rules are in place. Generally, the public IP the hostname resolves to is based on geographical location of the request source. All IPs below should be allowlisted to ensure uninterrupted connectivity.
All regions:
- 45.60.32.37
- 45.60.34.37
- 45.60.36.37
- 45.60.38.37
- 45.60.40.37
- 45.60.104.37
Your outbound requests to SSC will primarily go to the above six IPs. However, we recommend that all the IPs below should be allowed on your outbound firewall rules to maintain connectivity during some failover events where the traffic is routed through alternate network paths. Your tenants may resolve to one of the IPs in the below list during such a case.
The IP ranges from the Imperva Cloud WAF may change periodically; it is important to check frequently and stay up to date. IP ranges can be retrieved via the Imperva API. Example range output may include (but is not limited to):
-
199.83.128.0/21
-
198.143.32.0/19
-
149.126.72.0/21
-
103.28.248.0/22
-
185.11.124.0/22
-
192.230.64.0/18
-
45.64.64.0/22
-
107.154.0.0/16
-
45.60.0.0/16
-
45.223.0.0/16
-
131.125.128.0/17
3: RADIUS
Inbound allowlisting is necessary if RADIUS authentication is configured. IP addresses:
secretservercloud.com
-
20.228.138.112/29 (Primary)
-
52.190.184.16/29 (DR)
secretservercloud.co.uk
- 20.162.162.64/29 (Primary)
- 20.117.16.40/29 (DR)
secretservercloud.ca
- 40.85.220.216/29 (Primary)
- 20.220.90.80/29 (DR)
secretservercloud.eu
-
51.116.178.152/29 (Primary)
-
20.16.113.88/29 (DR)
secretservercloud.com.sg
- 52.237.113.56/29 (Primary)
- 23.100.88.144/29 (DR
secretservercloud.com.au
- 20.37.1.16/29 (Primary)
- 23.101.211.80/29 (DR)
4: Distributed Engine (DE)
If external clients must be able to connect to internal SSH or RDP endpoints, an SSH proxy can be configured on the DE. Additionally, TCP port 22 needs to be open for inbound connections on the DE server, as well as have an appropriate configuration to allow inbound connections from the public Internet.
5: Certificate CRLs
Allowlisting is not necessary unless outbound firewall rules are in place. If it is necessary, access to CRLs or OCSP endpoints may be required. CRL and OCSP endpoints may differ from customer to customer. To determine the endpoints, review the certificates presented by the:
- Web application firewall
- Customer service bus
- Engine response service bus
- CDN for DE updates