How to Select the Policy Service for Device Management
You can use IBM Security directory policy service or Active Directory Group Policy Management to set device configuration policies. When you select the IBM Security directory policy service, you use policy sets created in Admin Portal to set device configuration policies. When you use Active Directory group policy, you create group policy objects and edit them with the Group Policy Management Editor to set device configuration policies. You use roles to apply the policies to sets of users by linking the group policy object to an Active Directory organizational unit and then specify that organizational unit in the device registration settings.
You must use Privileged Access Service for mobile device management if you want to set the mobile device policies and install them in the device.
Both methods provide largely the same policies. The method you select depends upon the types of accounts (IBM Security Directory or Active Directory) used for registering devices. Use the following guidelines to select the proper method for your organization:
| You have devices registered by users with the following types of accounts | Select this method | Notes |
|---|---|---|
| Both users with IBM Security Directory and Active Directory accounts | IBM Security directory policy service | If you select Active Directory, Privileged Access Service does not install the policies in devices registered by users with IBM Security Directory accounts. |
| Only users with Active Directory accounts | Either Active Directory or IBM Security directory policy service | Select the method that is most convenient to you. |
| Only users with IBM Security Directory accounts | IBM Security directory policy service |
If you select Active Directory group policy, you still use policy sets to configure the Device Management Settings, Device Registration Settings, User Security Policies, and Application Policies. You use the group policy object just to set the device configuration policies (Policies > Endpoint Policies > settings in Common Mobile Settings, iOS Settings, etc.).
Selecting the IBM Security directory policy service
If you select IBM Security directory policy service, the Privileged Access Service uses the policy sets assigned to each role to set the device configuration policies.
Click the Download button to download the certificate for the IBM Security CA for your account for installation in the Exchange server, wi-fi access point, or VPN server or concentrator. The certificate is self-signed.
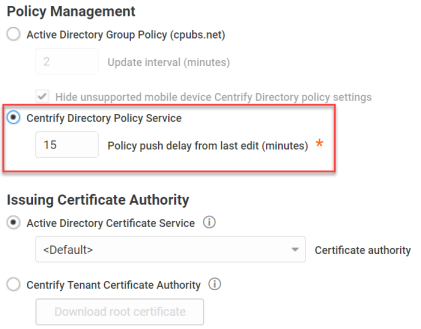
To select IBM Security directory policy service for device policy management:
-
Log in to Admin Portal.
-
Click Settings > Endpoints > Endpoint Management Settings.
-
Enable IBM Security Directory Policy Service.
-
Click the text box and enter the number of minutes for Policy push delay from last edit.
The policy push delay specifies the number of minutes Privileged Access Service waits from the time you saved the policy set to push the changes to the devices.
-
Select the issuing certificate authority.
You can use either the Active Directory Certificate Service or the IBM Security Certificate Authority (CA) to generate user and computer certificates to authenticate users and devices for wi-fi connections, respectively. The certificates are created and installed on the device when the user registers the device. The default selection is Active Directory Certificate Service.
-
Select Active Directory Certificate Service to use the default certification authority you configured in your Active Directory Certificate Service. (You can only use the default certification authority.) If you select this option, you need to create user and computer templates on the default certification authority. There may be some additional configuration required in the connector as well. See How to use Active Directory certificates in devices for authentication for the details.
-
Select IBM Security Tenant Certificate Authority to use the IBM Security CA for your Privileged Access Service account to generate user and computer certificates instead. You do not need to create templates when you select this option.
Privileged Access Service includes a self-signed IBM Security CA for each customer Privileged Access Service. When you select the certification authority, it generates certificates that can be used to authenticate users for wi-fi and VPN connections and ActiveSync server log ins (Exchange 2010 and older only). The certificates are automatically generated and installed for users who are a member of a role that has a wi-fi, VPN, or Exchange server profile in the IBM Security directory policy service in which certificates are used for authentication. The certificates are installed automatically when users register their devices.
-
(Optional) Click the Download root certificate button to download the certificate for the IBM Security CA to install in the Exchange server (2010 and older), wi-fi access point, or VPN server or concentrator.
-
-
Click Save.
Selecting Active Directory Group Policy
If you select Active Directory group policy, the Privileged Access Service uses the group policy object you linked to the organizational unit specified in the Device Registration Settings for each role to set the device configuration policies.
The certification authority you select generates certificates that can be used to authenticate users for wi-fi and VPN connections and Exchange ActiveSync server log ins. The certificates are automatically generated and installed for users who are a member of a role that has a wi-fi, VPN, or Exchange server profile in the group policy object linked to their organizational unit. The certificates are installed automatically when the user registers the device.
When you install the connector, it searches the Active Directory forest for the certification authorities you have configured in your Active Directory Certificate Service. You can select any certificate authority it finds to generate certificates.
Note: When you use an Active Directory certification authority, you need to create user and computer templates on the certification authority you select. There may be some additional configuration required in the connector as well. See How to use Active Directory certificates in devices for authentication for the details.
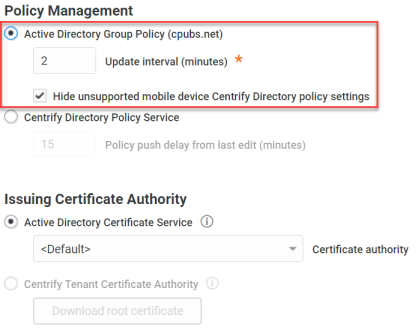
To select Active Directory for device policy management:
-
Log in to Admin Portal.
-
Click Settings > Endpoints > Endpoint Management Settings.
-
Enable Active Directory group policy in the Policy Management area.
-
Set the update interval.
The update interval sets how often the Privileged Access Service polls the domain controller for changes to the group policy objects. If the Privileged Access Service finds a group policy object has changed, it pushes the policy changes to the devices. Otherwise, it takes no action.
-
Configure Hide unsupported mobile device IBM Security Directory policy settings. Enabled by default.
Some device configuration policy settings are available for both Active Directory users policy settings managed using Windows Group Policy Management Editor (GPME)) and IBM Security Directory users (policy settings managed using Admin Portal), while some are only available in Admin Portal for managing IBM Security Directory users. When Hide unsupported mobile device IBM Security Directory policy settings is enabled, we hide those device configuration policy settings that are only available in Admin Portal to minimize confusion.
Typically, you disable this setting when your are planning to migrate your Active Directory users to IBM Security Directory, so you can see all the device configuration policy settings and make the necessary configurations.
-
Configure the issuing certificate authority.
Selecting Active Directory group policy automatically assigns the Active Directory Certificate Service as the issuing certificate authority.
If you do not want to use the default certification authority, use the drop-down menu to select another. When you install the connector, it searches the Active Directory forest for the certification authorities you have configured in your Active Directory Certificate Service. You can select any certificate authority it finds to generate certificates.
The certification authority you select generates certificates that can be used to authenticate users for wi-fi and VPN connections and Exchange ActiveSync server log ins. The certificates are automatically generated and installed for users who are a member of a role that has a wi-fi, VPN, or Exchange server profile in the group policy object linked to their organizational unit. The certificates are installed automatically when the user registers the device.
Note: When you use an Active Directory certification authority, you need to create user and computer templates on the certification authority you select. There may be some additional configuration required in the connector as well. See How to use Active Directory certificates in devices for authentication for the details.
-
Click Save.
Configuring Group Policy Objects and Organizational Units
When you use Active Directory group policy to set device configuration policies, you use group policy objects that you edit with the Group Policy Management Editor to set the policies. Next, you link that group policy object to an organizational unit. Finally, you specify the organizational unit to use for a given policy set when you configure the Device Registration Settings (see How to register devices).
The organizational unit you specify in the Device Registration Settings is also the organizational unit in which the Privileged Access Service stores the Active Directory record when the user registers the device. You can use this record in Active Directory Users and Computers to get information about the device and send it commands. See Using Active Directory Users and Computers to manage devices for the details.
When you select Active Directory group policy, you should plan on how you will apply the group policy objects to Privileged Access Service roles before you create the policy sets and assign them to the roles. When you have your roles and policies planned, you use the following procedure to apply them to individual devices:
- Create a separate organizational unit for each role.
- Create the group policy object for that role and set the policies.
- Link the group policy object to the organizational unit.
- Specify the organizational unit when you set the Device Registration Settings for the policy set (see How to register devices).
- Assign the policy set to the role.
- Add the users to the role.
You can use multiple roles or policy sets to apply different policies to users. In this case the rules for hierarchical policies are applied Using Hierarchical Policy Sets.