How to Configure Browsers for Silent Authentication
Silent authentication applies to Integrated Windows Authentication (IWA) and certain RADIUS authentication methods. For silent authentication to work when logging in to the Privileged Access Service Admin Portal, a few browser configuration tasks may be necessary.
-
Firefox: Either set
network.negotiate-auth.allow-non-fqdnto True or add the connector host name to thenetwork.negotiate-auth.trusted-urislist of trusted sites (see Configuring Firefox to Allow Silent Authentication. -
Internet Explorer: Make sure Integrated Windows Authentication (IWA) is enabled, and then in most cases silent authentication works without further configuration. Additional details are included here in case you need to make some configuration changes (see Configuring Internet Explorer Security Zones.
-
Safari: In most cases, silent authentication works without further configuration. Additional details are included here in case you need to make some configuration changes (see Configuring Google Chrome on Windows for Silent Authentication or Configuring Apple Safari on a Mac for silent authentication.
-
Chrome and Safari: In most cases, silent authentication works without further configuration. Additional details are included here in case you need to make some configuration changes (see Configuring Google Chrome on Windows for Silent Authentication.
Silent authentication works as installed with Windows Firewall. If you are using a different firewall system, be sure to allow traffic on the port specified in IBM Security Connectors in Settings in Admin Portal. By default, this port is 80.
Configuring Firefox to Allow Silent Authentication
To enable silent authentication for users logging in to the Privileged Access Service Admin Portal, you must import the tenant root CA to the browser and do one of the following in the users’ browser:
-
If you did not change the connector host name to a fully qualified domain name (by default it is not), you set the
network.negotiate-auth.allow-non-fqdnPreference Name to true.By default, the host name used by Privileged Access Service uses the format of
http://hostname, where hostname is the host name of the connector. -
If you did change the connector host name to a fully qualified domain name, you need to add the fully qualified domain names for the connector host computers to the
network.negotiate-auth.trusted-urisPreference Name.You can add the fully qualified domain names as a —for example, mycompany.com (do not enter a character)—or list each one individually. Listing them individually is more secure. However, you must remember to add the fully qualified domain name every time you add a new connector host.
To configure silent authentication in Firefox usingnetwork.negotiate-auth.allows-non-fqdn**:**
-
Open Firefox.
-
Type about:config as the target URL.
-
Type neg in the Filter field.
-
Select
network.negotiate-auth.allow-non-fqdn. If it is set to false, right-click and select Toggle. If it is already set to true, do not change it. -
Close the about:config tab and close Firefox.
To configure silent authentication in Firefox usingnetwork.negotiate-auth.trusted-uris**:**
-
Open Firefox.
-
Type about:config as the target URL.
-
Type neg in the Filter field.
-
Select and right click
network.negotiate-auth.trusted-urisand select Modify. Enter a comma-separated list of the fully qualified domain name for each connector as string values, then click OK.For example, if you have two connectors—hosta.mycompany.com and hostb.mycompany.com—you click Modify, enter the following and click OK.
hosta.mycompany.com,hostb.mycompany.comThe less-secure alternative would be to enter just the domain name. For example, you would click Modify, enter the following and click OK.
smycompany.com -
Close the about:config tab and close Firefox.
Configuring Internet Explorer Security Zones
For users to be authenticated silently when they use Internet Explorer to open Privileged Access Service Admin Portal two conditions must be met:
-
Internet Explorer must have integrated Windows authentication enabled. For details, see Enabling Integrated Windows Authentication.
-
If you are using a fully qualified domain name (FQDN) URL, the connector must be in the local intranet Internet Explorer security zone or explicitly configured as part of the local intranet security zone.
For Internet Explorer, a server is recognized as part of the local intranet security zone in one of two ways:
-
When the user specifies a URL that is not a fully qualified DNS domain name. For example, if you access an application with a URL such ashttp://acme/index.html, Internet Explorer interprets this as a site in the local intranet security zone.
By default, the connector host name is not a fully qualified DNS domain name. Privileged Access Service uses the format of https://hostname, where hostname is the host name of the connector.
-
When the user specifies a URL with fully qualified name that has been explicitly configured as a local intranet site in Internet Explorer (see instructions below). For example, if you access an application with a URL such as http://acme.mycompany.com/index.html, Internet Explorer interprets this as a site that is not part of the local intranet unless the site has been manually added to the local intranet security zone.
Depending on whether users log on to Web applications using a local intranet URL or a fully-qualified path in the URL, silent authentication may require modifying the local intranet security zone in Internet Explorer.
Enabling Integrated Windows Authentication
Use the following procedure to enable silent authentication on each computer.
To enable Integrated Windows Authentication for Internet Explorer:
-
Open Internet Explorer and select Tools > Internet Options.
-
Click the Advanced tab.
-
Scroll down to the Security settings.
-
Check the Enable Integrated Windows Authentication box.
-
Restart Internet Explorer.
Adding a Web Site to the Local Intranet Security Zone
By default, the IBM Security Connector host name is not a fully qualified domain name. When this is the case, you do not need to add the URL — https://hostname — to the local intranet, and users get silent authentication when they log in to the Privileged Access Service Admin Portal.
However, if you change the connector host name to a fully qualified domain name, you need to add the connector host FQDN URL (https://hostname.domain.com) in each user’s Internet Explorer Local Intranet before they can get silent authentication.
To add the connector host FQDN URL to the Internet Explorer local intranet:
-
Open Internet Explorer and select Tools > Internet Options
-
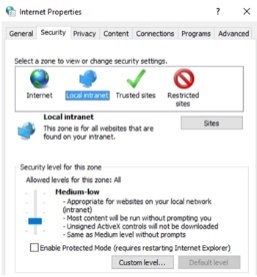
Click the Security tab.
-
Click the Local intranet icon.
-
Click Sites.
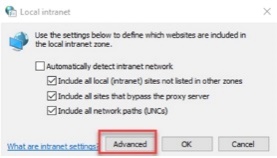
-
Click Advanced.
-
Type in the URL https://hostname.domain.com in the text box and click Add. Then click Close.
If there is a URL in the text box already, either delete it or click Add to save it.
-
Click OK to accept the local intranet configuration settings, then click OK to close the Internet Options dialog box.
Configuring Edge to Allow Silent Authentication
When using Microsoft Edge to open the Privileged Access Service Admin Portal, users can only be authenticated silently when the browser has integrated Windows authentication enabled. For details, see Enabling Integrated Windows Authentication.
For Edge, a server is recognized as part of the local intranet security zone when the user specifies a URL with a fully qualified name that has been explicitly configured as a local intranet site in Edge (see instructions below). For example, if you access an application with a URL such as http://acme.mycompany.com/index.html, Edge interprets this as a site that is not part of the local intranet unless the site has been manually added to the local intranet security zone.
Enabling Integrated Windows Authentication
Use the following procedure to enable silent authentication on each computer.
To enable Integrated Windows Authentication for Edge:
-
Open the Windows Settings and search Internet Options.
The following window opens.
-
Click Local intranet > Sites.
-
Click Advanced.
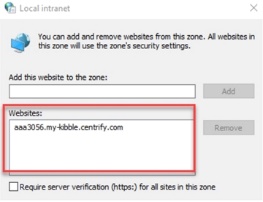
-
Enter the tenant specific URL into the Websites text box.
-
Click Close.
Configuring Google Chrome on Windows for Silent Authentication
In most cases, silent authentication works for Google Chrome without additional configuration, if the connector host name is available in your DNS.
Configuring Google Chrome on a Mac for Silent Authentication
Google Chrome on Mac requires you to whitelist an authentication server to successfully authenticate your users.
To configure Chrome on a Mac for silent authentication and single sign-on
-
Log in to your Mac device as an Active Directory user.
-
Quit any instances of Chrome, then open the Terminal.
-
Run the following command in the Terminal.
defaults write com.google.Chrome AuthServerWhitelist \<connector hostname\>
Connector hostname is the hostname set in Settings > Network > IBM Security Connectors.
Tip: If you have more than one connector configured, use a comma to separate the host names. For example:
defaults write com.google.Chrome AuthServerWhitelist host1,host2
Your users should now be able to use silent authentication with Chrome on a Mac. If the changes in the previous procedure do not take effect immediately, Quit Google Chrome and then force any remaining Google Chrome related process to quit using the Activity Monitor.
Configuring Apple Safari on a Mac for silent authentication
If you have a Verify Privilege Server Suite Agent installed on a Mac, silent authentication automatically works in the Safari web browser. For more information about IBM Security products on the Mac, see the Administrator’s Guide for Mac.