Creating Authentication Profiles
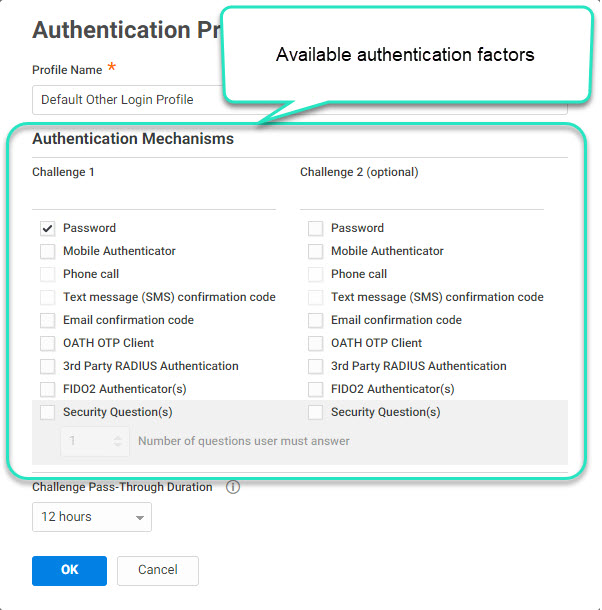
The authentication profile is where you define the required authentication mechanisms such as password, email confirmation code, mobile authenticator, and so on. You use the authentication profile when you create your authentication rule.
Three default authentication profiles are available out-of-the-box:
-
Default New Device Login Profile: Uses Password for the first challenge and Mobile Authenticator, Text message (SMS) confirmation code, Emailconfirmation code, or OATH OTP Client for the second challenge with a 12 hours pass-through duration.
-
Default Other Login Profile: Uses Password for the first challenge and no secondary challenge with a 12 hours pass-through duration.
-
Default Password Reset Profile: Gives the option for users to useCentrify Mobile Authenticator, Text message (SMS) confirmation code, Email confirmation code, or OATH OTP Client for the first challenge with a 12 hours pass-through duration.
Push notifications to 3rd party services such as email, SMS, and phone calls are subject to a delay that is independent of the Privileged Access Service. If the mobile carrier or mail provider causes a delay in receiving notifications that impact login, we recommend you use a none push authentication mechanism such as OATH token, or Centrify Mobile Authenticator's "Enter code" option which does not rely on a 3rd party service to deliver the message to the device.
To create an authentication profile:
-
Click Settings > Authentication.
-
Click Add Profile on the Authentication Profiles page.
-
Enter a unique name for each profile.
-
Select the authentication mechanism(s) you require and want to make available to users.
Some authentication mechanisms require additional configurations before users can authenticate using those mechanisms. For example, you can requirethat the first challenge be the user’s account password. Then for the secondchallenge, users can choose between an email confirmation code, securityquestion, or text message confirmation code. See Authentication Mechanisms for information about each authentication mechanism.
If you have multiple challenges, Privileged Access Service waits until users enter all challenges before giving the authentication response (pass orfail). For example, if users enter the wrong password for the firstchallenge, we will not send the authentication failure message until after users respond to the second challenge.
If users fail their first challenge and the second challenge is SMS, email, or phone call, the default configuration is that Privileged Access Service will not send the SMS/email or trigger the phone call. Contact support to change this configuration.
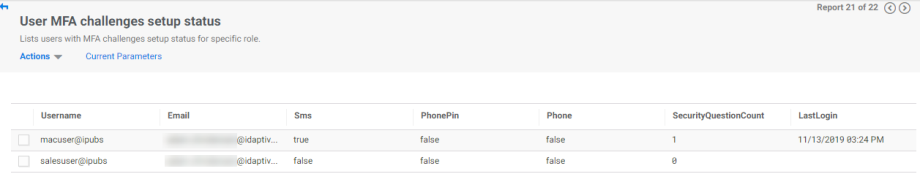
A built-in report is available to view whether users have setup the necessary information for multi-factor authentication challenges. For example, if you plan to use SMS confirmation codes as an authentication factor, you need to make sure all users impacted by the authentication policy have a mobile number associated with their account, otherwise they might be locked out.
-
From the Reports page in the Admin Portal, navigate to Built in Reports > Security, and open User MFA challenge setup status.
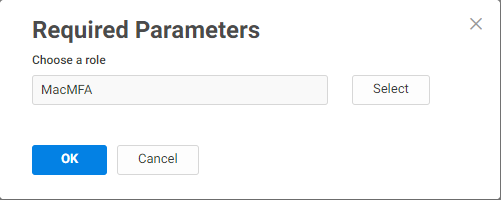
The Required Parameters window appears.
-
Select the role that will be impacted by your Authentication Policy.
For performance reasons, run this report on roles with approximately 1,000 users or less.
The report opens, showing whether your users have configured the required information for authentication factors that could result in lockout if the required information is absent. For example, a user with no associated mobile phone will have false in the SMS column.
-
Review the report and follow up with users missing required information.
-
-
(Optional) Select the pass-through duration.
If users have already authenticated using one of the specified mechanism within this duration, then they will not be authenticated again. The default is 30 minutes.
Important: This pass-through option does not apply to Windows, Linux, Unix, or Mac MFA logins.
-
Click OK.
If you have not created an authentication rule, see Creating Authentication Rules to create one and associate this profile to it.
Using Authentication Profiles to Secure Access to User Account Settings
In addition to authentication rules, authentication profiles can be used to further secure user access to specified account settings. For example, you can require that before users can modify their personal profile, they must first authenticate using a confirmation code sent via email. The relevant user account settings are:
-
Change user password -- "Configuring User Password Change Options".
-
Configure an OATH OTP client -- See How to Configure OATH OTP.
-
Create a security question -- Using Admin Portal > Access > Policies >
User Security Policies > User Account Settings > Authentication Profile
required to set Security Question drop-down list, you can select an authentication profile with the necessary authentication mechanism defined. This option will require users to authenticate before creating the security question at Profile > Security page. -
Modify personal profile information -- Using Admin Portal > Access >
Policies > User Security Policies > User Account Settings >
Authentication Profile required to modify Personal Profile drop-down list, you can select an authentication profile with the necessary authentication mechanism defined. This option will require users to authenticate before updating anything on the Profile > Personal Profile page.