How to Add a Directory Service
You can add LDAP or Google as directory services in the IBM Security Admin Portal. If you have the same username in multiple directory services, you can set the look-up order so your preferred directory service is searched first.
Refer to the following procedures for details.
Adding LDAP as a Directory Service
LDAP communicates with the IBM Security Connector over TLS/SSL on port 636. As part of the client/server handshake between the connector and the LDAP server, the LDAP server must present the connector with an X.509 certificate. To establish a trust relationship between the connector and the LDAP server, you must install the CA certificate that issued the LDAP server’s Server Authentication certificate on the machine running the IBM Security Connector (specifically, the Local Computer Trusted Root Certification Authorities certificate store).
Your LDAP servers must meet the following minimum requirements before you add LDAP as a directory service.
-
The server must support reading of the server's Root DSE (RFC 4512, section 5.1), and the Root DSE attributes must indicate that the server supports the LDAPv3 protocol.
As LDAPv2 was retired in 2003, most current servers will meet this requirement; however, any server that fails to meet these requirements is not supported.
-
A per-entry attribute that can be used as a server-scope unique identifier is required.
This attribute should be invariant, i.e. it should never change for the lifetime of the entry. This will default to the DN, but if the DN is liable to change in your installation you can specify a different attribute. In this case an operational attribute such as entry Uuid is preferred. If your LDAP server/schema lacks this operational attribute then you can try using a"unique" structural attribute as an alternative, but IBM Security does not recommend or support this.
In either case, if the attribute ever changes then the user/group that it represents will be seen as a different user/group, resulting in orphaned users, "lost" OATH tokens, and deleted app settings and assignments. It is extremely important that care be taken to select an appropriate attribute. Information about best practices for selecting an attribute for this purpose can be found here.
The selected attribute may not be changed after the configuration is created.
-
An attribute containing the user's login name must exist and must be able to be queried to obtain the entity's DN, and a simple bind using that DN and a provided credential must be able to be successfully completed.
-
The server must support the Modify Password Extended Operation for password reset/change to work as expected.
IBM Security's LDAP support is flexible enough that some servers not meeting the minimal requirements could be configured successfully, but IBM Security does not recommend or support servers that do not meet the minimal requirements.
To use the Group DN feature, your connector must be using version 21.2 or greater.
To Add LDAP for the Connector
-
Log in to Admin Portal as a system administrator.
-
Click Settings > Users > Directory Service > Add LDAP Directory.
-
In the Settings tab, provide the required information.
You can optionally set the Group DN to specify an alternate DN just for groups.When not set, the Base DN is used for both users and groups.
-
Click the Mappings tab to map your LDAP instance. See Configuring LDAP Directory Service for details on how to map your LDAP instance.
-
For group searches, the mapping will apply the keyword search to the group name and user's display name.
-
For user searches, the mapping will apply the keyword to the user's display name, first name, last name, email, and login name.
-
-
Click Connectors and select the IBM Security Connector to use with this service or let the LDAP server find an available cloud connector.
-
Click Save.
For additional information on configuring an LDAP service, see Configuring LDAP Directory Service for details.
Adding Google as a Directory Service
If you are using G Suite to store and manage your user information, you can configure Privileged Access Service to recognize it as a directory service. Users can then use their Google account details to log in to Admin Portal.
To add G Suite as a directory service
-
Log in to Admin Portal as a system administrator.
-
Click Settings > Users > Directory Service > Add Google Directory.
-
Click Authorize and enter your G Suite administrator credentials.
-
(Optional) Click Add to enter a redirect URI if you want your users to use a more recognizable URI that is specific to your organization.
-
Click Save.
Repeat the above procedure to add another Google directory.
If you use Google directory for managing your users, then do not deploy the G Suite SAML application to those same users. If you do, those users will not be able to authenticate into both Google and Privileged Access Service because they will be redirected back and forth between Google directory and Privileged Access Service.
Order Directory Service Lookup
If you have the same username in multiple directory services, you can set the look-up order so your preferred directory service is searched first. For example, you might want LDAP to be searched before AD. Directory services are listed in the order of look-up. You can change the list order to your preferred look-up order.
IBM Security Directory is always listed first, and Federated Directory is always listed last. You can only change the order of AD, LDAP, and Google.
To change the directory look-up order
-
Click Change Look-up Order.
-
Drag and drop the listed directory services until they are in the preferred order.
Directories listed on top are searched first
-
Click Save Look-up Order.
Configuring LDAP Directory Service
You can map, modify, test, or delete an LDAP Directory Service instance as detailed in:
Mapping a New LDAP Directory Service
To add and map a new LDAP Directory Service instance, perform the following steps:
-
Log in to the Admin Portal as a system administrator.
-
Click Settings > Users > DirectoryServices > Add LDAP Directory.
-
Provide the required information.
-
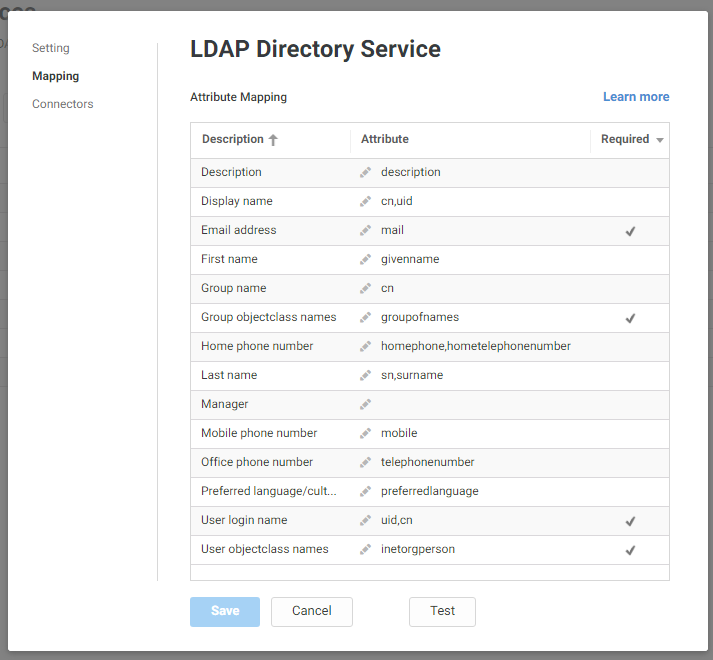
Click the Mappings tab. To set up a mapping for your LDAP, edit the attribute names in the right column to the names of the attributes in your LDAP schema that fulfill the description in the left column.
Attribute mappings may be set to required (denoted by a check in the Required column) or optional. You may choose to use several mappings simultaneously. LDAP will search for all parameters used in the mapped attributes.
The attribute mapping for "Unique Identifier" cannot be modified after saving the configuration.
-
Click Connectors and select the IBM Security Connector to use with this service or let the LDAP server find an available cloud connector.
-
Click Save.
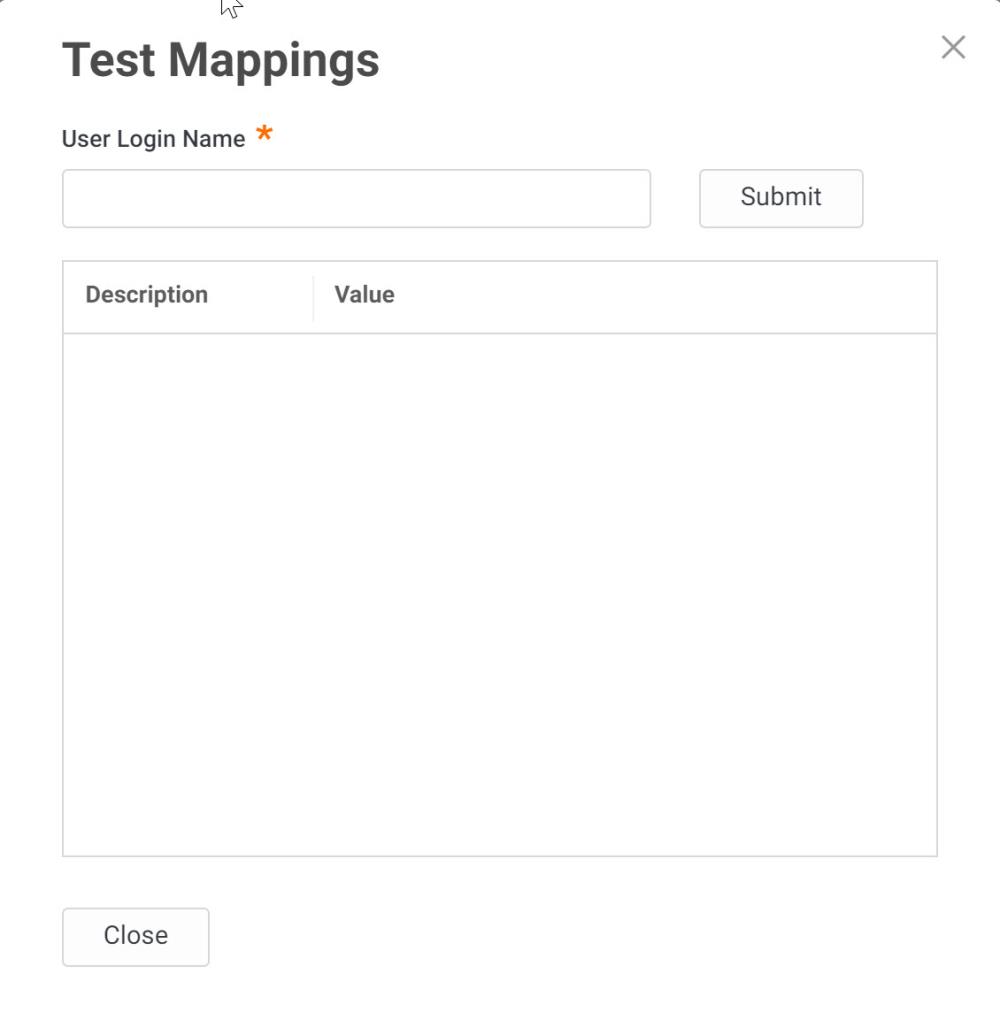
Testing the Attribute Mapping
Once you have completed mapping the LDAP service, click the Test button and enter the login name of the user you wish to test. The user entry will be loaded from the LDAP server and the attribute mapping results for that user are displayed.
Updating an Existing LDAP Directory Service
To update an existing LDAP Directory Service instance, perform the following steps:
-
Log in to the Admin Portal as a system administrator.
-
Click Settings > Users > DirectoryServices and click an existing LDAP Directory Service instance.
-
Update the values needed and click Save.
Deleting an LDAP Directory Service
To delete an LDAP Directory Service, perform the following steps:
-
Log in to the Admin Portal as a system administrator.
-
Click Settings > Users > DirectoryServices and select an existing LDAP Directory Service account.
-
Navigate to Actions and choose Delete from the dropdown.
Troubleshooting — LDAP Server Unavailable
Issue
I'm unable to configure the LDAP server in Cloud Manager. I get the error message, "LDAP server is unavailable".
Possible Explanations
-
The DNS name cannot be resolved by the IBM Security Connector machine.
-
There is no network route to the LDAP server from the IBM Security Connector machine possible because of firewall rules or other routing issues.
-
The LDAP server is not listening on port 636.
Verification Steps
Perform the following steps to verify the possible explanations:
-
From the IBM Security Connector machine, confirm that the DNS name can be resolved with dns look-up.
-
If the above confirmation is successful, confirm that there is a network path to the LDAP server by telneting to it on port 636. If the screen goes blank, it means we can connect. Use ctrl ] and type “quite” to exit.
Solutions
If the name cannot be resolved, try to enter the name in the hosts table or use the IP address of the machine. If the latter, you will likely need to un-check Verify Server Certificate on the Add LDAP Directory page.
If the server is NOT listening on port 636, append the port to the DNS hostname; for example: <dns hostname>:3269
We only support LDAP over SSL. We do not support clear LDAP.