Integrating Verify Privilege Manager and Verify Privilege Vault
Supported Integrations
The integration with Verify Privilege Vault provides the ability to use Verify Privilege Vault in either of two ways: Authentication and Vaulting.
Authentication
When usingVerify Privilege Vault for authentication, you can login to Verify Privilege Manager with users that are created and managed in Verify Privilege Vault.
The Verify Privilege Vault and Verify Privilege Manager integration for authentication purposes is not support in cloud instances. It is only supported for Verify Privilege Manager on-premises.
Vaulting
Customers can choose to integrate with Verify Privilege Vault. In Verify Privilege Vault, Verify Privilege Manager credentials are stored as secrets, and Verify Privilege Manager uses the Verify Privilege Vault REST API to communicate with Verify Privilege Vault.
Verify Privilege Vault vaults on the Delinea Platform cannot be used for integrations with Verify Privilege Manager. You are not able to enter a Delinea Platform URL in the Verify Privilege Vault foreign system configuration within Verify Privilege Manager. You must use a Verify Privilege Vault URL from an existing account on Verify Privilege Vault, not the Delinea Platform.
Setup the Integration
Proper license types need to be set-up, as Verify Privilege Vault Express (free) does not support the integration with Verify Privilege Manager.
-
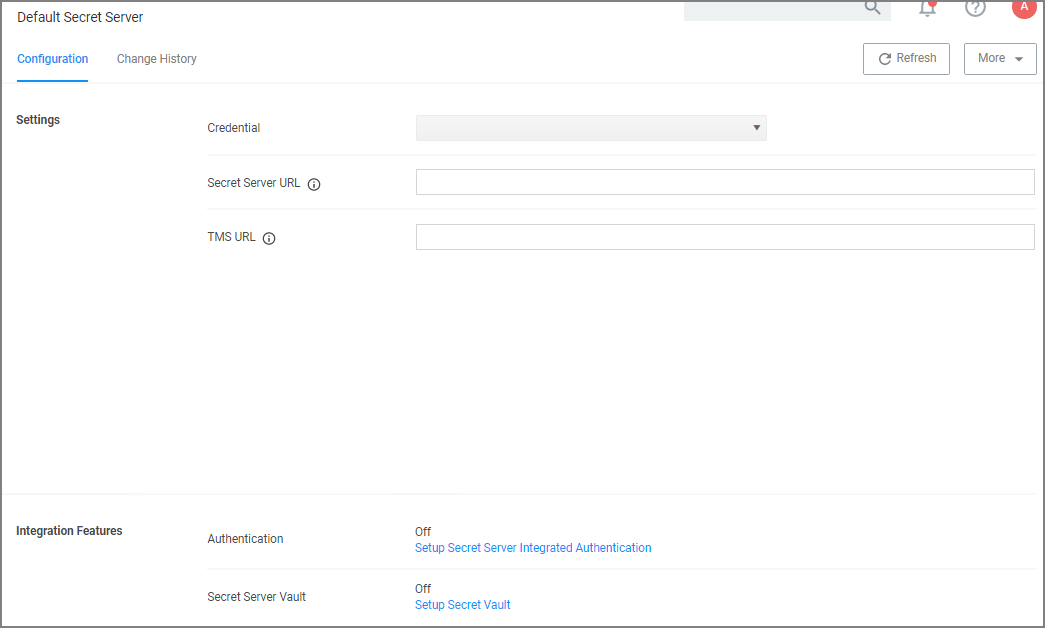
Navigate to Admin | Configuration.
-
If you do not have a Verify Privilege Vault configured, click the Advanced tab. In the General section, locate the Secret Server Vault parameter and click Configure. Provide the required parameters and click Save Changes.
-
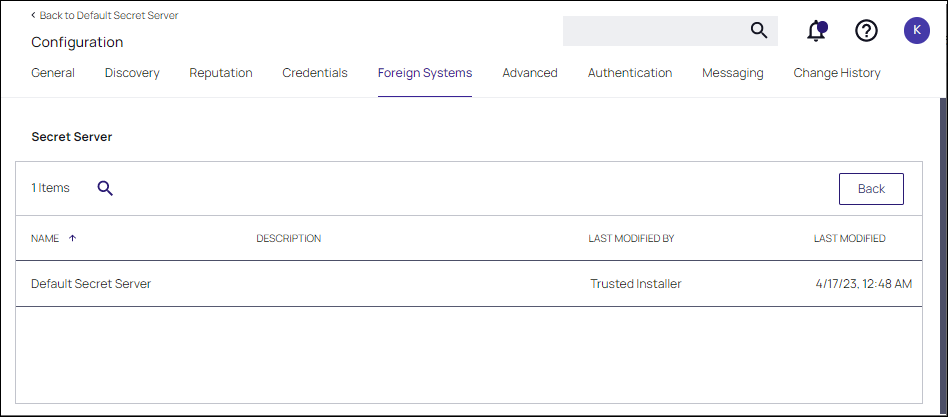
Click the Foreign Systems tab.
-
Select Secret Server from the list.
-
In the Name column, click on Default Secret Server.
-
Under Settings, update the following:
-
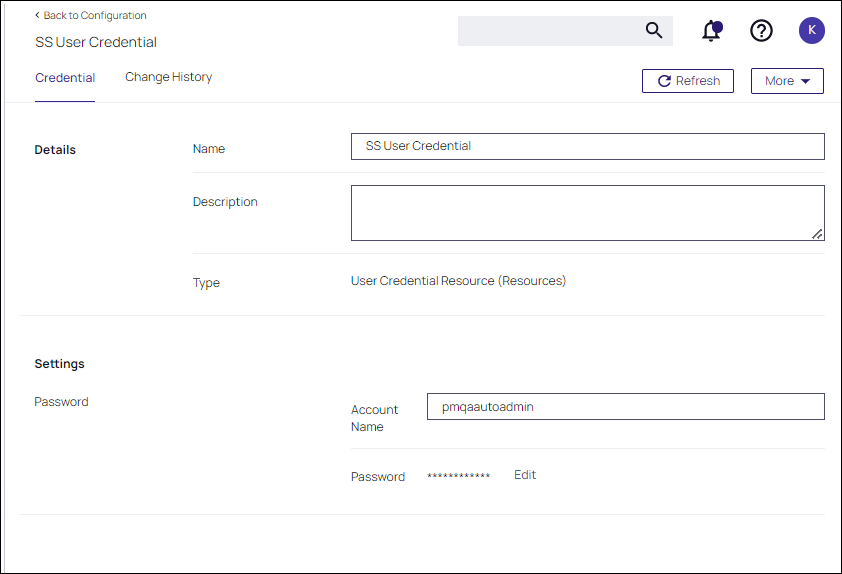
Credential: This is a Verify Privilege Vault user (preferably an application account). Refer to required permissions above. If you need to obtain credentials, in your Verify Privilege Vault application, navigate to Admin | Users and verify you have a user configured to be used for the credential setup in Verify Privilege Manager. This can be a regular Verify Privilege Vault user or a Verify Privilege Vault Application account.
An Application account is recommended. The account needs to have a role with ALL of the following Verify Privilege Vault permissions.
- Add Secret
- Administer Configuration
- Administer Folders
- Administer Licenses
- Assign Secret Policy
- Create Root Folders
- Deactivate Secret
- Edit Secret
- Own Secret
- View Secret
In your Verify Privilege Manager instance, enter the credentials for that user at Admin | Configuration | Credentials. Create/edit the defaultVerify Privilege Vault credential account to specify which account will be used by Verify Privilege Manager to connect to Verify Privilege Vault. Depending on your setup, this can be the Default User Credential in Verify Privilege Manager.
-
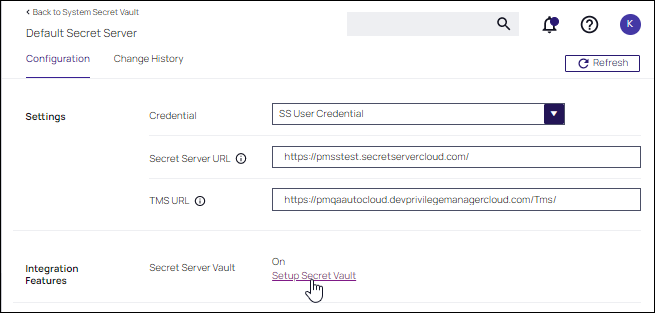
Secret Server URL: This is the URL that end users use to access Verify Privilege Vault. HTTPS is required. Also, the validation on this field reaches out to Verify Privilege Vault using the URL provided. If it can't be reached, or if the Verify Privilege Vault version is lower than v10.6, there will be a 404 not found validation error. The URL needs to be fully qualified ending with a /.
-
TMS URL: This is the URL to access TMS itself. It is the URL that end users use to access Verify Privilege Manager, minus the
PrivilegeManager/part at the end of the path. This URL also needs to be well formed and fully qualified ending with a/.
-
-
Click Save.
Integrating with Verify Privilege Vault for Verify Privilege Manager Authentication
-
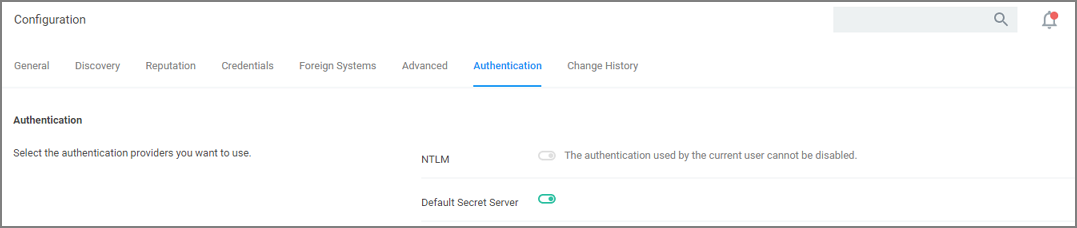
Scroll down to Integration Features | Authentication and enable Verify Privilege Vault as the authentication provider by clicking the Setup SecretServer Integrated Authentication link.
-
Set the switch for Verify Privilege Vault to enabled.
-
Click Save Changes.
After these steps the Verify Privilege Vault Foreign System is ready for use.
Integrating with Verify Privilege Vault to Store Secrets
This method of vaulting, allows passwords created in Verify Privilege Manager (user credentials, rotating passwords for agents, etc.) to be stored and maintained in Verify Privilege Vault as secrets.
Documentation for Verify Privilege Vault can be found at https://docs.delinea.com/online-help/products/secrets/current.
-
In Verify Privilege Vault, verify Web Services are enabled. Webservices can be enabled at the Administration > Configuration in the General tab.
Verify that under View Webservices the Enable Webservices option is reflecting Yes.
-
In your Verify Privilege Manager instance, select your Verify Privilege Vault instance on the Foreign System tab at Admin | Configuration.
-
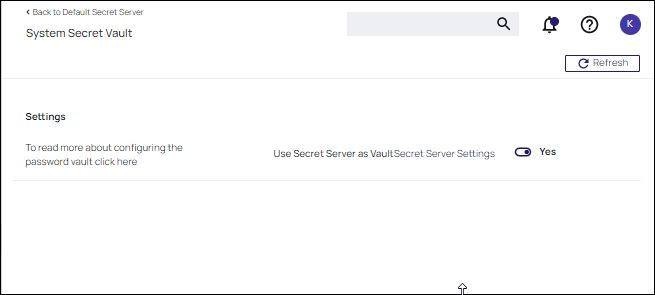
Scroll down to Integration Features | SecretServer Vault and setup Verify Privilege Vault as the vault by clicking the Setup Secret Vault link.
-
Set Use Secret Server as Vault to Yes. You are prompted to backup the Verify Privilege Vault database. Once confirmed, a task is automatically scheduled to start migrating the secrets.
Password Migration
After the vault and authentication set-up, all passwords are migrated from Verify Privilege Manager to Verify Privilege Vault. This migration process may take time.
Important Notes
The migration will create a root folder in Verify Privilege Vault named Verify Privilege Manager Secrets. Do NOT delete this folder. The folder, by default only has the sync account user as an owner, with no other permissions. The permissions on this folder can be modified to allow help desk users or administrators access to the Secrets. Do NOT remove the sync account user's permissions from the folder.
If desired, the folder can be moved or renamed within Verify Privilege Vault.
Templates
There are two Templates that Verify Privilege Manager uses to store Secrets in Verify Privilege Vault. These templates must exist with the proper fields and be marked as active.
-
Password (Template Id: 2): The following fields need to exist on the template:
- Username
- Password
Do NOT mark any other fields in that template as required!
-
Windows Account (Template Id: 6003): The following fields need to exist on the template:
- Machine
- Username
- Password
Do NOT mark any other fields in that template as required!