Resource Explorer
Resource Explorer provides information about any type of resource item in Verify Privilege Manager.
If you need to modify any items within Verify Privilege Manager, duplicate the item and modify the duplicate instead of the built-in item so that an upgrade does not overwrite it.
Resource Explorer provides:
- Summary, which contains general information, such as name, description, and modified date for any resource accessed.
- Known Data, such as any data known that relates to the resource. This data is different from resource type to resource type. For example, a domain has Global Domain Details and no account details, and a file will have all sorts of information pertaining to the file.
- Events are log-style data entries that are directly related to the resource. For example for discovered files, those are the events that are reported from and endpoint.
- Associations, are any associated/related items.
Resources can be deleted from the Resource Explorer page.
Only use Delete when you are absolutely sure that you want to delete that resource. Clicking on Delete will delete the current resource record you are viewing.
Resource Explorer is accessible by either navigating to:
-
Admin | Resources and expanding the Resources tree drilling down to a named resource to further explore and/or edit.
-
Change History tab of a named resource.
-
any named item, such as a report, in the Verify Privilege Manager console and selecting a named resource. Example navigation for the following image, Admin | Agents | select one system from the list | select one computer from "Managed Computers by Operating System " list:
Example for Discovered Files
You enter the Resource Explorer for discovered files through File Inventory on the main navigation tree. On the Events page, click any of the discovered files and use View File to drill down to the files resources.
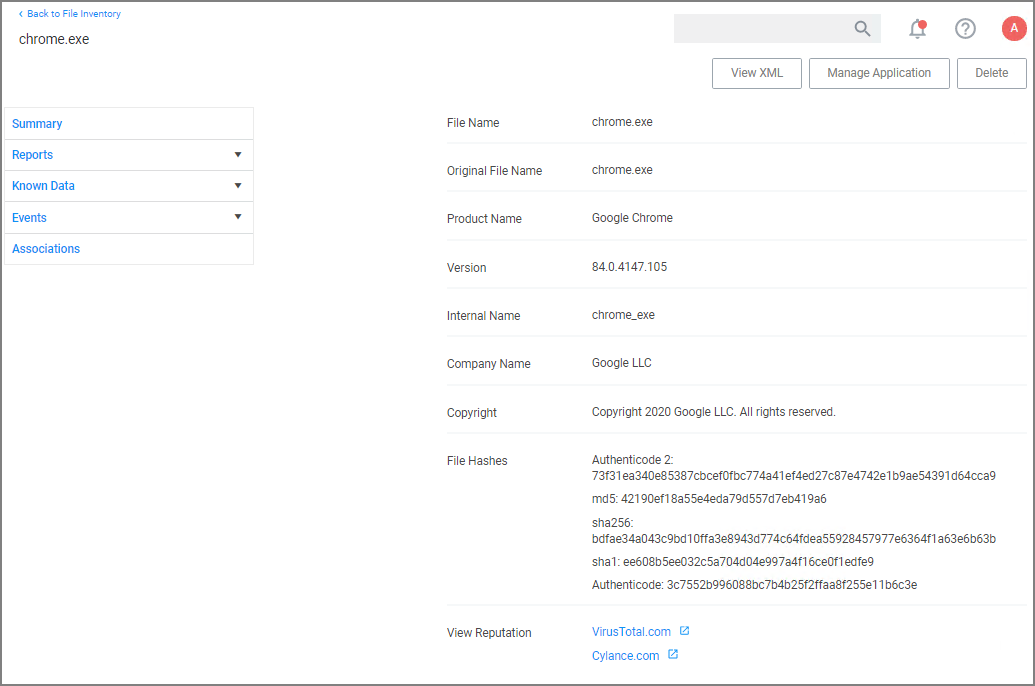
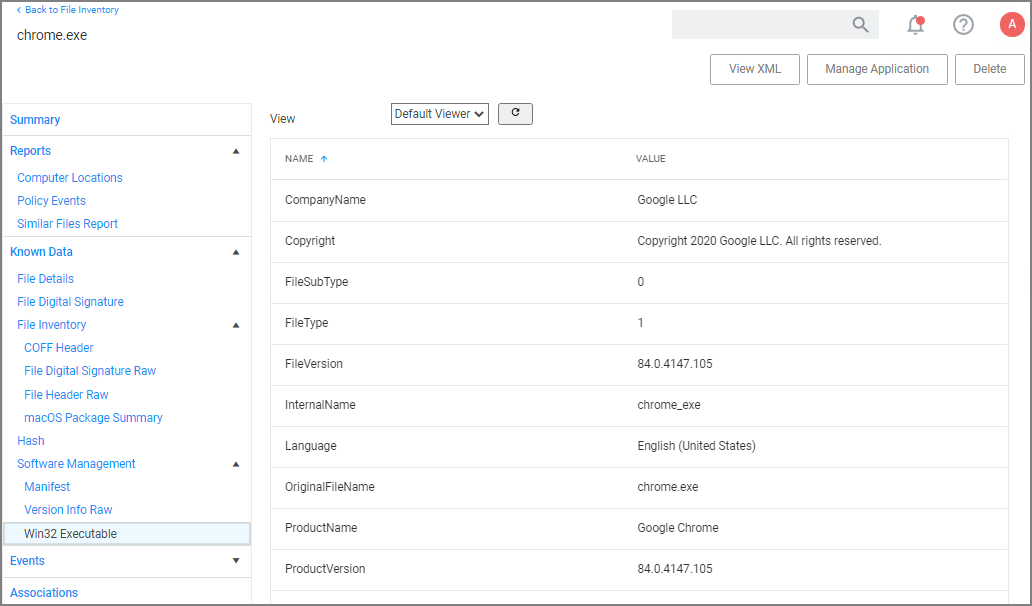
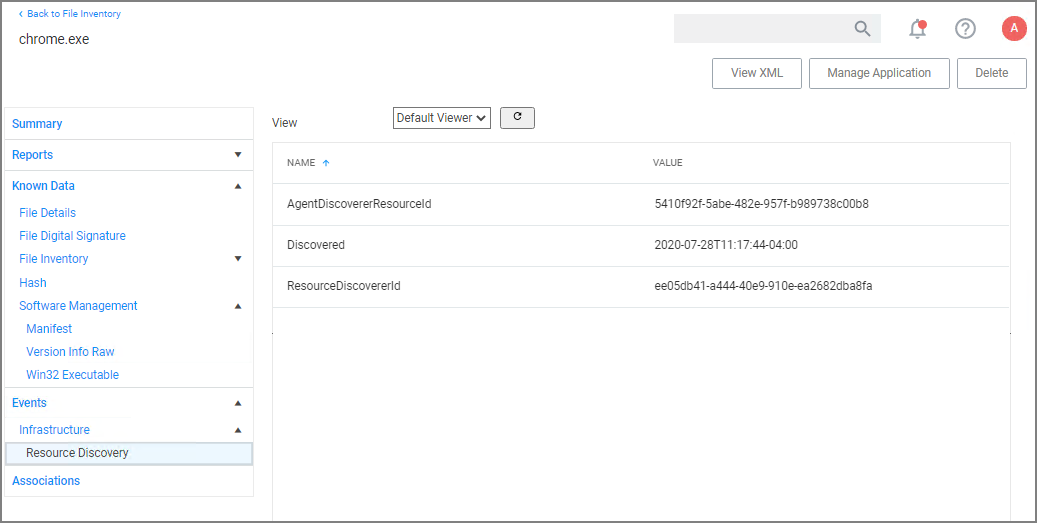
The following image shows all discovered information about the chrome.exe file, such as:
- File Name
- Original File Name
- Product Name
- Version
- Internal Name
- Company Name
- Copyright information
- File Hashes
- View Reputation, if a reputation provider is integrated with your Verify Privilege Manager instance.
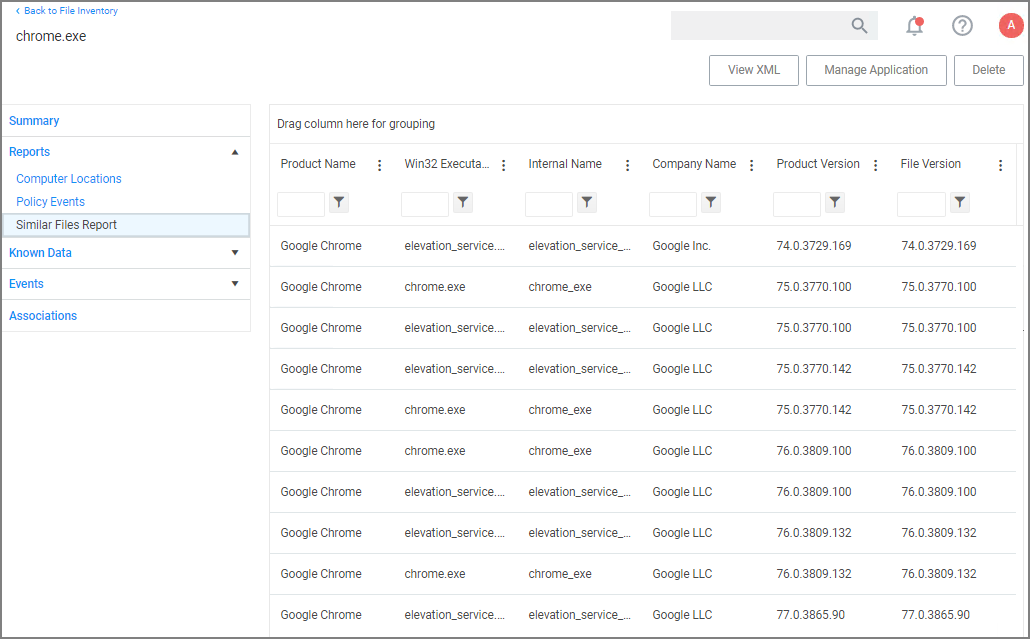
Under the Reports drop-down you can look at further details on the Computer Locations, Policy Events, and Similar Tiles Report tabs.
The Computer Locations tab provides details about the discovery locations where the file was discovered.
The Policy Events tab provides details about the policy events that triggered by the file if executed.
The Similar Files Report tab provides a list of and links to similar files that have been discovered by Verify Privilege Manager.
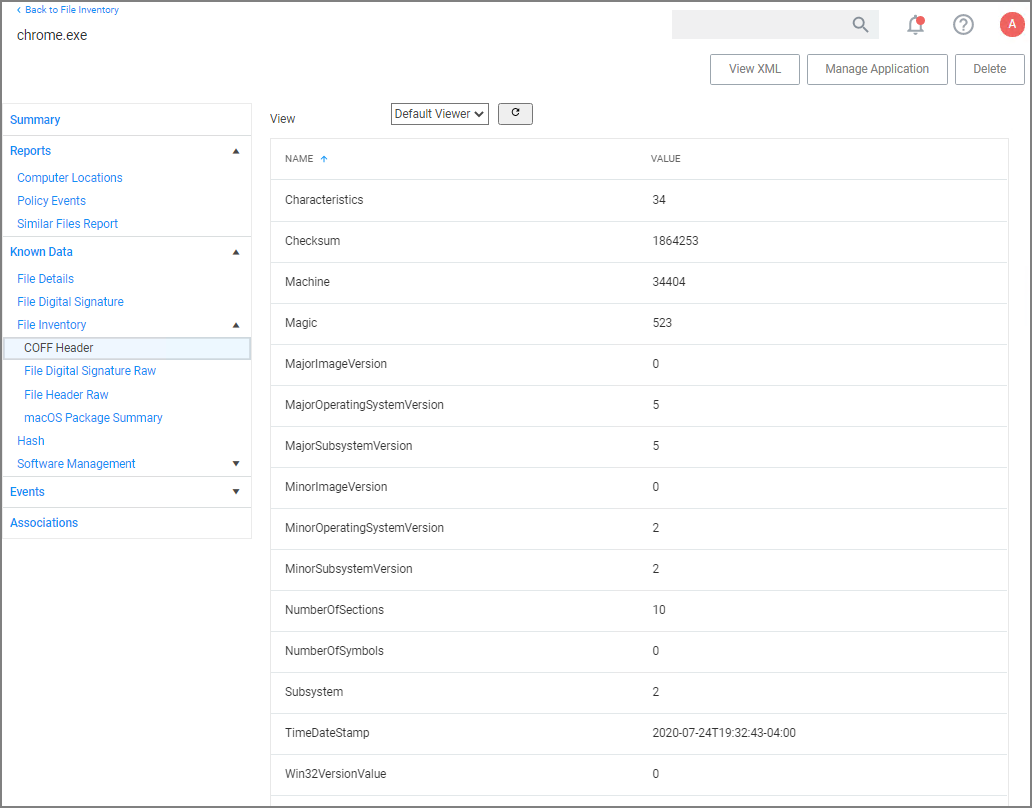
The Known Data for a discovered file includes details like:
-
File Inventory, which provides COFF Header and File Digital Signature data in raw form.
-
Software Management, which provides the files Manifest, Version Info in raw form, and Win32 Executables details.
-
File Details, such as name, file extension, file size, and if protected or not.
-
File Digital Signature, which provided information on the Signer, Countersigner if available, and the signature date/time stamp.
-
Hash, provides details on the name, the hash, and hex hash.
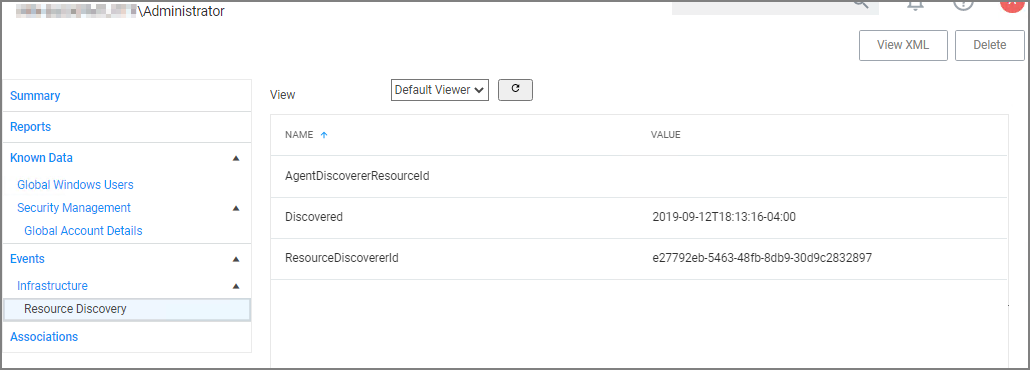
Under Events, Infrastructure offers a view into the Resource Discovery events that discovered the file, in this example the File Agent Discoverer and File Agent Discoverer (File Location) events.
This discovered file resource has no related items associated and thus the Associations area of the Resource Explorer is empty.
Example for User Resource
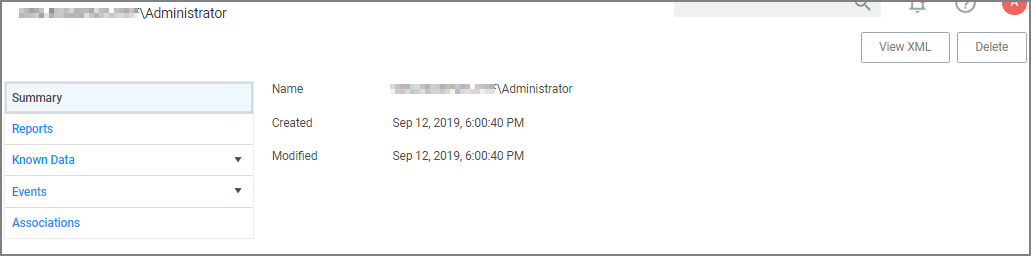
When you are looking at change history for any item and click the view user link, you access the Resource Explorer for that specific user resource. The Summary information for that specific user resources shows:
- Name – this is the user account that made the change.
- Created – indicates when the item was created.
- Modified – indicates when the item was last modified.
The resource explorer is providing information about the current state of that user resource.
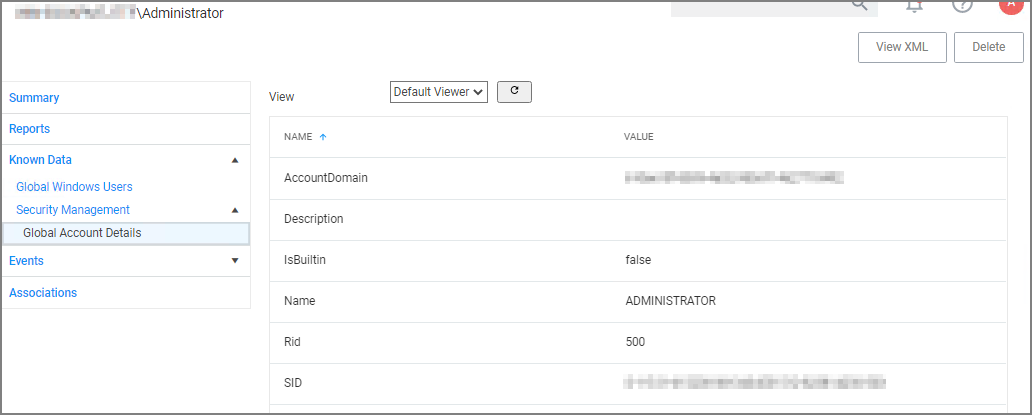
Under Known Data we can explore the information for Security Management | Global Account Details.
Users can select the View from the drop-down and see information on the type of the resource. User resources provide details about:
- AccountDomain – identifies the domain for the user account.
- Description
- IsBuiltin – can be true false to indicate if the account in built-in or not.
- Name – Name associated with the user account.
- Rid
- SID
Selecting the Global Windows Users information shows Name, Domain, and UserId.
Under Events, you can view Infrastructure | Resource Discovery information:
Under Associations you can see related items, such as Group Membership, which is based on the users credentials.
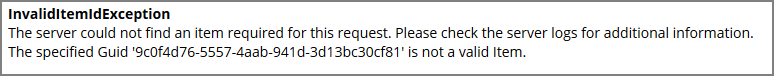
Error Message after Deleting a User Resource
In case a resource was deleted, an error message like the following will be shown the next time the resource view link is accessed.