Exclude File Extensions during File Hashing
The IBM Security Application Control Agent collects the file hash of a new process and also the hashes of the child processes it runs. Sometimes non-executable file types cause execution issues during the hashing process. Via the downloadable Configuration Feeds, IBM Security offers a policy template that provides the ability to exclude certain file extensions from the hash process.
If non-executable files like xlsx, xls, mdb, and accdb for example cause execution issues, download the Secondary Hash Exclusions policy template. By default .mdb and .accdb are excluded from the file hashing procedure in Verify Privilege Manager. To not overwrite default behavior, make them a part of your exclude list at all times.
Always manually test a new policy deployment on a single endpoint, and only push the solution to all desired workstations after a successful verification on the test environment.
This feature requires a IBM Security Control Agent version of 10.5 or greater and is only available via Configuration Feeds installation.
Default File Inventory Policy (Windows)
| Parameter | Value |
|---|---|
| Default Active | No |
| Command | Deploy Secondary Hash Exclusions Registry Key |
| Parameters | Comma-separated List of extensions to exclude, default: mdb,accdb |
| Triggers | Default: Daily at 10:00:00 PM starting Tue Jul 31 2018 (repeating every 2 hours for a duration of 24 hours) |
| Default: Upon task creation/modification | |
| Targets | Windows Computers |
| Conditions | Idle: None specified by default |
| Power: Start the task only if the computer is on AC power, Stop if the computer switches to battery power | |
| Advanced | On: Allow task to be run on demand |
| Off: Run task as soon as possible after a scheduled start is missed | |
| Off: Stop the task if it run for longer than 3 day(s). | |
| Off: If the task fails, attempt to restart | |
| Rule | Default (Do not start a new instance) |
| Agent Sent Size | n/a |
| Agent Received Size | n/a |
| Restrictions | None |
Create File Exclusion through Config Feed
-
Navigate to Admin | Config Feeds link.
-
Expand Privilege Manager Configuration Feeds.
-
Expand Application Control Solution.
-
Locate the Application Control - Secondary Hash Exclusions and click Install. The policy template is being downloaded and installed.
-
After the successful installation of the configuration feed, use Search and type Secondary Hash Exclusion.
-
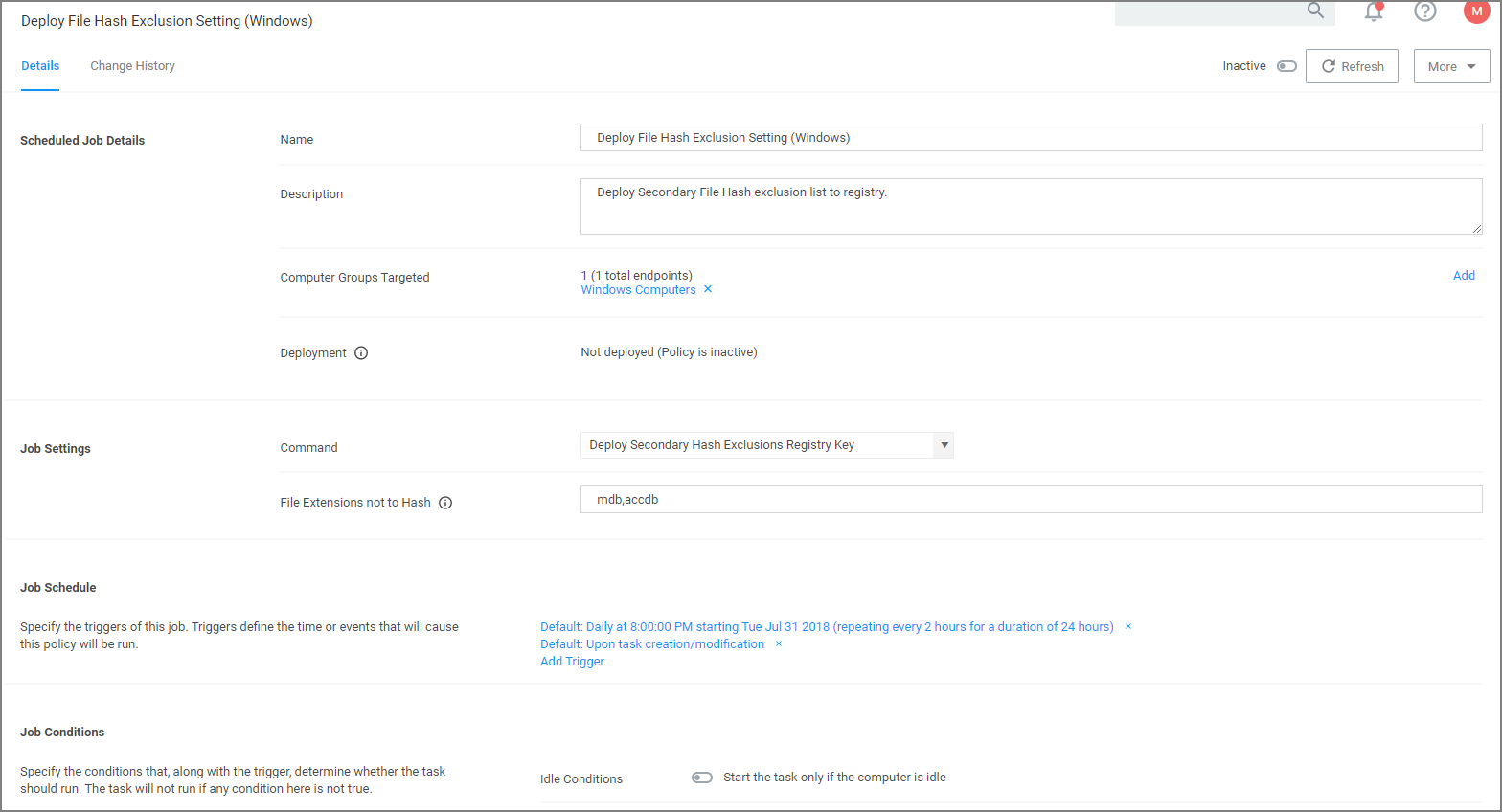
From the results list select the new policy Deploy File Hash Exclusion Setting (Windows).
-
Under Job Settings | File Extensions not to Hash you can add to the list of extensions, for example xlsx, xls. By default .mdb and .accdb extensions are already listed.
-
Click Save Changes.
Manually Test on Workstation
To create manual secondary extension exceptions to file hash collection, add a registry key to the workstation.
-
Open Registry Editor (regedit.exe) and navigate to
CopyHKLM:\Software\Policies\Arellia\AMS. -
Create New | String Value
- Name: SecondaryExtensionExclusions
- Value: enter a comma-separated list of extensions to include, i.e.
xlsx,xls,mdb,accdb.
-
Restart the Thycotic services on this machine.
Open a file matching an extension from your inclusion list and test if it works on this workstation. If it works, create a Policy to push this registry key creation to all desired workstations.