Google Authenticator
This topic describes how to set up a Verify Privilege Manager policy for enabling two-factor functionality with Google Authenticator.
Follow the steps described below to set up a policy for enabling two-factor functionality with Google Authenticator.
- If you are using the Verify Privilege Vault login for Verify Privilege Manager, make sure you log in with an Active Directory credential. If you are currently using a Verify Privilege Vault credential, you need to enable Active Directory Integration.
-
Once you log in with an Active Directory credential go to this URL:
https://[ServerName]/Tms/Account/Totp
-
There you will see the QR Code or Secret to input into Google Authenticator in order for your user account to authenticate on the endpoint. Each user will need to go to this URL after logging in to Verify Privilege Vault and add this QR Code to their authenticator app. Users can NOT re-use the same authenticator code that they are using for Verify Privilege Vault.
-
After you have done that with one of your user accounts, you need to import an XML file as follows:
- Access the topic, XML for Challenge Response Message Actions. It contains XML code, copy all that XML code.
- Go to https://[ServerName]/Tms/PrivilegeManager/#/item/xml/
- Paste the contents of the XML code (which you copied in a previous sub-step) into the text field and click the Import button.
-
You can then go to each policy for which you want to enable the two-factor prompt and add the “Challenge/Response Message Action” as an action.
It is not recommended that you do this for ALL applications that are being run.
-
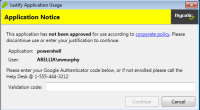
The end users will then see a prompt such as shown below, when they go to launch an application which triggers that action:
Justification prompt messages are customizable.