Application Policies
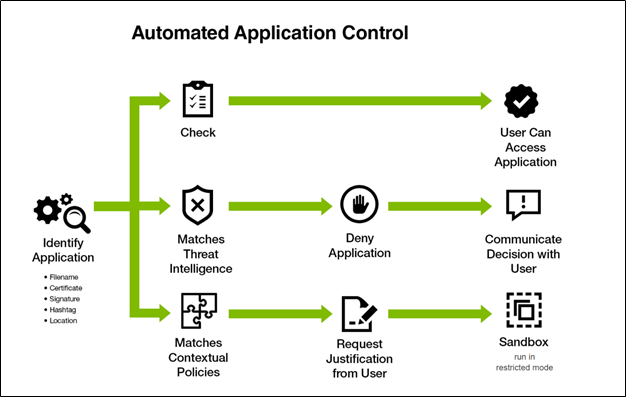
Application Control in Verify Privilege Manager allows administrators to manage all application activity on endpoints. Applications requiring admin rights or root access can be automatically elevated if trusted, applications can be allowed, and malicious applications can be blocked.
In other words, the key to keeping your organization's employees working both securely and effectively without notable disruptions to their work is by tailoring a robust, role-based Application Control system.
On the other hand, managing local administrator and root accounts through Local Security is the fastest way to lock down your network from malicious endpoint attacks that exploit administrator access.
Policy Types
Two types of policies can be created: Monitoring policies and Controlling policies.
Monitoring policies only report on the fact that an application was run, while controlling policies will actually intercede in some manner, such as elevating, restricting, blocking, requiring justification/approval, etc.
Policy Subtypes
Within policies, there are subtypes. Subtypes are associated with the types of actions that they are configured to use. A wide variety of subtypes can be created, such as managed [local] users, managed [local] groups, service hardening, etc. For example, if the policy has an Add Administrative Rights action, it's an elevate policy. If it has a Deny Execute action, it's a block/deny policy, etc.
Policy Filters
In Application Control, layered Policies create the backbone, or parameters, that dictate precisely how privileges are accessed across your network. They define what a user can run, and where. A policy is made up of customizable filters that apply an action to specific Computer Groups.
Each policy is defined by:
- Filters - What criteria needs to be met to apply this policy?
- Targets - Where should this policy be applied?
- Actions - What should happen to the applications this policy applies to? (i.e. blocked, allowed, etc.)
During the creation of a Policy you will specify actions, targets, and filters that are created separately but then assigned to Policies.
IBM Security also provides default policies that can be used out-of-the-box. Refer to Default Policies.