Using Process Explorer for Troubleshooting a Policy
This topic describes how to troubleshoot a policy with Process Explorer. Process Explorer is used to look at policies that grant administrative privileges, but don't seem to work when:
- an application is accessed, or
- actions are supposed to run.
In the example below, the policy allows resource monitor to run but the application is blank due to not having sufficient Windows Privileges. You can use Process Explorer to determine the correct Windows Privileges to add to the policy in order to use the resource monitor application.
Detailed Troubleshooting Steps
-
Download Process Explorer from the Microsoft website and extract the downloaded ProcessExplorer.zip file locally on your system.
-
Open Process Explorer.
-
Next open Resource Monitor as the Administrator.
-
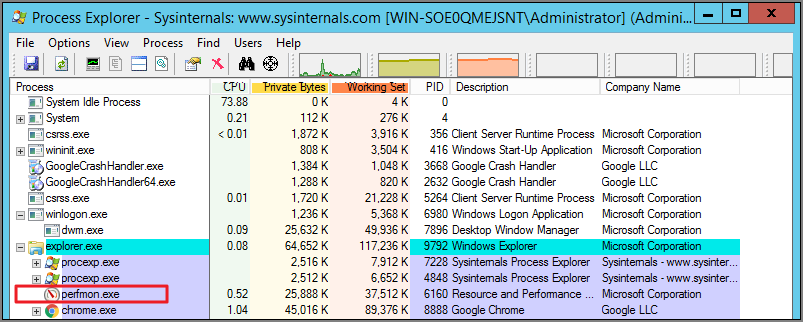
Navigate back to the Process Explorer Window and find the Resource Monitor application (perfmon.exe).
-
Right-click and select Properties.
-
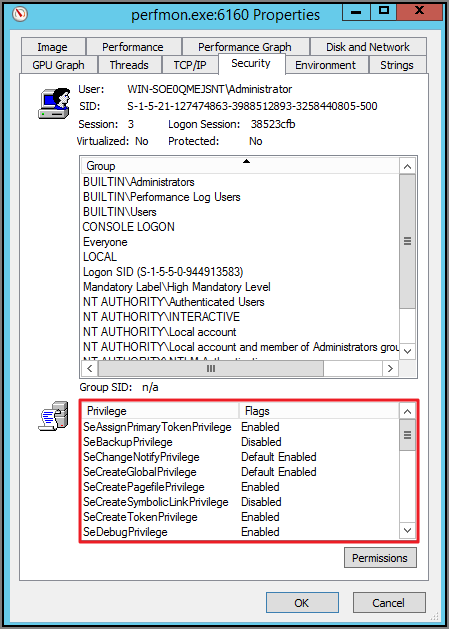
Select the Security tab.
-
Under the Privilege section, you can see all the flags that are enabled in order to use the application.
-
Launch Verify Privilege Manager and navigate to Admin | Application Policies.
-
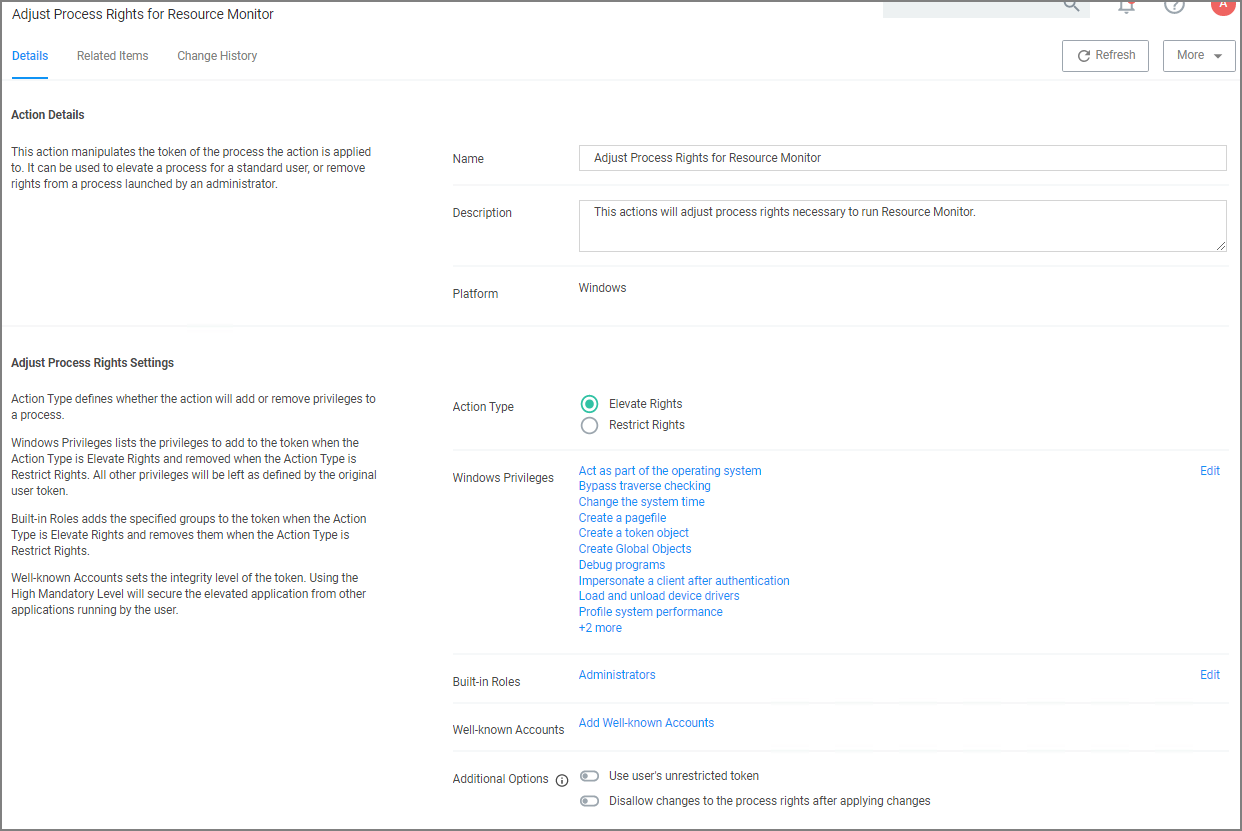
Select the policy that elevates privileges to run Resource Monitor.
-
Under Adjust Process Rights, modify settings.
- Select Add Administrative Rights or the elevation action you are using.
-
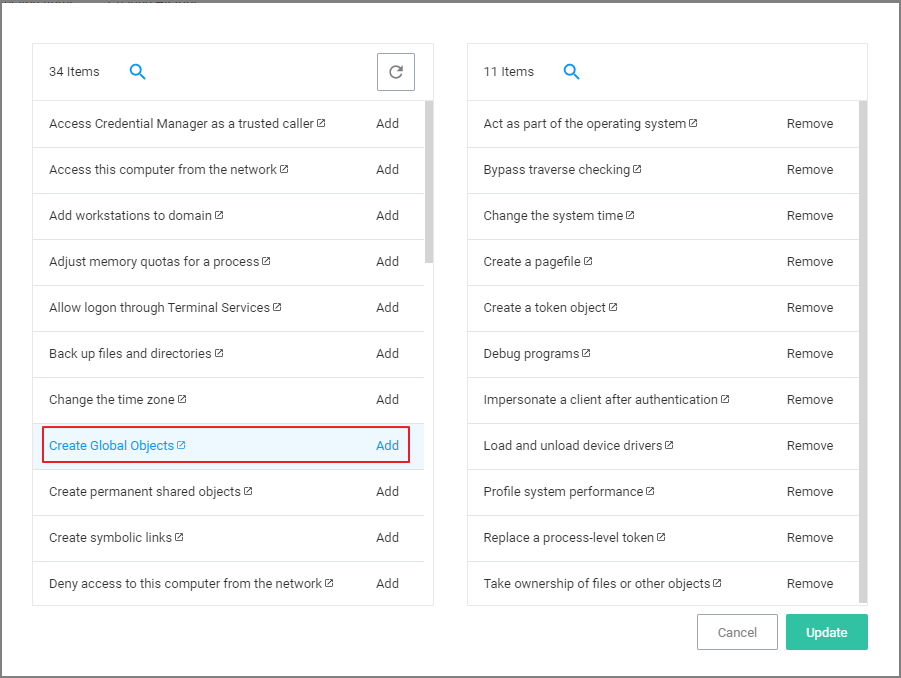
Under Windows Privileges, click Edit. (For this step you will have to determine which flags are enabled in Process Explorer in order to add the additional Windows Privileges to the action.)
-
In another window, navigate to the following Microsoft web site @ https://docs.microsoft.com/en-us/windows/win32/secauthz/privilege-constants. The site will show the name of the Windows Privileges, along with the user right information that needs to be added to the action in Verify Privilege Manager.
For Example: The privileges listed under the properties security tab show SeCreateGlobalPrivilege as enabled. On the Microsoft website for Privilege Constants @ https://docs.microsoft.com/en-us/windows/win32/secauthz/privilege-constants, the user right for SeCreateGlobalPrivilege privilege is: Create global Objects.
-
Enter the user into the search box and then select the user from the returned list. In this example, enter in Create Global Objects.
-
Click Add.
-
Remove any actions you don't need.
-
Click Update.
-
Click Save Changes.
Once the agent has received the updated policy, the additional Windows Privileges will be applied to the application next time it is launched.