Using the Demonstration Scripts
This chapter describes the ADEdit sample scripts provided in the package. The scripts are listed in the following table. The corresponding source files are in the /usr/share/centrifydc/samples/adedit directory. The source file name is shown in the table and each script header.
You have a couple of different ways to invoke scripts from the command line (see Creating ADEdit scripts under Getting Started with ADEdit). The sample scripts demonstrate two of them.
| Section Heading | Purpose | Source File Name |
|---|---|---|
| Reading command line input | These scripts illustrate two different methods for using the Tcl argv, argc, and argv0 variables. | MktDept.sh getopt-example
|
| Create a parent zone | This script illustrates how to create a IBM Security parent zone. | CreateParentZone
|
| Create child zones | This script illustrates how to create two child zones in a parent zone. | CreateChildZones
|
| Create privileged commands and roles | These scripts illustrate how to create new privileged commands and new roles that include those commands. | MakeRole ApacheAdminRole
|
| Add and provision UNIX users | This script and input file illustrate how to add users to Active Directory and copy them to the Active Directory UNIX Users group. If you have the Zone Provision Agent configured and running, you can use this script or one similar to it to automatically provision user profiles when users are added to Active Directory. | AddUnixUsers users.txt
|
| Simple tools | These scripts demonstrate how you can list the computers in a zone, extract field attributes from user objects, and list the users in a zone. | computers-report useracc-report user-report GetComputers
|
| Run a script from a script | These scripts illustrate how you can call a script (setenv) from within another script to perform different queries based on the values entered. | setenv GetChildZones GetGroups GetUsers GetZones
|
Zone Containers and Nodes
Many ADEdit commands require you to specify the zone container. This container is the root container used by IBM Securityto store the zone information for the users, groups, computers and child zones. This container can have any name and can be anywhere in Active Directory. This container can also be an organizational unit.
Before you proceed, you need to know the location of the zone containers in Active Directory and the distinguished names you use to specify the zone container and its objects.
This section illustrates some sample cases with different locations for the zone container and the distinguished name for commonly used variables in the scripts.
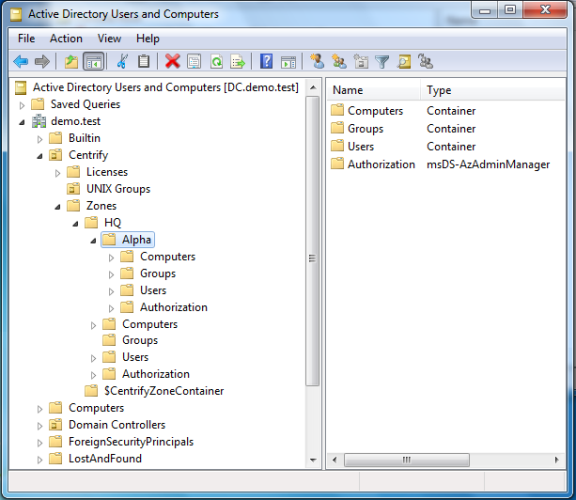
In this example, the installer defined a base organizational unit called IBM Security. This architecture is often used because it puts all the UNIX-related information in a single branch. The container with the zone information is called Zones.
In addition to the Zones container location, the installation script requires the installer to specify a location for a container to store the IBM Security software licenses. In this figure, the node—Licenses—is in the base organizational unit. However, it does not need to be there.
In this figure, the installer also created another organizational unit called UNIX Groups for the Active Directory groups used for the UNIX users. Keeping all of the groups recreated for the UNIX users in a single node simplifies managing them and the privileges assigned to each user. (With few exceptions, the UNIX users get their rights from the role assigned to the group in which they are a member.) Often, more organizational units are created for managing different classes of UNIX user and UNIX services.
There are two zones in this figure: the parent zone HQ and a child zone named Alpha. Each zone contains nodes labeled Computers, Groups, Users, and Authorization. When you specify a zone, computer, user, or group in an ADEdit command you must use the distinguished name. The following table illustrates the distinguished names.
| Object type | Example | Example distinguished name |
|---|---|---|
| Domain | demo.test | dc=demo,dc=test
|
| Base organizational unit | IBM Security | ou=Acme,dc=demo,dc=test
|
| Zone container | Zones | cn=Zones,ou=Acme,dc=demo,dc=test
|
| Parent zone | HQ | cn=HQ,cn=Zones,ou=Centrity,dc=demo,dc=test
|
| Child zone | Alpha | cn=Alpha,cn=HQ,cn=Zones,ou=Centrity,dc=demo,dc=test
|
| Organizational unit | UNIX Groups | “ou=UNIX Groups,ou=Acme,dc=demo,dc=test”
|
| UNIX group | ApacheAdmins | “cn=ApacheAdmin,ou=UNIX Groups,ou=Acme,dc=demo, dc=test”
|
| Computer in Alpha zone | RHEL | cn=RHEL,cn=Computers,cn=Alpha,cn=HQ,cn=Zones,ou=Centrity,dc=demo,dc=test
|
You should note that distinguished names can contain space, as illustrated by the UNIX Groups organizational unit. To prevent Tcl from interpreting a space as new element in a list, you can enclose the distinguished name with double quotes (“ “) or using braces ({ }). When specifying distinguished names, you should also be sure to use ou and cn correctly. Commands will fail if you refer to an organizational unit using cn.
Create Tcl Procedures
The following example demonstrates how to create procedures using the Tcl proc command. These two procedures create a new Active Directory user and Active Directory group, respectively, but first check to see if that object already exists in Active Directory.
This example uses the Tcl catch and if commands to determine if the account already exists. catch takes a Tcl script (in this case, the select_object command) and returns a 1 if an error (in this case, the account does NOT exist) occurs. Inside the if command, a non-zero result of the expression causes the body commands (puts and create_aduser or create_adgroup) to be executed. Otherwise, if select_object is successful (the account exists) it does not create the new account.
See the AddUnixUsers script for a similar example that uses the catch and if commands to determine whether a user exists.
Create Active Directory Group Procedure
# The following procedure creates an Active Directory group if a
# group with the same distinguished name does not already exist.
proc my_create_adgroup {dn sam gtype} {
if { [catch {select_object \$dn}] } {
# If we fail to select the object, the group
# does not exist. So we create it here.
puts "Creating \$dn"
create_adgroup \$dn \$sam \$gtype
} else {
puts "\$dn exists. Do not create."
}
}
Create Active Directory User Procedure
# The following procedure creates an Active Directory user if an
# account with the same distinguished name does not already exist.
proc my_create_aduser {dn upn sam pw} {
if { [catch {select_object \$dn}] } {
# If we fail to select the object, the account
# does not exist. So we create it here.
puts "Creating \$dn"
create_aduser \$dn \$upn \$sam \$pwd
} else {
puts "\$dn exists. Do not create."
}
}
Reading Command Line Input
In general, Tcl reads the arguments following the script name as a list and creates the following three variables:
argv: a Tcl list containing all of the arguments in the command lineargc: a count of the number of arguments in the listsargv0: the script name.
For example, the following script uses all three variables. This is a simple command in the form
>/bin/sh MktDept.sh name name name
where name is a person’s name, such as Mary or Joe. If you want to use first and last name, surround the name with quotes, for example “Jane Smith”.
This code sample demonstrates starting ADEdit from a shell script. The subsequent examples use the executable file model.
MktDept.sh
#!/bin/sh
# This script takes a list of names and displays it
#
# \
exec adedit "$0" ${1+"$@"}
package require ade_lib
if { $argc == 0 } {
puts "Command format: $argv0 name name ..."
exit 1
}
set total $argc
puts "
The following people are in the marketing department"
while {$total > 0} {
incr total -1
puts "[lindex $argv $total]"
}
The first if statement uses the count, argc, to determine if any arguments have been entered. If the argc value is equal to zero, the user did not enter any names and the script displays the command format message. The argc counter is used again to set the total count of names entered for the while loop. Inside the loop, the names are drawn from the argv list.
Another useful command for parsing command line options is getopt. This command derives from, but is different than, the Tcl getopt command. The ADEdit getopt command has the following syntax:
getopt _argv name ?-var?
where:
_argvis the Tcl list that contains the command line arguments.nameis a label for the associated data.?_var?is the variable name for the data.
For example, the following script illustrates the use of getopt to define the user and group variables that will be used later in the script.
This script also demonstrates how to use a procedure, usage, that prompts the user when she doesn’t enter all of the arguments. usage first displays the full command syntax and then the missing argument.
The user and password arguments are optional. If the user enters a user name without the password, the bind program automatically prompts for the password. You do not need to include that prompt in the script.
getopt-example
#!/bin/env adedit
# This script takes a domain name and optionally user name and password
# and binds the user to the specified domain.
# If the user does not specify a user name or password, she is prompted.
#
package require ade_lib
proc usage {msg} {
puts {usage: -d <domain> [-u <user>] [-p <password>]}
puts $msg
exit 1
}
if {[getopt argv -d domain] == 0} {
usage "Missing Domain, ex. centrify.demo"
}
if {[getopt argv -u user] != 0} {
if {[getopt argv -p password]} {
bind $domain $user $password
} else {
bind $domain $user}
} else {
puts "Enter administrator name:"
gets stdin user
bind $domain $user
}
puts "
Binding complete to $domain."
Create a Parent Zone
This sample script illustrates how you can create a parent zone. This script uses the puts command to display information and to prompt the user to specify variables that will be used to create the parent zone object. The command line syntax is as follows:
>./CreateParentZone - z parentZone -u adminName [-p password]
where:
parentZoneis the name of the parent zone you want to create.adminNameis the name of an Active Directory user with administrator privileges on the domain controller.passwordis the administrator’s password. If you do not enter the password in the command line, you are prompted to enter it.
Note that this sample script assumes you are using the default deployment structure with the top-level organizational unit. If you are not using the default deployment structure, you should modify the sample script to reflect the structure you are using before testing its operation.
CreateParentZone
#!bin/env adedit
# This script creates a tree zone. Use this, for example, to create the
# parent zone for child zones created in other scripts.
package require ade_lib
proc usage {msg} {
puts {usage: -z >parentZone> -u >user>}
puts $msg
exit 1
}
if {[getopt argv -z parentZone] == 0} {
usage "Missing the name for the new zone"
}
puts "
Enter the domain name for the bind command"
gets stdin domain
if {[getopt argv -u user] != 0} {
if {[getopt argv -p password]} {
bind $domain $user $password
} else {
bind $domain $user}
} else {
puts "Enter administrator name"
gets stdin user
bind $domain $user
}
set domaindn [dn_from_domain $domain]
puts "
Enter the name of the Active Directory container that holds the IBM Securityzone data"
gets stdin zonesNode
puts "
Enter the organizational unit with the IBM Securityzone data container"
gets stdin baseOU
puts "Summary:"
puts "Domain is $domain. DN for the domain is $domaindn"
puts "The base OU is $baseOU."
puts "The container for the zone information is $zonesNode"
puts "The new zone is named $parentZone"
# create the parent zone in Active Directory
puts "
Creating IBM Securityzone $parentZone"
create_zone tree "cn=$parentZone,cn=$zonesNode,ou=$baseOU,$domaindn" std
puts "Created new zone: cn=$parentZone,cn=$zonesNode,ou=$baseOU,$domaindn"
Create Child Zones
This script creates two child zones in the domain and parent zone specified in the command line. The command line syntax is as follows:
>./CreateChildZones -d domain -z parentZone [-u adminName] [-p password]
where:
domainis the domain nameparentZoneis the name of an existing zoneadminNameis the name of an Active Directory user with administrator privileges on the domain controllerpasswordis the administrator’s password. If you do not enter the password in the command line, your are prompted for it
The *password is optional. If you do not type it in the command line, the script prompts you to enter it.
The script binds to the domain you specify using the user name and password you provide. The script then prompts you to enter the name of the organizational unit and container in which you store the zone information. After that, it prompts you to enter names for the two child zones. Note that this sample script assumes you are using the default deployment structure with the top-level organizational unit. If you are not using the default deployment structure, you should modify the sample script to reflect the structure you are using before testing its operation.
To confirm the script ran successfully, open Access Manager and expand the Child Zones node under the parent zone you specified in the command line. If the two new child zones are listed, you can right-click each zone name to see its zone properties.
CreateChildZones
#!/bin/env adedit
# This script creates 2 child zones in the domain and parent zone
# specified in the command line.
#
package require ade_lib
proc usage {msg} {
puts {usage: -d <domain> -z <parentZone> [-u <user>] [-p <password>]}
puts $msg
exit 1
}
if {[getopt argv -d domain] == 0} {
usage "Missing Domain, ex. demo.test"
}
if {[getopt argv -z parentZone] == 0} {
usage "Missing parent zone, ex. HQ"
}
if {[getopt argv -u user] != 0} {
if {[getopt argv -p password]} {
bind $domain $user $password
} else {
bind $domain $user}
} else {
puts "Enter administrator name"
gets stdin user
bind $domain $user
}
puts "
Enter the name of the container for the IBM Securityzone data"
gets stdin zoneContainer
puts "
Enter the organizational unit for the IBM Securityzone data"
gets stdin zoneContainerOU
# Define distinguished name for domain
set domaindn [dn_from_domain $domain]
puts "
Summary:"
puts "Domain is $domain. DN for the domain is $domaindn"
puts "The base OU is $zoneContainerOU."
puts "The container for the zone information is $zoneContainer
"
# Create child zones
puts "Enter child zone name"
gets stdin czone1
puts "
Enter another child zone name"
gets stdin czone2
create_zone tree "cn=$czone1,cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn" std
create_zone tree "cn=$czone2,cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn" std
# link the children to parent
select_zone "cn=$czone1,cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn"
set_zone_field parent "cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn"
save_zone
select_zone "cn=$czone2,cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn"
set_zone_field parent "cn=$parentZone,cn=$zoneContainer,ou=$zoneContainerOU,$domaindn"
save_zone
puts "
Child zones $czone1 and $czone2 created in $parentZone"
Create Privileged Commands and Roles
Users get the rights necessary to run privileged commands and access applications from their role assignments. The predefined UNIX Login role gives users basic access to UNIX computers without any elevated privileges. The scripts in this section illustrate how you can create roles with additional rights. The first sample script uses a separate text file to define a new role and the commands users in that role are allowed to execute. The second sample script illustrates how to define the commands and the role within the script after prompting for bind credentials and the target zone.
Both scripts create the same commands and role.
Privileges and Role Defined in a File
For the first sample script, a single role and its privileged commands are defined in the file Role_apacheAdmin.txt. This sample text file defines the role name and a few sample commands that you might assign to an Apache server administrator. For example:
ApacheAdminRole
vi /etc/httpd/conf/httpd.conf
apachectl *
htpasswd *
The first line in the Role_apacheAdmin.txt file specifies the new role name. The subsequent lines specify the commands to add to the role. You can edit the text file to suit your environment. For example, you might want add or remove commands or modify the path to the Apache configuration file. To create the role and commands, you can then run the MakeRole sample script and specify the Role_apacheAdmin.txt file name as a command line argument. The MakeRole sample script then prompts you to enter the domain name, account, and password for the bind command and to type the name of the parent zone where the sample role will be created.
Note that you must specify a parent zone for this sample script. The second sample ApacheAdminRole script, shown in the Privileges and Roles Defined in the Script section below, displays the list of zones in the domain to illustrate how you can create a role in a child zone. In addition, this sample script assumes you are using the default deployment structure with the top-level organizational unit. If you are not using the default deployment structure, you should modify the sample script to reflect the structure you are using before testing its operation.
MakeRole
The MakeRole sample script creates a role with the set of privileged commands defined in the sample Role_apacheAdmin.txt file.
#!/bin/env adedit
# This script creates a role consisting of a
# set of privileged commands
# The role name and commands are specified
# in a separate file.
#
# The first line in the input file should be
# the new role name.
# The subsequent lines are the names of the
# privileged commands to
# add to the role.
# For example:
# audit_admin_cmds
# /usr/bin/vi /etc/security/audit/config
# /usr/bin/vi /etc/security/audit/objects
package require ade_lib
if { $argc != 1 } {
puts "usage: $argv0 file"
exit 1
}
if {[catch {set fp [open [lindex $argv 0] r]} errmsg]}
{
puts "Cannot open [lindex $argv 0]."
exit 1
}
# Get domain and bind
puts "Enter domain name"
gets stdin domain
set domaindn [dn_from_domain $domain]
puts "Enter account name with administrator privileges"
gets stdin administrator
puts "Enter $administrator password"
gets stdin APWD
bind $domain $administrator "$APWD"
# Select the target zone and base organizational unit
puts "Enter the target zone name for the new role"
gets stdin zonename
puts "
Enter the name of the Active Directory container that holds the IBM Securityzone data"
gets stdin zonesNode
puts "
Enter the organizational unit with the IBM Securityzone data container"
gets stdin baseOU
select_zone "cn=$zonename,cn=$zonesNode,ou=$baseOU,$domaindn"
if {[gets $fp line] == -1} {
puts "Cannot read [lindex $argv 0]."
exit 1
}
# Create role
puts "Creating role...$line"
set role $line
new_role "$role"
save_role "$role"
set count 0
while {[gets $fp line] >= 0} {
incr count
# Create command. Each command will be named
# based on the role defined in the first line
# and the command’s line number in the file
set cmd_name $role$count
new_dz_command "$cmd_name"
# set the command fields
set cmd_path $line
set_dzc_field cmd "$cmd_path"
set_dzc_field dzdo_runas root
set_dzc_field umask 077
# prevent nested execution
set_dzc_field flags 1
# save the command
save_dz_command
# Add the command to the Role
add_command_to_role "$cmd_name"
}
close $fp
save_role "$role"
Privileges and Roles Defined in the Script
In this sample script, you create the same Apache administrator commands and role as the previous script. However, this script displays a list of the zones in the domain and lets you select in which zone to create the commands and role.
ApacheAdminRole
#!/bin/env adedit
puts "This script creates privileged commands and the ApacheAdminRole in the zone entered"
package require ade_lib
puts "
Enter the domain name"
gets stdin domain
puts "
Enter the account name to use to modify Active Directory"
gets stdin acctName
bind $domain $acctName
set domaindn [dn_from_domain $domain]
set zonelist [get_zones $domain]
set numberZones [llength $zonelist]
set row 1
set zonenum 0
puts "
This domain contains the following zones"
while {$numberZones != 0} {
puts "$row. [lindex $zonelist $zonenum]"
incr zonenum
incr row
incr numberZones -1
}
puts "
Enter the row number of the target zone"
gets stdin rowSelect
set zone [lindex $zonelist [incr rowSelect -1]]
select_zone "$zone"
puts "
Creating command-level Apache admin rights in $zone"
puts "
Creating web_edit_httpd_config"
new_dz_command web_edit_httpd_config
set_dzc_field cmd "vi /etc/httpd/conf/httpd.conf"
set_dzc_field description "edit httpd config file"
set_dzc_field dzdo_runas root
set_dzc_field dzsh_runas root
set_dzc_field path /usr/local/apache2/bin
set_dzc_field flags 1
save_dz_command
puts "
Creating web_apachectl"
new_dz_command web_apachectl
set_dzc_field cmd "apachectl *"
set_dzc_field description "Web Apache Server Control"
set_dzc_field dzdo_runas root
set_dzc_field dzsh_runas root
set_dzc_field path /usr/local/apache2/bin
save_dz_command
puts "
Creating web_htpasswd"
new_dz_command web_htpasswd
set_dzc_field cmd "htpasswd *"
set_dzc_field description "Web Apache Manage user files"
set_dzc_field dzdo_runas root
set_dzc_field dzsh_runas root
set_dzc_field path /usr/local/apache2/bin
save_dz_command
#--------------------------------------------------------------------
# Create ApachedAdminRights role
# The new_role command creates the role in the currently selected zone.
puts "
Creating the ApacheAdminRole with these rights"
# In each role you need to set the sysrights with the set_role_field
# to the following binary values
# password_login = 01
# sso = 02
# ignore_disabled = 04
# full_shell = 08
new_role ApacheAdminRights
add_command_to_role web_edit_httpd_config
add_command_to_role web_apachectl
add_command_to_role web_htpasswd
set_role_field sysrights [expr 0x0000000b] #full_shell | sso | password_login
save_role
save_zone
Add and Provision UNIX Users
It is difficult to provision a lot of UNIX users and ensure that the UID is unique in the domain. To assist you with the process, IBM Security provides a set of features called the Zone Provisioning Agent. The Zone Provisioning Agent includes a service that automatically assigns a unique UID and other UNIX profile attributes, such as the home directory, default shell, and primary GID, based on rules you define.
This script demonstrates how you could use the Zone Provisioning Agent to add and provision users. For this sample script, the list of UNIX users is defined in the source file named users.txt and the Active Directory source group is Unix Users.
Note:To learn more about the Zone Provisioning Agent and automated provisioning, see the Planning and Deployment Guide.
users.txt
You specify the names to be added in a text file in which each name is on a separate line. Be sure to use line feed only as the end-of-line; do not use CR-LF. The sample file in the distribution package contains the following names:
Amy.Adams
Brenda.Butler
Dennis.Day
Eric.Edwards
AddUnixUsers
In the following script, you specify the file name with the user names in the command line. The script then prompts you for the additional information required. The target Active Directory group—Unix Users—is hard-coded into the script.
This script uses the Tcl catch command three times to control processing when an error occurs.
- In the first case, it is used to exit gracefully if the specified file cannot be opened.
- In the second case,
catchis used to determine if the user already exists. An error here indicates that the user does not exist and, rather than exiting, theelsestatement creates the user. (If the user already existed, you would not want to create another Active Directory account.) - In the third case,
catchis used to exit gracefully if the user is already a member of theUnix Usersgroup.
#!/bin/env adedit
# This script creates an Active Directory account
# for each user the specified
# and adds the user to UNIX Users group.
# This automatically fills in their UNIX profile.
# Command line input: file name w/ user names in
# format ffff.llll only
# Prompted input: domain, administrator
# name, default password
package require ade_lib
if { $argc != 1 } {
puts "usage: $argv0 file"
exit 1
}
if {[catch {set users [open [lindex $argv 0] r]}
errmsg]} {
puts "Cannot open [lindex $argv 0]."
exit 1
}
# Get domain and bind
puts "Enter domain name"
gets stdin domain
set domaindn [dn_from_domain $domain]
puts "Enter account name with administrator privileges"
gets stdin administrator
puts "Enter $administrator password"
gets stdin APWD
bind $domain $administrator "$APWD"
puts "
Define password to be used for all accounts"
gets stdin pwd
# Now start creating accounts from users
# example: "cn=Ellen Edwards,cn=Users,$domaindn"
# "Ellen.Edwards@$domain" ellen.edwards pwd
while {[gets $users sam] >= 0} {
set name [split $sam .]
set dn "cn=[lindex $name 0] [lindex $name 1],
cn=Users,$domaindn"
set upn $sam@$domain
if { [catch { select_object $dn }] } {
# If we fail to select the object,
# most probably it
# does not exist. So we create it here.
puts "Creating $dn"
create_aduser $dn $upn $sam $pwd
} else {
puts "$dn exists. Skip creating."
}
# Because we already installed and started ZPA,
# this provisions the
# Active Directory account
catch { add_user_to_group $sam@$domain
"UNIX Users@$domain" }
}
close $users
Simple Tools
The following scripts are simple “utilities” for getting information from Active Directory about the managed computers and users accounts:
- computers-report: Lists the managed computers in the zone.
- useracc-report: List the Active Directory users in the domain and several account properties.
- user-report: Lists the users in a zone.
- GetComputers: Lists all of the managed computers in the specified domain and the zone to which each computer is joined.
Following these scripts are sample scripts that demonstrate how you can use a script that calls, for example, commonly-used commands in other scripts. For more information, see Run a Script from a Script below.
computers-report
Use this command to list managed computers in the zone. The command line arguments are as follows:
| Label | Required/Optional | |
|---|---|---|
| -domain | required | Domain name. |
| -m | optional | Bind using the ADEdit host computer’s credentials (see bind). You can use either the computer credentials (-m) or the user account credentials (-u). |
| -u | optional | Administrator’s account name. |
| -p | optional | Administrator’s account password. Note: If you do not enter the password in the command line you will be prompted to enter it. |
| -sep | optional | Separator used between data. The default is separator is the pipe (|) character. |
#!/bin/env adedit
# This script lists the managed computers on the zone.
# Command line input is the domain, the
# administrator account name and
# the separator to use between computer's field
# values in the output
package require ade_lib
# Lists all of the managed computers and the zone
proc usage {msg} {
puts {usage: -domain <domain> [-m] [-u <user>]
[-p <password>] [-sep csv | tab | <char>]}
puts $msg
exit 1
}
if {[getopt argv -domain domain] == 0} {
usage "Missing domain"
}
set verbose 0
if {[getopt argv -v]} {
set verbose 1
}
set sep "|"
getopt argv -sep sep
if {$sep == "csv"} {set sep ","}
if {$sep == "tab"} {set sep "\t"}
if {[getopt argv -m]} {
bind -gc -machine $domain
} else {
if {[getopt argv -u user]} {
if {[getopt argv -p password]} {
bind -gc $domain $user $password
} else {
bind -gc $domain $user}
} else {
bind -gc $domain
}
}
# this code runs entirely off the GC
cache on
set scps [get_objects -gc -depth sub [dn_from_domain $domain] {(&(displayName=$CimsComputerVersion*)(objectClass=serviceConnectionPoint))}]
foreach scp $scps {
select_object -gc $scp
set name [get_object_field name]
set parent ""
# first look for parentLink
foreach k [get_object_field keywords] {
set bits [split $k ':']
if {[lindex $bits 0] == "parentLink"} {
set sid [lindex $bits 1]
#ok we got it
# make sure it exists
catch {set parent [principal_from_sid $sid]}
}
}
# if we didn't then try by managed By (DC3)
if {$parent == ""} {
set mb [get_object_field managedBy]
if {$mb != ""} {
set parent $mb
}
}
set orphan 0
if {$parent == ""} {set orphan 1}
set path [get_parent_dn [get_parent_dn
[get_object_field dn]]]
set zone [string range [get_rdn $path] 3 end]
puts $name$sep$zone$sep$orphan
}
useracc-report
Use this command to list all users and their Active Directory account control values. The command line arguments are as follows:
| Label | Required/Optional | Description |
|---|---|---|
| -domain | required | Domain name |
| -m | optional | Bind using the ADEdit host machine’s credentials (see bind) Note: If you use -m you do not need to enter -u |
| -u | optional | Administrator’s account name. |
| -p | optional | Administrator’s account password. Note: If you do not enter the password in the command line you will be prompted to enter it. |
| -sep | optional | Separator used between data. Default is | |
#!/bin/env adedit
# This script lists all the users and their Active Directory account control values
package require ade_lib
# List users and the following field
proc usage {msg} {
puts {usage: -domain <domain> [-m] [-u <user>] [-p <password>] [-sep csv | tab | <char>]}
puts $msg
exit 1
}
if {[getopt argv -domain domain] == 0} {
usage "Missing domain"
}
set verbose 0
if {[getopt argv -v]} {
set verbose 1
}
set sep "|"
getopt argv -sep sep
if {$sep == "csv"} {set sep ","}
if {$sep == "tab"} {set sep "\t"}
if {[getopt argv -m]} {
bind -machine $domain
} else {
if {[getopt argv -u user]} {
if {[getopt argv -p password]} {
bind $domain $user $password
} else {
bind $domain $user}
} else {
bind $domain
}
}
cache on
proc my_convert_msdate {msdate} {
if {$msdate==9223372036854775807} {
return -1
}
return [clock format [expr ($msdate/10000000)-11644473600] -format "%m/%d/%y %H:%M:%S"]
}
proc nice_date {date} {
if {$date == ""} {return $date}
if {$date == 0} {return ""}
set ret [my_convert_msdate $date]
if {$ret == -1} {return ""}
return $ret;
}
set users [get_objects -depth sub [dn_from_domain $domain] "(objectcategory=Person)"]
foreach user $users {
select_object $user
set uac [get_object_field userAccountControl]
if {$uac == ""} {continue}
# gof is get_object_field
eval "set name [gof cn]"
#puts [gof dn]
set sam [gof sAMAccountName]
set exp [nice_date [gof accountExpires] ]
set locked [nice_date [gof lockoutTime] ]
set lastlogon [nice_date [gof lastLogon] ]
set enabled [expr $uac&0x2 ]
set enabstr "False"
if {$enabled} {set enabstr "True"}
puts $name$sep$sam$sep$exp$sep$locked$sep$lastlogon$sep$enabstr
}
user-report
Use this command to lists the users in the specified zone. The command line arguments are as follows:
| Label | Required/Optional | Description |
|---|---|---|
| -z | required | The distinguished name of the zone |
| -m | optional | Bind using the ADEdit host machine’s credentials (see bind) Note: If you use -m you do not need to enter -u |
| -u | optional | Administrator’s account name. |
| -p | optional | Administrator’s account password. Note: If you do not enter the password in the command line you will be prompted to enter it. |
#!/bin/env adedit
# This script lists the users in the zone you specify in the command line.
# On the command line use either -m or -u
package require ade_lib
proc usage {msg} {
puts {usage: -z <zoneDN> [-m] [-u <user>] [-p <password>]}
puts $msg
exit 1
}
if {[getopt argv -z zoneDN] == 0} {
usage "Missing input zone. Enter full distinguished name"
}
if {[catch {domain_from_dn $zoneDN} domain]} {
usage "Invalid input zone name. Enter full distinguished name"
}
set verbose 0
if {[getopt argv -v]} {
set verbose 1
}
if {[getopt argv -m]} {
bind -machine $domain
} else {
if {[getopt argv -u user]} {
if {[getopt argv -p password]} {
bind $domain $user $password
} else {
bind $domain $user}
} else {
bind $domain
}
}
select_zone $zoneDN
list_zone_users
GetComputers
Use this command to list all the Centrify-managed computers in the specified domain. Enter the domain name in the command line.
#!/bin/env adedit
# GetComputers
# Purpose: Retrieves a listing of all UNIX computers in all IBM SecurityZones.
package require ade_lib
puts "
This script retrieves a listing of all UNIX computers in the specified domain"
puts "and shows the zone to which it is joined"
if { $argc == 0 } {
puts "
Command format: $argv0 domain name"
exit 1
}
set domain [lindex $argv 0]
# Use lindex command because argv is a list and bind requires a string
puts "
Enter administrator name for bind command"
gets stdin admin
bind $domain $admin
foreach ZONE [get_zones $domain] {
select_zone $ZONE
foreach COMPUTER [get_zone_computers] {
puts -nonewline $COMPUTER:; puts $ZONE;
}
}
Run a Script from a Script
The following scripts illustrate the use of the Tcl source command to run the script in a specified file. In this example, the source file is setenv, which prompts the user to enter environment variables such as the domain and zone.
Note You may find repeated use of setenv to be maddening since it prompts you for all of the environment variables regardless of whether the command actually needs them. This is done for demonstration purposes only. In a production environment, you would eliminate the prompts you don’t need by tailoring setenv specifically to your environment. Feel free to remove or comment out parts when you’ve had enough.
The subsequent scripts in this section call the setenv script and then run a short script that does simple queries, such as get the child zones, get the computers in the zone, and get the groups.
setenv
This script prompts you to enter data that can be used in the calling script. This example is intended as a demonstration only. Not all of the information is relevant to the calling script. Note that this sample script assumes you are using the default deployment structure with a top-level organizational unit. If you are not using the default deployment structure, you should modify the sample script to reflect the structure you are using before testing its operation.
# Setenv file contents
# Purpose: Sets up a common environment for the following Active Directory
# tools, selecting the Active Directory Domain, binding the user, and
# defining commonly used variables.
# Other Active Directory tools:
# GetZones
# GetUsers
# GetGroups
# GetChildZones
# GetComputers
puts "
This portion of the script prompts you to enter the domain and account name for the bind command."
# If you are always using the same domain, comment out the puts and gets and use the set command instead
puts "
Enter the domain name"
gets stdin domain
# get the distinguished name for the domain.
set domaindn [dn_from_domain $domain]
puts "
Enter administrator account name for bind command"
gets stdin admin
bind $domain $admin
puts "
bind to $domain complete"
puts "
The next two prompts ask you to enter the OU and container for your zone information"
puts "
Enter the name of the Active Directory container that holds the IBM Securityzone-related data"
gets stdin zonesContainer
# If you are always using the same zone, comment out the puts and gets and use the set command instead
# set zonesContainer <Active Directory container with zones data>
puts "
Enter the name of the organizational unit that has the zone container."
gets stdin zonesContainerOU
# If you are always using the same OU for the zone container, comment out the puts and gets and use the set command instead
# set zonesContainerOU <Active Directory OU with zones container>
puts "
Enter the base organizational unit with the IBM Securitymanaged computers data"
gets stdin baseOU
# If you are always using the same base OU, comment out the puts and gets commands and use the set command instead
# set baseOU <base OU name>
puts "
The next prompt asks for the parent zone."
# If you are always using the same zone, comment out the puts and gets and use the set command instead
# set parentZone <parent zone name>
puts "
Enter the parent zone name"
gets stdin parentZone
GetZones
Use this script to get a list of all the zones in a domain.
#!/bin/env adedit
# GetZones
# Purpose: Performs a recursive listing of all IBM Securityzones in the specified
# domain
package require ade_lib
source setenv
puts "
This script retrieves a recursive listing of all IBM Securityzones in the $domain domain"
puts "
The Active Directory folder with the IBM Securityzone data is named $zonesContainer"
puts "
That container is in organizational unit $zonesContainerOU"
puts "
The parent zone is $parentZone"
foreach ZONE [get_zones $domain] {
puts $ZONE;
}
GetUsers
Use this script to get a list of all users in a zone.
# GetUsers
# Purpose: Operates on a recursive listing of all UNIX users in all
# IBM SecurityZones, and retrieves the administered UNIX attribute values
# for each user object in each zone.
package require ade_lib
puts "
This script retrieves the UNIX attributes for each user in each zone in the specified domain"
source setenv
foreach ZONE [get_zones $domain] {
select_zone $ZONE
foreach USER [get_zone_users] {
save_zone_user $USER
puts -nonewline "[get_zone_user_field uname]:[gzuf uid]:[gzuf gid]:[gzuf gecos]:[gzuf home]:[gzuf shell]"; puts :$USER:$ZONE
}
}
GetGroups
Use this script to get the UNIX group attribute values for the groups in the managed computers.
#!/usr/bin/env adedit
# GetGroups
# Purpose: Retrieves the UNIX group attribute values for each UNIX
# group administered in the parent zone specified in setenv.
# To select a different zone, change the DN in the select_zone command
package require ade_lib
puts "
This script retrieves the group attribute values for each UNIX group in the specified parent zone"
source setenv
select_zone "CN=$parentZone,CN=$zonesContainer,OU=$zonesContainerOU,$domaindn"
foreach GROUP [get_zone_groups] {
select_zone_group $GROUP
puts -nonewline "[get_zone_group_field name]:[gzgf gid]"; puts :$GROUP
}
GetChildZones
Use this command to get a list of the child zones for the specified parent.
#!/bin/env adedit
# # GetChildZones
# Purpose: Retrieves a recursive listing of all new hierarchical IBM Securitychild
# zones administered underneath the parent zone specified in setenv
#
package require ade_lib
source setenv
puts "
This script retrieves a recursive listing of all child zones in $parentZone"
puts "
The Active Directory folder with the IBM Securityzone information is $zonesContainer"
select_zone "CN=$parentZone,CN=$zonesContainer,OU=$zonesContainerOU,$domaindn"
foreach ZONE [get_child_zones -tree] {
puts $ZONE;
}