[title]: # (Hierarchical Zones (5.x)) [tags]: # (windows api) [priority]: # (1)
Hierarchical IBM Security Zones (5.x)
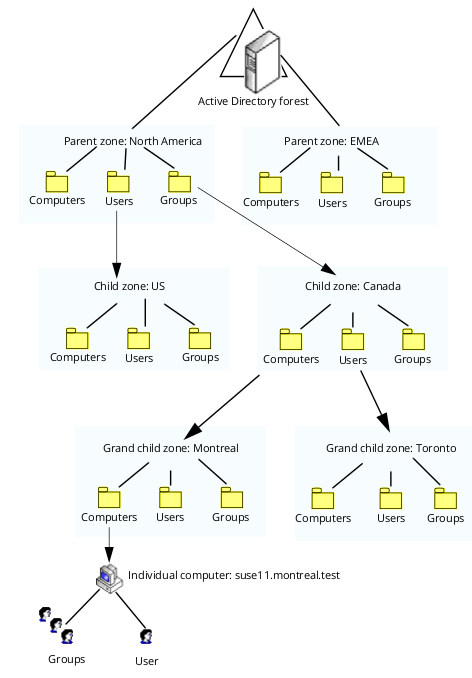
In hierarchical IBM Security zones, each zone is part of a tree of zones and Active Directory containers for users, groups, and computers. The effective profile for each user, group, or computer in a hierarchical zone is determined by attributes defined in the current zone, in parent zones, and in zone default values, with values lower in the hierarchy taking priority. In addition, individual computers can have computer-level overrides of users, groups, and role assignments. When you assign computer-level overrides for a specific computer, internally IBM Security creates a computer-specific zone that contains the users, groups, and computer role assignments that are specific to only that one computer. Computer zones are not exposed as zones in Access Manager, but are treated as end nodes in the zone hierarchy.
The following figure illustrates the basic structure used for hierarchical IBM Security zones. Attributes are inherited from higher-level to lower-level zones as indicated by the arrows in the figure.
In hierarchical zones, because User and Zone objects inherit from their parent
zones, it is not necessary for every hierarchical level to have a full set of
attributes. If a user profile is incomplete after inheriting all the ancestor's
attributes, missing mandatory attributes are filled from defaults. Missing UIDs
are generated from an RID-based algorithm.
See Classic IBM Security zones (2.x, 3.x, 4.x) for a general description of the way IBM Security attributes are stored in Active Directory.