Creating a UNIX Administrator Role
Now that you have verified an Active Directory user can access the Linux or UNIX computer you are using for the evaluation, you will see to how to create users that have elevated privileges and how you can limit the use of those privileges to specific computers.
To illustrate this scenario, you will create a UNIX administrator role that grants root privileges for the computers in a zone without requiring users to know the root password. Instead, users who are assigned the UNIX administrator role use their Active Directory credentials.
You can use the same steps to define roles with different and more granular rights. For example, you will follow similar steps to create an Apache administrator role that can only perform a limited set of tasks on computers in a child zone.
At the end of this section, you will have two accounts with UNIX Login privileges: one of which has only standard user privileges, the other account has full administrative privileges.
To create a new Active Directory user and group with administrative access
-
Open Active Directory Users and Computers and create a new User object.
-
Fill in the First, Last, and the User logon name fields.
-
Type and confirm a password and select the Password never expires option.
-
Acknowledge the warning, click Next, then click Finish.
-
-
Open Active Directory Users and Computers and create a new Group object in the UNIX Groups organizational unit.
-
For the Group name, enter EnterpriseUnixAdmins.
-
Select Global as the scope for the group and Security for the type of group, then click OK.
-
-
Add the administrative user to the EnterpriseUnixAdmins group.
-
Select the user you created in Step 1, right-click and select Add to a group.
-
Select the EnterpriseUnixAdmins group, then click OK.
-
-
Provision a UNIX profile for the new user using Access Manager.
-
Expand the Zones node and select the Headquarters, right-click, then select Add User.
-
Select the user you created for UNIX administration.
-
Select Define user UNIX profile only and deselect Assign roles.
-
Accept the default values for all profile properties.
-
Review your selections, click Next, then click Finish.
-
Defining a Command Right and a New Role
You are now ready to define a new privileged command right that uses the asterisk (*) wild card to give the user the equivalent of all commands, all paths, and all hosts in the sudoers file. In a production deployment, you would define more specific sets of privileged commands and run them using accounts with no restricted access than the root user.
To create new UNIX right definition for the administrative role
-
Create a new privileged command using Access Manager.
-
Expand the Authorization node under the Headquarters zone, then expand UNIX Right Definitions and select Commands.
-
Right-click then select New Command. For this example, you will only set information on the General tab.
-
Type a command name and description, for example root_any_command and All commands, all paths, all hosts.
-
Type an asterisk (*) in the Command field to match all commands.
-
Leave the default setting for Glob expressions.
-
Select the Specific path options and type an asterisk (*) to match all command paths, then click OK.
-
You now have a root_any_command that grants privileges to run any command in your role definitions. In the next steps, you create a role that will give members of the EnterpriseUnixAdmins group the root_any_command privileges.
To create and assign the UNIX administrators role
-
Create a new role definition using Access Manager.
-
Expand the Authorization node under the Headquarters zone, select Role Definitions, right-click, then select Add Role.
-
Type a role name (UnixAdminRights) and a description (Set of rights for UNIX administrators) for the new role.
-
Click the System Rights tab and select all of the UNIX rights and the Rescue right.
-
Click the Audit tab and select Audit if possible, then click OK.
-
-
Add the root_any_command and several default rights to the new role.
-
Select the UnixAdminRights role, right-click, then select Add Right.
-
Use CTRL-click to select rights, including login-all, secure shell (ssh, sshd, and dzsshall) rights, and the root_any_command right you just created, then click OK.
-
-
Assign the UnixAdminRights role to the enterprise UNIX administrators group using Access Manager.
-
Expand the Authorization node under the Headquarters zone, select Role Assignments, right-click, then select Assign Role.
-
Select the UnixAdminRights role and click OK.
-
Click Add AD Account.
-
Change the object to Find from User to Group, then search for and select the EnterpriseUnixAdmins group, then click OK.
-
Click OK to complete the role assignment.
-
Verifying Administrative Privileges
You now have two role assignments—Login Users and EnterpriseUnixAdmins—in the zone. Any Active Directory user you add to the Login Users group and provision a UNIX profile for will have access rights but no administrative privileges on the computers in the zone. Any Active Directory users you add to the EnterpriseUnixAdmins group and provision a UNIX profile for will be able to run any command with root-level permissions using their Active Directory credentials.
The Active Directory user you added to the EnterpriseUnixAdmins group can now log on and run privileged commands on the UNIX or Linux computers you are using for evaluation.
To verify the user can run privileged commands using Active Directory credentials
-
Log on to the Linux or UNIX computer using the Active Directory logon name and password you created for the UNIX administrator.
-
Open a terminal on the Linux or UNIX computer.
-
Run a command that requires root-level privileges.
For examples, run the dzinfo command to view the rights and roles for the UNIX Login user you createdAdding and provisioning an evaluation user and group.
dzinfo user_name
Because you are logged on as the Active Directory user and not invoking the command using your role assignment, the command displays an error messageindicating that you are not allowed to view authorization information for another user.
-
Re-run the command using your role assignment by typing dzdo before the command.
dzdo dzinfo user_name
The command runs successfully and returns information about the evaluation user similar to this partial output.
User: lois.lane
Forced into restricted environment: NoRole Name Avail Restricted Env
--------------- ----- --------------
UNIXLogin/Headquarters Yes None
Effective rights:
Password login
Non password login
Allow normal shellAudit level:
AuditIfPossible
Viewing Effective Rights
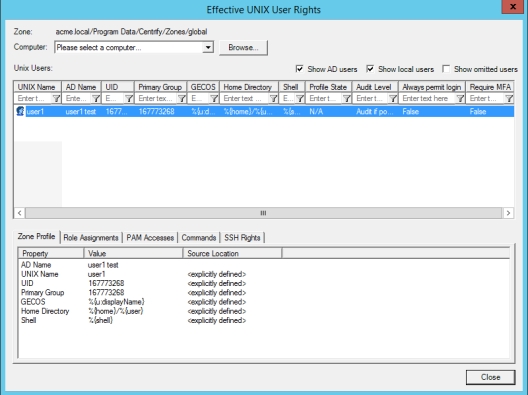
Often, you need to see which users have what privileges in a zone. Access Manager provides you a single view of all of the effective users in a zone and lets you tab through their account properties.
To view effective rights for Linux and UNIX users
-
Open Access Manager.
-
Expand Zones, right-click your parent zone name, then select Show Effective UNIX User Rights.
For example, the following illustrates the effective users in the evaluation zone.
-
Select a user, then click the tabs to see details about that user’s profile, role assignments and UNIX rights.