How Authentication Works for Windows
This section introduces core concepts and features that you should be familiar with before starting an evaluation of IBM Security software for managing Windows computers.
Providing Access Control and Accountability
In many organizations, most computer users are given very restricted access privileges to minimize the exposure of sensitive services and data to possible compromise. However, there are often a few applications, procedures, or services that require enhanced privileges and to which these users need access. For example, a user might occasionally have to install software or run a restricted internal application. For this purpose, these organizations often provide these users with login information for accounts with enhanced privileges. Unfortunately, this policy substantially undermines security, because there’s no way to tell—even on an audited system—who actually logged on to these accounts, and once logged on, a malicious user is not restricted to the procedures for which he was given the login information in the first place.
IBM Security solves this problem by enabling you to assign roles that give a user access to only those services or applications and restricted access privileges only when the user needs them.
For Windows computers, IBM Security provides three main services: access control, privilege management, and auditing. These services can be used together or independently.
To provide access control, privilege management, and auditing for Windows computers, IBM Security relies on the following:
- Authentication Service and Privilege Elevation
Service features enable you to define access control privileges, create
roles composed of a set of privileges, and assign users or groups to those
roles. You can also use zone technology to limit the scope of a
role to limited sets of computers. You can, also, configure roles with start
and expiration dates or to be active on specific days of the week and hours
of the day.
-
Audit & Monitoring Service enables you to collect and store an
audit trail of user activity and provides a console for searching and
replaying captured sessions.
-
Agent for Windows enables you to deploy access and auditing
features on the Windows computers you want to manage.
You can use Privilege Elevation Service without auditing if you aren’t interested in collecting and storing information about session activities. You can also deploy Verify Privilege Server Suite without access and privilege management features if you are only interested in auditing activity on Windows computers. However, the real value of IBM Security software for Windows computers comes from using the services together as an integrated solution for managing elevated privileges and ensuring regulatory compliance across all platforms in your organization. That way you can restrict access to only those instances when elevated permissions are absolutely necessary, and audit only user activity that merits auditing.
Organizing Computers and Access Rights
This guide is intended to help you evaluate how you can use IBM Security software to manage access and administrative privileges for Windows computers and applications. However, IBM Security also enables you to include UNIX, Linux, and Mac OS X computers in Active Directory, providing you with a single repository for all managed computers, users, privileges, and roles. IBM Security enables this cross-platform integration through the use of Zones.
A zone is a logical object that you create using Access Manager. You use the zone to organize computers, rights, and roles into groups. In each group, you can define different access rights, different role availability rules, and different role assignments. You can create the zones in a hierarchy of parent and child zones, so that rights and roles can inherited or zone-specific.
As part of the evaluation, you will create a zone for the Windows computers, define access rights that are specifically for Windows computers, create roles that include those access rights, and assign roles to users and groups.
Restricting Access to Administrative Privileges
By defining roles with specific access permissions, you can use Access Manager to specify the conditions under which users can perform privileged operations. A user logs on to the Windows computer with his or her normal, restricted login, and then selects the role they need to perform a privileged operation only when that access is needed. You can restrict a role or desktop to certain times or days of the week, and you can set a beginning and expiration date for the access. You can set any role or desktop to require auditing, so that the user cannot use the role or desktop unless it is being audited.
Access Manager provides three kinds of Windows access rights. For Windows computers, these specialized access rights are:
-
Desktop access rights enable you to create additional working
environments and run any application in that desktop as a member of Active
Directory or built-in group.
-
Application access rights enable you to run a specific local application
as another user or as a member of an Active Directory or built-in group.
This access right is similar to the standard Run as menu option, except
that someone assigned a role with this right doesn’t need to know the
privileged user’s password to use it.
-
Network access rights enable you to connect to a remote computer as
another user or as a member of an Active Directory or built-in group to
perform operations, such as start and stop services, that require
administrative privileges on the remote computer.
You configure these access rights using the Access Manager console. The rights are enforced through an Agent for Windows installed on each computer you want to manage.
Auditing User Activity on a Managed Computer
When you install the Agent for Windows on a computer, you have the option to enable access management, auditing, or both. If you enable auditing features, the agent can capture detailed information about user activity and all of the events that occurred in each user session on the managed computer. The user activity captured includes an audit trail of the actions a user has taken and a video record of everything displayed on the screen. For users who have privileged access to computers and applications, the audit and monitoring service helps ensure accountability and improve regulatory compliance. By recording user sessions, you can see exactly who had access to which computers and what they did, including any changes they made to key files or configurations.
The audit and monitoring service collects user activity as it occurs. The recorded activity is transferred to a Microsoft SQL Server database so that it is available for querying and playback. You can search the stored user sessions to look for policy violations, user errors, or malicious activity.
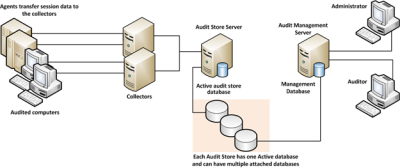
To ensure scalability and enterprise readiness, the auditing infrastructure consists of multiple components called a audit and monitoring service installation:
-
Audited computers are the computers on which you want to monitor
activity. To be audited, the computer must have the Agent for
Windows installed with auditing enabled and be joined to an Active Directory
domain.
-
One or more collectors receive the captured activity from the agents on
audited computers and forward it to an audit store database.
-
An audit store defines a scope, such as an Active Directory site or a
subnet, and one or more databases that store captured activity and audit
trail records from the collectors and store it for querying.
-
A management database keeps track of all the agents, collectors, and
audit stores that make up a single DirectAudit installation.
-
Consoles enable administrators to configure and manage all of the
audit-related components and auditors to query and review user sessions.
When you enable auditing on a computer with the Agent for Windows, the agent captures user activity on that computer and forwards it to a collector computer. If no collectors are available, the agent caches the session data locally and transfers it to a collector later. The collector sends the data to an audit store database. When administrators or auditors want to review the captured data, they use the Audit Analyzer to search for and play back the session. The Audit Analyzer connects to the management database which retrieves the data from the appropriate audit store. The administrator can control the audit data available to any specific user or group through auditor roles that limit audit access rights and privileges.
The following figure illustrates the basic architecture and workflow in a small scale installation.