Setting up the Evaluation Environment
This section describes how to prepare for an evaluation of Verify Privilege Server Suite on a Windows computer. It includes instructions for installing Verify Privilege Server Suite components and the Agent for Windows to enable a full evaluation of access control, privilege management, and auditing on Windows computers.
Installing and configuring Verify Privilege Server Suite requires about a half hour. If you need to install Microsoft SQL Server Express with Advanced Features, which is also included in the package, add another 10 to 15 minutes to the setup.
Preview of Tasks
You will perform the following tasks to set up the evaluation environment. You should perform the tasks in the order shown to prepare your environment for a meaningful evaluation that demonstrates the key features of the solution for Windows computers.
-
Ensure you have at least one Active Directory domain controller and one Windows domain computer—also referred to as the Windows client computer.
See Basic Requirements for the Evaluation for details about the system requirements for these computers.
-
Acquire IBM Security software for the Windows client computer.
See Downloading IBM Security Software for Windows Evaluations for details about acquiring IBM Security software.
-
On the Active Directory domain controller, create an Active Directory user and group to be used in the evaluation.
See Creating an Active Directory User and Group for details about this procedure.
-
Install Access Manager and administrative tools on the Windows client computer.
See Preparing to Evaluate Access Management for details about installing these features.
-
Use Access Manager to configure Active Directory on the domain controller.
See Configuring Active Directory Using Access Manager for details about configuring Active Directory from Access Manager.
-
Use Access Manager to create a zone.
See Creating the First Zone for details about creating a zone.
-
Use Access Manager to assign the Windows Login role to your Active Directory account.
See Assigning Yourself the Default Windows Login Role for details about this procedure.
-
If you are evaluating auditing features, you need access to an instance of Microsoft SQL Server and an audit installation, which consists of several auditing-specific components.
See Identifying a Microsoft SQL Server Instance for details about installing a SQL Server Express instance for demonstration purposes.
See Preparing to Evaluate Auditing for details about installing audit components.
-
Install the Agent for Windows on the Windows client computer.
See Installing the Agent for Windows for details about this procedure.
Basic Requirements for the Evaluation
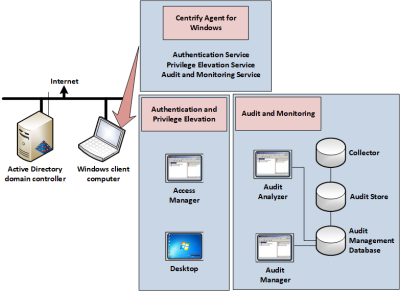
The installation procedures described in this guide are based upon a minimal configuration with one Windows IBM Security-managed computer (the Windows client computer) and one Windows Active Directory domain controller, as illustrated in the following figure.
You can add more Windows computers to the configuration to expand the scenario or to make the evaluation more consistent with a production deployment.
Preparing an Active Directory Domain Controller
You must have an Active Directory domain controller to use in this evaluation. You should also have a properly configured Domain Name Service that enables the computers used in the evaluation to communicate.
For details about supported platforms, please consult the release notes.
In the configuration illustrated in the previous topic, no software is installed on the domain controller. However, because this is just an evaluation environment, you could install all of the software on the domain controller. In a production environment it is not recommended to install this software on domain controllers.
Selecting a Windows Domain Computer
The Windows client computer that you use for the evaluation should have a supported Windows operating system and minimum system requirements.
| For this | You need this |
|---|---|
| Windows operating system | Windows 7 or later or a Windows server platform. Please consult the release notes for supported platform versions. |
| .NET Framework | .NET Framework 4.6.2 or later If .NET is not installed, the setup program will install it for you. |
| CPU speed | Minimum 2 GHZ |
| RAM | 4 GB |
| Disk space | 20 GB free space |
Desktop rights can be used on Windows servers and workstations that have a traditional Windows desktop. If the computer you are using is running Windows Server 2012 or 2012 R2, Windows does not provide access to applications natively when you switch from the default desktop to a privileged desktop due to changes to the underlying interfaces and supported features within the operating system. To enable access to applications on computers running these versions of Windows, the Agent for Windows provides a custom start menu. The IBM Security start menu allows you to open and run applications as you would on Windows 7 or Windows Server 2008 R2. The IBM Security start menu is installed on the left side of the taskbar and displays the IBM Security logo. This start menu is only available if you are using a role with IBM Security desktop rights and cannot be modified.
IBM Security also recommends that you install the Microsoft Windows Server
Administration Tools Pack on the computer on where you install Access Manager.
The Administration Tools Pack includes the Active Directory Users and Computers
utility—dsa.msc—used in many of the exercises.
If you are using the recommended configuration with a separate Windows client computer that is not the domain controller, be sure that the Windows client computer is joined to the Active Directory domain.
Downloading IBM Security Software for Windows Evaluations
You can go to the this website to sign up for a free trial. Once you're signed up with an account, you can download the software.
To register for a free trial:
- Navigate to https://www.delinea.com/free-trial/.
-
Enter your contact and company information, click the checkbox to indicate
that you agree to the terms of use and privacy policy, and then click
Start My Trial.
You will receive an email with the next steps in downloading your free trial.
Downloading Verify Privilege Server Suite Software for Windows Evaluations
You can download all of the components for Verify Privilege Server Suite from the IBM Security website to your Windows computer. Before you begin, be sure you have the email address and password you used to register for your trial.
To download the Windows software for Verify Privilege Server Suite:
-
Open a browser on the Windows computer you plan to use for the evaluation and go to https://www.delinea.com.
-
In the upper area of the web page, click Login.
-
Enter your email address and your account password, then click Login.
-
Go to Support > Downloads.
-
Select Zero Trust Privileges - Enterprise to locate the latest software bundles.
-
Next to the latest version for 64-bit Windows systems, click either the ISO or ZIP button to download the software in that format.
The latest version of the Windows software bundle is called Verify Privilege Server Suite.
-
Close the window when the download is complete.
Creating an Active Directory User and Group
Evaluation scenarios covered in this guide require an Active Directory user with normal user privileges to demonstrate different features. For example, you will create access rights that grant elevated privileges to a role and assign this user to the role to use those rights.
To prepare for the evaluation scenarios:
-
On the Active Directory domain controller, open Active Directory Users and Computers.
For example, create the user
amy.adamsto represent a domain user with a valid logon account. -
Select Action > New > User and follow the prompts to create a new Active Directory user.
-
Select Action > New > Group and follow the prompts to create a new Active Directory group.
For example, create the group
Eval Groupto represent a typical Active Directory security group to which you would assign a role. -
Right-click the user name and select Add to a group to add the new user to the new group.
You might also want to add your own Windows account to the new group. Adding your own account to the Evaluation group makes it easier to demonstrate some features, such as assigning roles to group members.
Preparing to Evaluate Access Management
If you are evaluating access control and privilege management features, you must install the administrative tools on the Windows client computer to prepare for the evaluation. Later, you will also install the Agent for Windows on the Windows client computer as described in Installing the Agent for Windows.
To install Access Manager from the installer:
-
Log on to the Windows client computer using a Windows account that is a member of the Domain Administrator domain security group in the domain where you will install Verify Privilege Server Suite.
-
From the IBM Security CD or directory that has IBM Security software, open autorun.
-
On the Getting Started page, click Authentication & Privilege to start the setup program for Authentication Service and Privilege Elevation Service.
-
Follow the prompts displayed and select Administration as the components to install.
For a Windows-only evaluation, none of the Utilities components are applicable.
-
Accept the defaults for the remaining selections, then click Finish to close the setup program.
Configuring Active Directory Using Access Manager
The setup program adds shortcuts for selected components to your desktop to give you immediate access to the consoles you will use. Before you can use Access Manager to create zones, define access rights and roles, and assign roles to users and groups, however, you use it to run a Setup Wizard that prepares the Active Directory forest with parent containers for licenses and zones.
To use the Setup Wizard to configure Active Directory:
-
From the desktop, open Access Manager.
-
Select Use currently connected user credentials to use your current log on account, then click Next.
-
Select Generate recommended deployment structure and Generate default deployment structure, then click Next.
-
Click Browse to select the container you would like to use for the deployment structure.
You can select any domain in the forest, including the forest root domain.
-
Select a location for installing license keys in Active Directory, then click Next.
The Setup Wizard displays information about the Read permissions that must be granted on the container. Click Yes to continue.
-
Type, copy and paste, or import the license key you received, click Add, then click Next.
-
Click Next to use the default container for zones.
-
Click Next to skip the following options:
- Grant computer accounts permission to update their own account information.
- Register the administrative notification handler.
- Activation of profile property pages.
-
Review the summary, click Next, then click Finish.
The wizard opens the Access Manager console. For reference, the user account under which you are logged in displays in the main panel just below Access Manager.
Creating the First Zone
In this section, you create a zone for the Windows client computer. After you create the zone, you can start creating access rights, defining roles, and assigning roles to Active Directory users and groups.
To create a new zone:
-
In Access Manager, click Create Zone.
-
Type a name and description for the zone, for example Headquarters, then click Next to accept the defaults for the other fields.
-
Click Finish.
You now have one parent zone in Access Manager. Expand Access Manager > Zones to view your new zone in the console.
Assigning Yourself the Default Windows Login Role
After you install the Agent for Windows, you must be assigned to a role that allows you to log on. To finish the preparation of the evaluation environment for access control and privilege management, you are going to assign a role with the log in privilege to your Active Directory account. The Windows Login role is a predefined role that grants permission to log on locally and connect remotely for IBM Security-managed Windows computers.
To assign the Windows Login role to your account:
-
In Access Manager, expand Zones and select the zone you created in Creating the First Zone.
-
Right-click the zone, and select Add User.
-
Select Active Directory user and click Next.
-
Type the path to your account or click Browse to search for and select your Active Directory user account, then click Next.
For example, click Browse and type all or part of the name, then click Find Now. You can then select your account name in the list of results and click OK.
-
Deselect Define user UNIX profile and make sure Assign roles is selected, then click Next.
-
Click Add, select the predefined Windows Login role, and click OK.
-
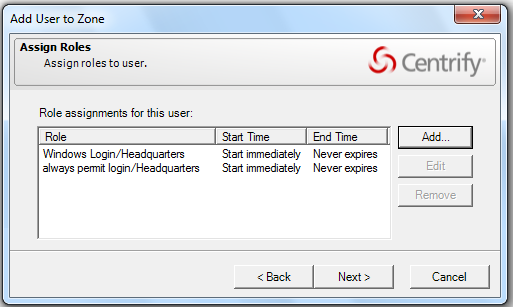
Check the role assignment start and end times for your account are set to Start immediately and Never expire, then click OK.
-
Repeat Step 6 and Step 7 to add the Rescue - always permit login role.
Your Add User to Zone window should show the following roles:
-
Click Next, then click Finish.
If you are evaluating auditing features, go on to Preparing to Evaluate Auditing. If you are only evaluating access-related features, skip to Installing the Agent for Windows.
Preparing to Evaluate Auditing
If you are evaluating access and auditing features or only auditing, there are several components that make up the auditing infrastructure. For evaluation, you can install all of the components on the same computer.
Identifying a Microsoft SQL Server Instance
If you are evaluating both access and auditing features or only auditing, you must have at least one Microsoft SQL Server instance for storing audit-related information.
For evaluation purposes, you can use an existing Microsoft SQL Server database instance to which you have administrative access or automatically install and configure an instance of Microsoft SQL Server Express with Advanced features directly from the Audit Configuration Wizard.
You should only use Microsoft SQL Server Express for evaluation and testing. You should not use Microsoft SQL Server Express for a production environment.
Installing the Auditing Components
In this section, you run the setup program to install the auditing and monitoring components, including the Audit Manager and Audit Analyzer consoles, on the Windows client computer.
To install the Audit & Monitoring Service from the installer:
-
Log on to the Windows client computer using a domain account with administrative privileges, such as
DEMO\\administrator. Do not log on as a local user. -
From the IBM Security CD or directory that has IBM Security software, open autorun.
-
On the Getting Started page, click Audit & Monitor to start the setup program for the audit and monitoring service.
-
At the Welcome page, click Next.
-
Review the terms of the license agreement, click I accept the terms in the license agreement, then click Next.
-
Select Administration and Services to install both Audit Manager and Audit Analyzer, then click Next.
-
Accept the defaults for the remaining selections and confirm that the Launch Configuration Wizard option is selected, then click Finish to close the setup program.
Note If the Launch Audit Configuration Wizard option is not selectable, a possible cause is that you are logged on to the Windows client computer as a local user (for example, local administrator) rather than as a user with domain administrative privileges. In this scenario, select Start > Switch user and log on as a Windows domain user with administrative privileges (for example,
DEMO\\administrator). Then launch Audit Manager from the desktop icon, and select Action > New Installation to start the audit configuration wizard. -
In the Welcome page for the audit configuration wizard, click Next.
-
Select Create a new installation and type a name for your installation, then click Next to capture audit trail events without recording video of an audited user’s desktop activity.
Audit trail events provide a summary of user activity, for example, when users log on and off, open and close applications, and use role assignments with elevated rights. If you want to be able to review what was displayed on the screen during an audited user’s session, you can select Enable video capture auditing of user activity. This option increases the database storage required for auditing.
-
Select Install a new SQL Server Express instance on this computer and specify the instance name, then click Next.
-
Verify the default path to the Microsoft SQL Server Express setup program, the disk space requirements, and the location for the files, then clickNext.
If an incompatible instance of SQL Server Express is already installed, the wizard displays an error message instructing you to uninstall that instance. Use the Windows control panel to uninstall the incompatible instance of SQL Server Express, and then try the SQL Server Express installation from the wizard again.
- Review the summary, then click Finish.
The audit configuration wizard automatically configures the audit store scope, audit store database, and a collector on the local computer. After the auditing infrastructure is in place, you can install the Agent for Windows and join the computer to the zone you created.
Installing the Agent for Windows
You are now ready to install the Agent for Windows on the client computer to begin the evaluation. In a production environment, you would install the agent on all of the Windows computers in the domain that you want to manage or audit.
The following instructions assume you are still logged in with your
administrator account. Be sure that this account has at least the Windows Login
and Rescue - always permit login roles assigned as described in Assigning Yourself the Default Windows Login Role to ensure you can log on after the agent is
installed. If the account you are using to install the agent does not have the
Windows Login role assigned, the agent configuration wizard will allow you to
assign the Windows Login role to the domain administrators (Domain Admins) group
when you join a zone.
To install the Agent for Windows using the setup program:
-
Insert the IBM Security distribution CD into the computer on which you wish to install the agent or browse to the location where you have saved downloaded IBM Security files.
-
On the Getting Started page, click Agent to start the setup program for the agent.
If the Getting Started page is not displayed, open the autorun.exe file to start the software installation.
-
If a previous version of the agent is installed, click Yes when prompted to upgrade the Agent for Windows.
-
At the Welcome page, click Next.
-
Review the terms of the license agreement, click I accept the terms in the License Agreement, then click Next.
-
Accept the default location for installing components, or click Change to select a different location, then click Next.
-
In the Ready to install Agent for Windows page, click Install.
-
Click Finish to complete the installation and start the agent configuration panel.
You must restart the computer after you configure the Privilege Elevation Service. When prompted, click Yes to restart the computer immediately.
After you restart the computer, log on with your administrator account. Left-click on the IBM Security icon on your taskbar to confirm that you are viewing your default desktop. In the next chapter, you will see how to configure access rights and roles and how to select from roles you are assigned.
Configuring the Agent
By default, when you click Finish, the setup program opens the agent configuration panel. In the agent configuration panel, you can enable the agent to connect to IBM Security services that are installed on the main administrative computer as described in Installing the Agent for Windows. After a service is enabled, you can use the agent configuration panel to configure settings that define how the agent will interact with each service.
The first time the agent configuration panel opens, it does not display any services for you to enable. Services display in the agent configuration panel only after you manually instruct the configuration panel to check for services and display those that are eligible to be enabled.
Only services that are installed and configured as required are eligible to be enabled. For example, if you installed the Privilege Elevation Service earlier (as described in Preparing to Evaluate Access Management ) but did not create a zone, the Privilege Elevation Service does not display on the list of services that you can enable.
To enable services using the agent configuration panel:
-
If the agent configuration panel is not open, open it by clicking Agent Configuration in the list of applications in the Windows Start menu.
-
In the agent configuration control panel, click Add service.
All services that are available to be enabled are displayed.
-
In the list of services, highlight a service and click OK.
-
Provide additional information about the service that you are enabling:
-
Audit & Monitoring Service:
In the Select an Audit Installation page, select an audit store from the list of available audit stores. Click Next, and the computer is connected to the audit store.
-
Identity Platform Settings:
- In the Connect to Identity Platform page, type the URL of the
identity platform instance to connect to, or select an instance from
the list of registered platform instances in the forest. Click
Next. - In the Multi-factor authentication for Windows Login page, ensure
that the check box to enable multi-factor authentication is
selected. Next, use the All Active Directory accounts button or
Accounts below button to specify which Active Directory accounts
are enabled for multi-factor authentication login. If you select
Account below, use the Add and Remove buttons to select
accounts. Click Next when you are finished.
- In the Connect to Identity Platform page, type the URL of the
-
Privilege Elevation Service:
-
In the Join to a zone page, type a zone or select a zone from the list of available zones. You can also choose to select the option to retrieve the zone data before the computer restarts. This option can be helpful in situations where you might lose connection to the domain after restarting, such as when you're using a VPN connection.
Click Next, and the computer is joined to the zone.
-
After the computer is joined to a zone, you must reboot the computer to activate all privilege elevation service features on the computer.
If the zone that you select is already configured with a Privileged Access Service tenant, the message Identity Platform enabled displays after the computer joins the zone. In this situation, the instance is managed by the zone, and is shown as read-only.
-
-
-
To add additional services, click Add service and repeat the preceding steps.
When you are done, the services that you enabled are shown in the Enabled services section of the agent configuration panel.
-
If necessary, continue to configure services after their initial configuration during enablement as described in these sections:
Configuring Agent Settings for Audit and Monitoring Service
If you want to reconfigure agent settings for auditing on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the service), you can open the agent configuration panel manually and configure the agent as described in this section.
To configure agent settings for audit and monitoring service:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration panel opens, and displays the services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Audit & Monitoring Service, and then click Settings.
-
In the General tab, click Configure.
-
Select the maximum color quality for recorded sessions, then click Next.
See Selecting the Maximum Color Quality for Recorded Sessions for more information on the configuration of this setting.
-
Specify the offline data location and the maximum percentage of disk that the offline data file should be allowed to occupy, then click Next.
See Configuring Agent Settings for Offline Audit and Monitoring Service Storage for more information on the configuration of this setting.
-
Select the installation that the agent belongs to, then click Next.
-
Review your settings, then click Next.
-
Click Finish.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see the Administrator’s Guide for Windows.
Selecting the Maximum Color Quality for Recorded Sessions
Because auditing Windows computers captures user activity as video, you can configure the color depth of the sessions to control the size of data that must be transferred over the network and stored in the database. A higher color depth increases the CPU overhead on audited computers but improves resolution when the session is played back. A lower color depth decreases network traffic and database storage requirements, but reduces the resolution of recorded sessions.
The default color quality is low (8-bit).
Configuring Agent Settings for Offline Audit and Monitoring Service Storage
The “Maximum size of the offline data file” setting defines the minimum percentage of disk space that should be available, if needed, for audit and monitoring service. It is intended to prevent audited computers from running out of disk space if the agent is sending data to its offline data storage location because no collectors are available.
For example, if you set the threshold to 10%, auditing will continue while spooling data to the offline file location as long as there is a least 10% of available disk space on the spool partition. When the available disk space reaches the threshold, auditing will stop until a collector is available.
The agent checks the spool disk space by periodically running a background process. By default, the background process runs every 15 seconds. Because of the delay between background checks, it is possible for the actual disk space available to fall below the threshold setting. If this were to occur, auditing would stop at the next interval. You can configure the interval for the background process to run by editing the HKLM\Software\Centrify\DirectAudit\Agent\DiskCheckInterval registry setting.
Configuring Agent Settings for the Identity Platform
If you want to reconfigure agent settings for Privileged Access Service on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the service), you can open the agent configuration panel manually and configure the agent as described in this section.
To configure agent settings for the Identity Platform:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration panel opens, and displays the services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Identity Platform, and then click Settings.
-
In the General tab, review the Status field in the Features area:
- If the status is Enabled, the computer is not joined to a zone, and
you can configure all Identity Platform settings that are shown in the
General tab. - If the status is Enabled per zone settings, the computer is joined
to a zone, and most Identity Platform settings are based on the zone
configuration. In this situation, the Browse and Details buttons
in the General tab are disabled, because those features are controlled
by the zone configuration. The only configuration that you can perform
in the General tab is to change the proxy server settings.
- If the status is Enabled, the computer is not joined to a zone, and
-
To change proxy server settings:
- Click Change.
- Specify a new proxy server address.
- Click OK.
-
To change to a different Identity Platform instance (only configurable if the computer is not joined to a zone):
- Click Browse.
- Select an instance from the list of registered platform instances in the forest.
- Click OK.
-
To specify which Active Directory accounts require multi-factor authentication (only configurable if the computer is not joined to a zone):
- Click Details.
- Use the All Active Directory accounts button or Accounts below
button to specify which Active Directory accounts are enabled for
multi-factor authentication login. If you select Account below, use
the Add and Remove buttons to select accounts. - Click OK.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see the Multi-factor Authentication Quick Start Guide.
Configuring Agent Settings for Privilege Elevation
If you want to reconfigure agent settings for privilege elevation on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the privilege elevation service), you can open the agent configuration panel manually and configure the agent as described in this section.
To configure agent settings for privilege elevation:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration control panel opens, and displays the services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Privilege Elevation Service, and then click Settings.
-
In the General tab, click Change.
-
In Change the zone for this computer, click Browse.
-
Click Find Now to search for an appropriate zone for the agent.
-
Select a zone from the list of search results, then click OK.
-
Click OK to use the zone you selected.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see the Administrator’s Guide for Windows.