Permissions Required for Administrative Tasks
This chapter describes the permissions required to perform administrative tasks that affect IBM-specific objects in Active Directory. You can set these permissions manually for individual users and groups who manage IBM zones in Active Directory. However, setting permissions manually can be time-consuming and error-prone. In most cases, you should use the Zone Delegation Wizard to authorize users to perform specific tasks.
At a minimum, all Access Manager actions require users to have generic Read permission. This permission is typically granted to all Authenticated Users by default.
Because Authenticated Users have read access, they can run reports in the Report Center. No additional rights need to be granted to enable users to run reports.
How Permissions Are Set
Access Manager requires specific rights for administrators to work with objects such as UNIX users, groups, and computers within Active Directory. As part of your deployment planning process, you should review the rights required to set up and manage IBM specific objects and be familiar with how to manually assign rights for managing IBM objects, if needed.
Built-in Windows groups, such as Domain Admins and Domain Users, have default permissions, which might be customized for your organization. In general, the administrators for the forest root domain have broad authority to set permissions for all other users and groups, including the administrators of other domains. Therefore, whether you can modify the permissions for specific users and groups within your Active Directory environment will depend on the policies of your organization.
If you have the appropriate authority, there are several ways you can access, verify, and modify the permissions assigned to specific users and groups.
For example, you can view and modify permissions in the following ways:
-
Use ADSI Edit to directly modify any Active Directory attributes.
-
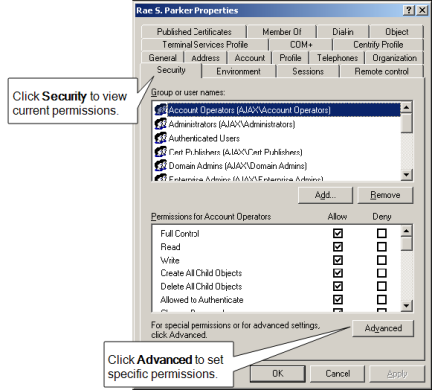
Use Active Directory Users and Computers to set basic or advanced permissions on any Active Directory object through the Security tab.
To display the Security tab, select View > Advanced Features. To access some permissions, however, your user account must have Create all child objects or Write all properties permissions.
-
Run the Zone Delegation Wizard to set the appropriate permissions for specific users or groups to perform specific tasks within a zone.
-
Click Permissions when viewing Zone Properties in Access Manager to set basic or advanced permissions on any zone object.
-
Click Permissions when viewing the IBM Profile for a user in Access Manager to set basic or advanced permissions on any user object.
The following steps illustrate how you can set permissions from Active Directory Users and Computers:
-
Open the console and connect to the Active Directory domain.
-
Select an Active Directory object, such as a user or computer, rightclick, then click Properties.
-
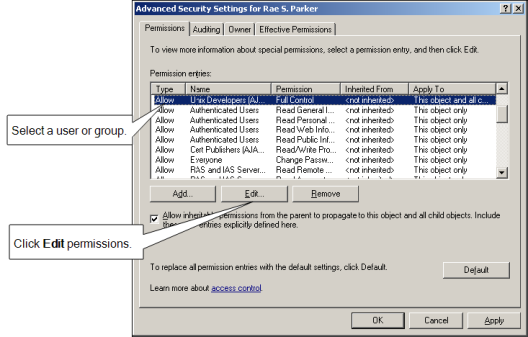
Click the Security tab, then click Advanced.
-
Select the user or group to which you want to assign rights, then click Edit.
If the user or group to which you want to assign permissions isn’t listed, click Add to find the account.
-
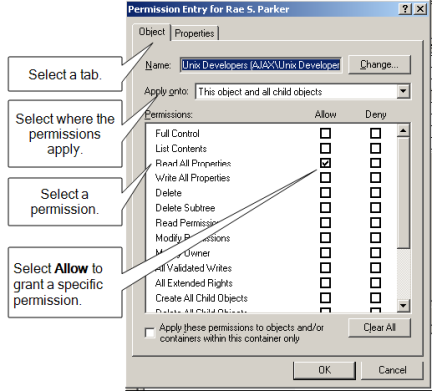
In the Permission Entry dialog box, click the Object or Properties tab, as needed.
Selecting Object or Properties and where the permission should be applied varies depending on the task you are allowing a user or group to perform.
-
Select the specific rights you want to assign by scrolling to find the permission, then clicking the Allow check box.
-
When you are finished setting the appropriate permissions, click OK.
For more specific information about how to set permissions on Active Directory objects and properties and how to view, modify, and remove permissions, see your Active Directory documentation.
Permissions Required to Use the Setup Wizard
In most cases, you run the Setup Wizard to guide you through the configuration of Active Directory for IBM. The Setup Wizard updates Active Directory with IBM-specific objects and properties, including zone and license containers that are required for proper operation.
To successfully perform initialization tasks, the user account that runs the Setup Wizard must have specific rights. Because some of these rights might be reserved for administrative accounts, some users might be prevented from performing certain steps in the Setup Wizard.
To allow other user accounts to run the Setup Wizard, you can manually create the appropriate container objects, then assign to those objects only the specific permissions needed to correctly complete the configuration of IBM-specific objects. Users can then use the Setup Wizard to select the appropriate container objects and perform all of the necessary steps without being members of an administrative group.
Licenses Container Permission Requirements
The following table describes the minimum rights that must be applied to the IBM specific container objects or other users to successfully complete the configuration of IBM software.
| This target object | Requires these permissions | Applied to |
|---|---|---|
| Licenses container | Read all properties Create classStore Objects Modify permissions | This object only |
| Write Description property Write displayName property | This object and all child objects | |
| The Setup Wizard requires you to create or select at least one parent container for license keys. By default, this container object is: domain/Program Data/Centrify/Licenses You can create additional License containers, if needed, through the Manage Licenses dialog box. By default, all Authenticated Users have read and list contents permission for the Licenses container and all of its child objects. You can change these permissions if you want to restrict access to Access Manager. | ||
| Zones container or any container used as a destination for a new zone | Read all properties Create classStore Objects Create container objects | This object only |
| Write displayName property | This object and all child objects | |
| The Setup Wizard requires you to create or select a parent container object for creating new zones. By default, this container object is: domain/Program Data/Centrify/Zones You can use other containers for zones, if needed. For example, if you have created a separate high-level organizational unit called UNIX as the parent container: domain/UNIX/Zones | ||
| ZoneName/Computers container | Create group objects Write Description property | This object only |
| These permissions are only needed if you are supporting “agentless” authentication in a zone. | ||
| Computers container For example, the generic Computers container: domain.com/Computers | Write operatingSystem property Write operatingSystemVersion property Write operatingSystemHotfix property Write operatingSystemServicePack property | SELF on Computer objects |
| These permission are granted to each computer’s SELF account when you select the Grant computer accounts in the Computers container permission to update their own account information option in the Setup Wizard. |
Licenses Container Permissions
The following table describes the minimum rights that must be applied to the IBM Licenses container that stores the license keys for your installation.
| This target object | Requires these permissions | Applied to |
|---|---|---|
| Licenses container | Read all properties Create classStore Objects Modify permissions | This object only |
| Write Description property Write displayName property | This object and all child objects |
The Setup Wizard requires you to create or select a parent container for license keys. The default location for the parent container for license keys depends on the organizational structure you deploy. For example, if you use the recommended organizational structure, the default location for licenses would be domain/Centrify/Licenses.
You must have at least one parent container for license keys in the forest. You might want to create more than one license container objects to give you more granular control over who has access to which licenses.
By default, all Authenticated Users have Read and List Contents permission for the Licenses container and all of its child objects. These permissions are required to use Access Manager. You can change who has these permissions if you want to prevent users from using Access Manager.
Zones Container Permissions
The following table describes the minimum rights that must be applied to the IBM Zones container.
| This target object | Requires these permissions | Applied to |
|---|---|---|
| Zones container or any container used as a destination for a new zone | Read all properties Create classStore Objects Create container objects | This object only |
| Write displayName property | This object and all child objects | |
| Change the default zone container | Delete | Previous zone container |
The Setup Wizard requires you to create or select a parent Zones container object for new zones. The default location for the parent container for new zones depends on the organizational structure you deploy. For example, if you use the recommended organizational structure, the default location for new zones would be domain/Centrify/Zones. You can use other containers for zones or create multiple parent containers for zones to separate administrative duties for different groups.
Computers Container Permissions
The following table describes the minimum rights that must be applied to the generic Computers container (domain/Computers).
| This target object | Requires these permissions | Applied to |
|---|---|---|
| Computers container | Write operatingSystem property Write operatingSystemVersion property Write operatingSystemHotfix property Write operatingSystemServicePack property | SELF on Computer objects |
These permission are granted to each computer’s SELF account when you select the Grant computer accounts in the Computers container permission to update their own account information option in the Setup Wizard.
Computers Container Within a Zone Permissions
The following table describes the minimum rights that must be applied to the Computers container in a named zone if you are supporting “agentless” authentication in that zone.
| This target object | Requires these permissions | Applied to |
|---|---|---|
| ZoneName/Computers container | Create group objects Write Description property | This object only |
Creating Parent Containers Manually
Some organizations prefer to create and manage Active Directory objects manually to ensure tight control over the objects and their related attributes. For example, you might want to manually create separate Zones or Licenses parent containers for different business units or geographic locations so that you can manually set different sets of permissions and related properties on those containers. Creating objects manually also enables you to have precise control over who has access to the objects.
You can create the container objects anywhere in the forest’s directory structure, but you must have at least one parent Zones container object and at least one parent Licenses container object.
Optional Administrative Tasks
By default, IBM does not require you to be an enterprise administrator or domain administrator of the forest root domain to install or configure IBM-specific properties. However, some optional configuration tasks do require you to be an enterprise administrator or a domain administrator of the forest root domain.
These optional tasks involve:
- Creating display specifiers for IBM profiles to enable access to the IBM Profile properties page in Active Directory Users and Computers.
- Registering the administrative notification handler to ensure data consistency if users delete IBM objects using Active Directory Users and Computers.
- Setting permissions for zones objects to enable maximum control over the placement of and rights associated with IBM-related objects within Active Directory.
In most cases, if you want to perform any of these tasks, you must use an account that is an enterprise administrator or a domain administrator of the forest root domain.
Creating Display Specifiers for IBM Profiles
To display the IBM Profile properties in Active Directory Users and Computers, you must be an enterprise administrator or a domain administrator for the forest root domain because adding the IBM Profile to Active Directory Users and Computers requires you to add display specifiers to Active Directory.
A display specifier is an Active Directory object that allows you to add components to the Active Directory Users and Computers (ADUC) Microsoft management console (MMC) snap-in.
If you want to make the IBM Profile available in Active Directory Users and Computers, an enterprise administrator can manually define the display specifiers (under domain/Configuration/DisplaySpecifiers/LanguageID/) for computer, group, and user properties by modifying the adminPropertyPages attribute with the appropriate GUID. For example, if the Active Directory domain is ajax.org and the language you support is US-English (CN=409), you would define the display specifiers in:
ajax.org/Configuration/DisplaySpecifiers/409
Adding the display specifiers for IBM properties is an optional step you can perform manually using ADSI Edit or by running the displayspecifier.vbs script. If you manage all IBM objects through Access Manager, you do not need to perform this task.
To use the displayspecifier.vbs script to set up the display specifiers:
-
Log on using an enterprise administrator account or a domain administrator for the forest root domain.
-
Open a Command Prompt window and change to the Centrify installation directory. For example:
cd C:\Program Files\Centrify\Access Manager
-
Run the displayspecifier.vbs script.
If you want to manually add the display specifiers to display property pages in Active Directory Users and Computers, you must create the following entries using ADSI Edit, where n is the next number in the index of values for the attribute:
| For this target object | Set this attribute | To |
|---|---|---|
| computer-Display displaySpecifier | adminPropertyPages | n,{DB5E4BE1-A0F0-4e6c-AD8A-B46475D727CB} |
| group-Display displaySpecifier | adminPropertyPages | n,{0CDC9AD0-E870-483f-8D16-17EAB3B7F881} |
| user-Display displaySpecifier | adminPropertyPages | n,{543DBFE3-317D-4493-8D00-84591E4EDCDE} |
| inetOrgPerson-Display | adminPropertyPages | n,{543DBFE3-317D-4493-8D00-84591E4EDCDE} |
For example, if the Active Directory domain is ajax.org and the language you support is US-English (CN=409), you would add these entries to the objects in:
ajax.org/Configuration/DisplaySpecifiers/409
In most cases, you only need to set up the display specifiers once for the Active Directory forest. If you support multiple languages, you can manually add the display specifiers to each language you support. For example, if your organization supports US-English (CN=409), Standard French (CN=40C), and Japanese (CN=411), you would add the display specifiers to these three containers. Once you have updated Active Directory by running the displayspecifier.vbs script or by manually adding the display specifiers, you can access the IBM Profile properties using Active Directory Users and Computers.
Registering the Administrative Notification Handler
The administrative notification handler provides services to ensure data integrity in the Active Directory forest. You can register the notification handler automatically through the Setup Wizard the first time you start Access Manager, but this requires an account that is an enterprise administrator or a domain administrator in the forest root domain.
Registering the administrative notification handler is optional, but doing so helps to ensure that no orphan UNIX data is left in the directory if a user, group, or computer is deleted using Active Directory Users and Computers. When registered, the notification handler automatically deletes any service connection point (SCP) dependencies on a directory object if the directory object is deleted. Without this service, deleting a directory object such as a computer or user account in Active Directory might leave an orphan service connection point for the object in the directory.
If you don’t want to perform this step in the Setup Wizard, you can manually configure the administrative notification handler using ADSI Edit or you can choose not to register the administrative notification handler for IBM. If you choose not to register the administrative notification handler, however, you should periodically run the Analyze command to check for orphan data in the Active Directory forest.
To manually set up the administrative notification handler for IBM, add the following entry using ADSI Edit under domain/Configuration/DisplaySpecifiers/LanguageID/ where n is the next number in the index of values for the attribute:
| For this target object | Set this attribute | To |
|---|---|---|
| DS-UI-Default-Settings | dSUIAdminNotification | n,{D0D2C2AE-C143-4C81-A61C-BE95C3C5EEDF} |
For example, if the Active Directory domain is ajax.org and the language you support is US-English (CN=409), you would add this entry to the object in:
ajax.org/Configuration/DisplaySpecifiers/409
Granting Permissions For Administrative Tasks
The easiest way to grant permissions to perform administrative tasks is to use the Zone Delegation Wizard. The Zone Delegation Wizard enables you to delegate specific administrative tasks to specific users and groups. For each task you delegate to a specific user or group, you are providing that user or group with a specific set of permissions for working with objects in Active Directory.
The user who creates a zone has full control on the zone’s serviceConnectionPoint. That user has exclusive permission to delegate administrative tasks to other users. The user who creates a zone is also the only user who can add NIS maps to the zone because creating NIS maps requires permission to create containers in Active Directory. The zone creator can, however, grant other users permission to add, remove, or modify NIS map entries.
The following table summarizes the permissions that can be assigned through your selections in the Zone Delegation Wizard. In addition to the permissions listed, however, the basic Read permission is required to perform any action. The Read permission is granted to Authenticated Users by default.
| Selecting this task | Grants these rights |
|---|---|
| All | Permissions to perform all of the actions listed in the Zone Delegation Wizard and described below. This option allows a designated user or group to perform all of the other actions. Only the user who creates a zone can grant this permission to other users and groups for the zone. |
| Change zone properties | List contents on the ZoneName object container. Read all properties on the ZoneName object container. Write name on the ZoneName object container. Write Name on the ZoneName object container. Write Description property on the ZoneName object container. |
| Add users | List contents on the ZoneName/Users object container. Read all properties on the ZoneName/Users object container. Create serviceConnectionPoint objects on the ZoneName/Users object container. |
| Add groups | List contents on the ZoneName/Groups object container. Read all properties on the ZoneName/Groups object container. Create serviceConnectionPoint objects on the ZoneName/Groups object container. |
| Add local users | List contents on the ZoneName/Local Users object container. Read all properties on the ZoneName/Local Users object container. Add local users to the zone. |
| Add local groups | List contents on the ZoneName/Local Groups object container. Read all properties on the ZoneName/Local Groups object container. Add local groups to the zone. |
| Join computers to the zone | List contents on the ZoneName/Computers object container. Read all properties on the ZoneName/Computers object container. Create serviceConnectionPoint objects on the ZoneName/Computers object container. Note Joining the domain requires additional permissions on the Active Directory computer object, but the join command performs the necessary operations without requiring the additional permissions to be granted to the user or group you are designating as a trustee. |
| Remove zones | List contents on the ZoneName object container. Read all properties on the ZoneName object container. Allow Delete on the ZoneName object container. Allow Delete Subtree on the ZoneName object container. |
| Remove users | List contents on the ZoneName/Users object container. Read all properties on the ZoneName/Users object container. Delete serviceConnectionPoint objects on the ZoneName/Users object container. |
| Remove groups | List contents on the ZoneName/Groups object container. Read all properties on the ZoneName/Groups object container. Delete serviceConnectionPoint objects on the ZoneName/Groups object container. |
| Remove local users | List contents on the ZoneName/Local Users object container. Read all properties on the ZoneName/Local Users object container. Remove local users from the zone. |
| Remove local groups | List contents on the ZoneName/Local Groups object container. Read all properties on the ZoneName/Local Groups object container. Remove local groups from the zone. |
| Remove computers from the zone | List contents on the ZoneName/Computers object container. Read all properties on the ZoneName/Computers object container. Delete serviceConnectionPoint objects on the ZoneName/Computers object container. |
| Modify user profiles | List contents on the ZoneName/Users object container. Read all properties on the ZoneName/Users object container. Write cn on the serviceConnectionPoint object. Write name on the serviceConnectionPoint object. Write Name on the serviceConnectionPoint object. Write keywords on the serviceConnectionPoint object. For RFC 2307-compliant zones, modifying the user’s UNIX profile also requires the following rights on the serviceConnectionPoint object of the UNIX user object: Write uid. Write uidNumber. Write loginShell. Write gidNumber. Write gecos. Write unixHomeDirectory. The additional rights for RFC 2307-compliant zones are applied to the posixAccount object associated with the serviceConnectionPoint for the UNIX user object. |
| Modify group profiles | List contents on the ZoneName/Groups object container. Read all properties on the object containers. Write name on the serviceConnectionPoint object. Write Name on the serviceConnectionPoint object. Write keywords on the serviceConnectionPoint object. For RFC 2307-compliant zones, modifying the group’s UNIX profile also requires the following rights applied to the posixGroup object associated with the serviceConnectionPoint object of the UNIX group object: Write gidNumber. |
| Modify local user profiles | List contents on the ZoneName/Local Users object container. Read all properties on the ZoneName/Local Users object container. Modify local users in the zone. Parameters that can be modified are: User name (the UNIX login name). The user identifier (UID). The user’s primary group profile numeric identifier (GID). The default home directory for the user. The default login shell for the user. General information about the user account (GECOS). State. |
| Modify local group profiles | List contents on the ZoneName/Local Groups object container. Read all properties on the object containers. Modify local groups in the zone. Parameters that can be modified are: Group name. Group members. Group identifier (GID). State. |
| Modify computer profiles | List contents on the ZoneName/Computers container object. Read all properties on the ZoneName/Computers container object. Write description on the ZoneName/Computers container object if the zone is a hierarchical zone. Write keywords on the serviceConnectionPoint object. Write displayName on the serviceConnectionPoint object. Write cn on the serviceConnectionPoint object. Write name on the serviceConnectionPoint object. |
| Allow computers to respond to NIS client requests | List contents on the ZoneName/Computers/zone_nis_servers group object. Read all properties on the ZoneName/Computers/zone_nis_servers group object. Write member property of group object on the ZoneName/Computers/zone_nis_servers group object. |
| Import users and groups to zone | List contents on the ZoneName/Users and ZoneName/Groups container object. Read all properties on the ZoneName/Groups container object. Create serviceConnectionPoint on the ZoneName/Users and ZoneName/Groups container objects. Write cn on the serviceConnectionPoint object. Write name on the serviceConnectionPoint object. Write managedby on the serviceConnectionPoint object. Write displayName on the serviceConnectionPoint object. Write keywords on the serviceConnectionPoint object. For RFC 2307-compliant zones, importing users also requires the following rights on the serviceConnectionPoint object of the UNIX user object ZoneName/Users: - Write uid. - Write uidNumber. - Write loginShell. - Write gidNumber. - Write unixHomeDirectory. - Write gecos. For RFC 2307-compliant zones, importing groups also requires the following right on the serviceConnectionPoint object of the UNIX group object under ZoneName/Groups: - Write gidNumber. |
| Manage roles and rights | List contents on the AzTask container and all child objects. Read all properties on the AzTask container and all child objects. Create msDS-AzTask objects Delete msDS-AzTask objects Write msDS-AzApplicationData on the msDs-AzTask object. Write cn on the msDs-AzTask object. Write name on the msDs-AzTask object. Write description on the msDs-AzTask object. Write msDs-OperationsForAzTask on the msDs-AzTask object. List contents on the AzOperation container and all child objects. Read all properties on the AzOperation container and all child objects. Create msDS-AzOperation objects Delete msDS-AzOperation objects Write msDs-AzApplicationData on the msDs-AzOperation object. Write cn on the msDs-AzOperation object. Write name on the msDs-AzOperation object. Write description on the msDs-AzOperation object. List contents on the msDS-AzAdminManager object. Read all properties on msDS-AzAdminManager object. Write msDs-AzApplicationData on msDS-AzAdminManager object. |
| Manage role assignments | List contents on the msDS-AzAdminManager object and all child objects. Read all properties on the msDS-AzAdminManager object and all child objects. Create msDS-AzRole objects. Delete msDS-AzRole objects. Write msDS-AzApplicationData on the msDS-AzRole object. Write msDS-TasksForAzRole on the msDS-AzRole object. Write msDS-MembersForAzRole on the msDS-AzRole object. Write displayName on the msDS-AzRole object. Write msDS-AzApplicationData on the msDS-AzAdminManager object. |
| Modify computer roles | List contents on the ZoneName object and all child objects. Read all properties on the ZoneName object and all child objects. Write msDS-AzApplicationData Write msDS-AzScopeName Write description |
| Add or remove NIS map entries | List contents on the ZoneName/NISMaps object container. Read all properties on the ZoneName/NISMaps object container. Create classStore Objects on the ZoneName/NISMaps object container. Write name on the ZoneName/NISMaps object container. Write Name on the ZoneName/NISMaps object container. |
| Modify NIS map entries | List contents on the ZoneName/NISMaps object container. Read all properties on the ZoneName/NISMaps object container. Write adminDescription on the classStore object. Write Description on the classStore object. Write wWWHomePage on the classStore object. |
| Remove NIS maps | List contents on the ZoneName/NISMaps object container. Read all properties on the ZoneName/NISMaps object container. Allow Delete on the MapName object. Allow Delete Subtree on the MapName object. |
In some cases, the permissions granted through the Zone Delegation Wizard are a subset of the complete permissions required to perform some tasks. For information about the complete permissions required to perform a specific task, see the section that describes the permissions for performing that task. For example, for information about setting permissions for NIS maps, see Setting permissions for NIS maps.
Setting permissions for zones
The user who creates a zone has full control over zone properties and administrative tasks. Only the zone owner can delegate administrative tasks to other users and groups through the Zone Delegation Wizard. In most cases, the users who are allowed to create zones have domain administrator privileges and sufficient permissions to perform all administrative tasks and to delegate administrative tasks to other users.
If you manually set permissions to allow domain users to create zones, however, you should also manually set the permissions to allow those users to manage rights and roles or notify zone administrators that they should run the Zone Delegation Wizard and assign those tasks to their own account or to appropriate users and groups. At least one administrator must have permission to add an authorization store, define rights and roles, and manage role assignments in each zone. All users must have at least one valid role assignment to access a zone.
Creating a Zone
To create new zones, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for new zones you created or selected in the Setup Wizard. For example: domain/UNIX/Zones | On the Object tab, select Allow to apply the following permission to this object and all child objects: Create Container Objects Create Organizational Unit Objects Note Both permissions are required if you want to allow zones to be created as either container objects or organizational unit objects. |
| Parent container for Computers in the zone | On the Object tab, select Allow to apply the following permission to this object only: Create group objects Click the Properties tab and select Allow to apply the following properties to this object only: Write Description property These permissions are only needed if you are supporting “agentless” authentication in the new zone. |
Opening Zones
To open an existing zone, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for new zones For example: domain/UNIX/Zones | On the Object tab, select Allow to apply the following permission to this object: List contents |
| Container for the individual zone For example, a ZoneName container object, such as: domain/UNIX/Zones/arcade | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributes Read allowedAttributesEffective Read canonicalName Read Description Read displayName Read name Read objectClass |
| Parent container for Users in the zone | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectClass |
| Parent container for Groups in the zone | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectClass |
Modifying Zone Properties
To modify zone properties for a zone, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for an individual zone For example, a ZoneName container object: domain/UNIX/Zones/arcade | Click the Properties tab and select Allow to apply the following properties to this object only: Read Name Read name Read Description Read displayName Write Description Note You can grant these permission to specific users or groups by selecting the Change zone properties task in the Zone Delegation Wizard. These permissions also enable you to change the parent zone for a selected zone object. |
Renaming a Zone
To rename a zone, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for an individual zone For example, a ZoneName container object, such as: domain/UNIX/Zones/arcade | Click the Properties tab and select Allow to apply the following properties to this object only: Write name property Write Name property Note You can grant this permission to specific users or groups by selecting the Change zone properties task in the Zone Delegation Wizard. |
Deleting a Zone
To delete a zone from Active Directory, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for an individual zone For example, a ZoneName container object, such as: domain/UNIX/Zones/arcade | On the Object tab, select Allow to apply the following properties to this object only: Delete Delete Subtree Click the Properties tab and select Allow to apply the following properties to this object only: Read Name Read name Read displayName Note You can grant this permission to specific users or groups by selecting the Delete zone task in the Zone Delegation Wizard. |
Managing Roles and Rights in a Zone
To manage rights and roles in a zone, including creating and deleting role definitions and updating time constraints, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for the authorization store For example: domain/UNIX/Zones/arcade/Authorization | On the Object tab, select Allow to apply the following properties to this object and all child objects: List contents Read all properties Click the Properties tab and select Allow to apply the following properties to the msDS-AzAdminManager object: Write msDS-AzApplicationData |
| AzTaskObjectContainer | On the Object tab, select Allow to apply the following properties to this object and all child objects: List contents Read all properties Create msDS-AzTask objects Delete msDS-AzTask objects Click the Properties tab and select Allow to apply the following properties to msDS-AzTask objects: Write msDS-AzApplicationData Write cn Write name Write description Write msDs-OperationsForAzTask |
| AzOpObjectContainer | On the Object tab, select Allow to apply the following properties to this object and all child objects: List contents Read all properties Create msDS-AzOperation objects Delete msDS-AzOperation objects Click the Properties tab and select Allow to apply the following properties to msDS-AzOperation objects: Write msDS-AzApplicationData Write cn Write name Write description |
Managing Role Assignments in a Zone
To manage role assignments in a zone, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for the authorization store For example: domain/UNIX/Zones/arcade/Authorization | On the Object tab, select Allow to apply the following properties to this object only: List contents Read all properties Create all child objects Delete all child objects Click the Properties tab and select Allow to apply the following properties to this object only: Write msDS-AzApplicationData Click the Properties tab and select Allow to apply the following properties to msDS-AzRole objects: Write displayName Write msDS-AzApplicationData Write msDS-TasksForAzRole Write msDS-MembersForAzRole |
| Computers container in the zone | On the Object tab, select Allow to apply the following properties to this object only: Create Container Right This permission is required to allow a delegated user to make the first role assignment after a computer is joined to Active Directory. |
| AzRoleObjectContainer | On the Object tab, select Allow to apply the following properties to the msDS-AzApplication object and all child objects: List contents Read all properties Create msDS-AzRole objects Delete msDS-AzRole objects Click the Properties tab and select Allow to apply the following properties to msDS-AzRole objects: Write displayName Write msDS-AzApplicationData Write msDS-TasksForAzRole Write msDS-MembersForAzRole Click the Properties tab and select Allow to apply the following properties to msDS-AzAdminManager objects: Write msDS-AzApplicationData |
| AzOpObjectContainer | On the Object tab, select Allow to apply the following properties to this object only: Read all properties Create msDS-AzOperation objects Delete msDS-AzOperation objects Create msDS-AzRole objects Delete msDS-AzRole objects Click the Properties tab and select Allow to apply the following properties to msDS-AzRole objects: Write displayName Write msDS-AzApplicationData Write msDS-TasksForAzRole Write msDS-MembersForAzRole Click the Properties tab and select Allow to apply the following properties to msDS-AzOperation objects: Read name Read Name Write msDS-AzApplicationData Write name Write description |
Changing Computer Role Properties in a Zone
To manage computer role properties in a zone, your user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Container for the authorization store For example: domain/UNIX/Zones/arcade/Authorization/guid The guid object is a globally unique identifier (GUID) for the Authorization object. For example: CN=cab186af-61a0-4d54-a0dd... | On the Object tab, select Allow to apply the following properties to this object only: Read all properties Click the Properties tab and select Allow to apply the following properties to msDS-AzScope objects: Read name Read Name Write msDS-AzApplicationData Write msDS-AzScopeName Write description |
Setting Permissions to Join or Leave the Domain
To join a UNIX computer to an Active Directory domain without predefining a computer account, your Active Directory user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for computer accounts For example: domain/UNIX/Servers | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects Note You can grant this permission to specific users or groups by selecting the Join computers task in the Zone Delegation Wizard. |
To join a UNIX computer to an Active Directory domain and place the computer account in a specific organizational unit (OU), the Active Directory account used to join the domain must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer accounts | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects Create Computer Objects |
To join a UNIX computer to an Active Directory domain when you are using a predefined computer account, your Active Directory user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer account | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects |
| Computer account object in Active Directory For example, if the computer account is AJAX in the default Active Directory Computers container: domain/Computers/AJAX | On the Object tab, select Allow to apply the following permission to this object only: Full Control This permission is required for enabling or disabling a computer account. |
To remove a UNIX computer from an Active Directory domain, your Active Directory user account must be set with the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer account | On the Object tab, select Allow to apply the following permission to this object only: Delete serviceConnectionPoint Objects If you are deleting a computer account, you also need the Delete Computer Objects permission. |
This setting only gives the user or group permission to leave an Active Directory domain. If you want to grant permission for a user or group to delete a computer account, you also need the Delete Computer Objects permission.
Setting Permissions for Zone Computers
Although joining or leaving a domain is the primary task for working with computer accounts in Active Directory, there are also specific permissions required to list computers or modify computer properties. The objects and permissions can also vary depending on the type of zone the computer account is associated with and the task to be performed. In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard.
In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard instead of assigning the permissions manually.
Joining a Computer to a Zone
To join a computer to a zone, your user account must have the following permission:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer account in the zone For example, in a classic zone, the ZoneName/Computers container object: domain/UNIX/Zones/acme/Computers | Click the Object tab and select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects |
| Computer account object in Active Directory For example, if the computer account name is AJAX: domain/UNIX/Servers/AJAX | Click the Object tab and select Allow for the Full Control permission for the user with permission to join the domain. The adjoin command grants the computer’s SELF account the following permissions: Write operatingSystem Write operatingSystemVersion Write operatingSystemHotfix Write operatingSystemServicePack Write servicePrincipalName Write userAccountControl Write dnsHostName |
Listing Computer Accounts
To list computers, your user account must have the following permission:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer account in Active Directory For example: domain/UNIX/Servers | On the Object tab, select Allow to apply the following permission to this object for each of the computers to be included in the list: List contents |
| Parent container object for the computer account in the zone For example, in a classic zone, the ZoneName/Computers container object: domain/UNIX/Zones/acme/Computers | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectClass |
| The serviceConnectionPoint object for the computer account For example, if the computer account name is AJAX, select: domain/UNIX/Servers/AJAX then select: serviceConnectionPoint objects | Click the Properties tab and select Allow to apply the following properties to this object for each of the computers to be included in the list: Read displayName Read keywords Read managedBy Read Name Read objectClass |
| Computer account object in Active Directory For example, if the computer account name is AJAX: domain/UNIX/Servers/AJAX | Click the Properties tab and select Allow to apply the following properties to this object for each of the computers to be included in the list: Read objectClass Read Operating System Read Operating System Version Read userAccountControl |
Modifying Computer Properties
To modify any computer account properties for a UNIX computer, your user account must have the following permission:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the computer account in Active Directory For example: domain/UNIX/Servers | On the Object tab, select Allow to apply the following permission to this object only: List contents |
| The serviceConnectionPoint object for the computer account For example, if the computer account name is AJAX, select: domain/UNIX/Servers/AJAX then select: serviceConnectionPoint objects | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributes Read allowedAttributesEffective Read displayName Read keywords Read managedBy Read Name Read objectClass Write keywords |
| Computer account object in Active Directory For example, if the computer account is AJAX in the default Active Directory Computers container: domain/UNIX/Servers/AJAX | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectGUID Read objectSid Read objectClass Read Operating System Read Operating System Version Read userAccountControl |
Responding to NIS Requests
If you are supporting “agentless” authentication or want to allow a computer to service NIS client requests in a zone, the computer must be a member of the zone_nis_servers group in the zone. Setting or unsetting the Allow this computer to respond to NIS client requests property requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The zone_nis_servers group object For example, select: domain/UNIX/Zones/acme/Computers/zone_nis_servers | Click the Properties tab and select Allow to apply the following properties to this object only: List contents Read all properties Write member property If the zone_nis_servers group does not already exist in the current zone, setting the Allow this computer to respond to NIS client requests property also requires the following permission on the ZoneName/Computers object: Create group objects |
Changing the Computer Zone
If you need to change the zone for a computer account, your user account must have the following additional permissions:
| Select this target object | To apply these permissions |
|---|---|
| All parent container objects for the original and new zones | Click the Properties tab and select Allow to apply the following properties to this object only: Read name Read Name |
| The serviceConnectionPoint object for the computer account | Click the Properties tab and select Allow to apply the following properties to this object only: Write name Write Name Note The Name property is the common name (cn) of the serviceConnectionPoint object. |
| Original parent container for the computer account in the current zone For example, if you are moving a computer from the Finance zone to the Corporate zone, the target object would be: domain/UNIX/Zones/Finance/Computers | On the Object tab, select Allow to apply the following permission to this object only: Delete serviceConnectionPoint Objects Click the Properties tab and select Allow to apply the following properties to this object only: Read objectGUID |
| New parent container for the computer account in the new zone For example, if you are moving a computer from the Finance zone to the Corporate zone, and you use the default Computers container, the target object would be: domain/UNIX/Zones/Corporate/Computers | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects Click the Properties tab and select Allow to apply the following properties to this object only: Read objectGUID |
You can set the permissions for modifying computer accounts by clicking the Security tab when you are viewing a computer’s properties.
Preparing a Computer Object
To prepare a computer account in a zone before joining, the following permissions apply to the user or group you want to designate as the trustee for joining the domain.
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the computer account | Click the Object tab and select Allow to apply the following permission to this object only: Read all properties Write keywords property Write displayName property |
| Computer account object in Active Directory For example, if the computer account name is AJAX: domain/Computers/AJAX | Click the Object tab and select Allow to apply the following permission to this object only: Read Permission Reset Password Write userAccountControl Validated write to DNS host name Validated write to service principal name Write to service principal name Write msDS-SupportedEncryptionTypes Write Account Restrictions Write Description Write displayName Write computer name (Pre-Windows 2000) Delete Delete Subtree All Extended Rights |
The adjoin command resets the computer account and grants the computer’s SELF account the following permissions:
- Write operatingSystem
- Write operatingSystemVersion
- Write operatingSystemHotfix
- Write operatingSystemServicePack
- Write altSecurityIdentities
Creating The Computer Object Manually
If you use Active Directory Users and Computers to prepare the computer object instead of the Prepare Computer wizard, the following permissions must be granted on the computer for the trustee:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the computer account | Click the Object tab and select Allow to apply the following permission to this object only: Read all properties Write keywords property Write displayName property |
| Computer account object in Active Directory For example, if the computer account name is AJAX: domain/Computers/AJAX | Click the Object tab and select Allow to apply the following permission to this object only: Read Permission Reset Password Write userAccountControl Validated write to DNS Host Name Validated write to service principal name Write Account Restrictions Write Description Write displayName Write computer name (Pre-Windows 2000) Write operatingSystem Write operatingSystemVersion Write operatingSystemHotfix Write operatingSystemServicePack Write altSecurityIdentities Write msDS-SupportedEncryptionTypes Delete Delete Subtree All Extended Rights |
Modifying Computer Roles
If you use computer role assignments to control access to a computer, the following permissions are required to modify computer roles:
| Select this target object | To apply these permissions |
|---|---|
| msDS-AzScope This object is listed under a globally unique identifier (GUID) for the Authorization object. For example: CN=cab186af-61a0-4d54-a0dd... | Click the Properties tab and select Allow to apply the following properties to this object only: Read description Read msDS-AzScopeName Read msDS-AzApplicationData Write description Write msDS-AzScopeName Write msDS-AzApplicationData |
Deleting Computer Roles
If you use computer role assignments to control access to a computer, the following permissions are required to delete computer roles:
| Select this target object | To apply these permissions |
|---|---|
| msDS-AzScope This object is listed under a globally unique identifier (GUID) for the Authorization object. | Click the Properties tab and select Allow to apply the following properties to this object only: Read Name Read name Read displayName Allow Delete Allow Delete Tree |
Setting Permissions For Zone Users
The specific objects and permissions required to work with user accounts depend on the type of zone the user account is associated with and the task to be performed.
In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard instead of assigning the permissions manually.
Adding Users To Standard Zones
In a standard IBM zone when the functional level of the forest is Windows Server 2003 or later, adding a user account with an Active Directory security group as the primary group to a zone requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the user profile For example, if you use classic zones, the default Users container in the Finance zone: domain/UNIX/Zones/Finance/Users | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint Objects This permission is required for both standard zones and RFC 2307compliant zones. For standard zones, you need to apply additional permissions. Click the Properties tab and select serviceConnectionPoint objects from the object list, then select Allow to apply the following properties to this object: Read Name Read name Read displayName |
| User account object in Active Directory For example: domain/Users/user_name | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectCategory Read objectClass Read objectGUID Read objectSid Read userAccountControl |
| Parent container object for the individual zone For example, if you are adding a user to the Finance zone: domain/UNIX/Zones/Finance | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectGUID Write Description |
Modifying Users In Standard Zones
In a standard zone, modifying user account properties for a user with a standard Active Directory security group as the primary group requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account For example, if you are using classic zones and the UNIX user name is chris: domain/UNIX/Zones/Finance/Users/chris then select serviceConnectionPoint objects | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributesEffective Read objectGUID Write keywords If you are changing the UNIX user name for the user, you need the following additional permissions applied to this object: Read name Write name Write Name property Note The Name property is the common name (cn) of the serviceConnectionPoint object. |
You can set the permissions for modifying user accounts by clicking Permissions when you are viewing the IBM Profile for a user.
Modifying Users In Rfc 2307-compliant Zones
In a standard RFC 2307-compliant zone, modifying user account properties for a user with an Active Directory security group as the primary group requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account For example, if you are using classic zones and the UNIX user name is chris: domain/UNIX/Zones/Finance/Users/chris then select serviceConnectionPoint objects | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributesEffective Write keywords Write uid Write uidNumber Write gidNumber Write loginShell Write unixHomeDirectory If you don’t see some of these attributes listed for serviceConnectionPoint objects, change the object selected to posixAccount objects, then click Allow for the additional properties. The GECOS field in a user’s UNIX profile is derived from the displayName attribute or the Name property (cn). |
You can grant the required permissions to specific users or groups for any zone by selecting the Modify users task in the Zone Delegation Wizard.
Listing Users In Standard Zones
In a standard zone, listing user account information requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account | Click the Properties tab and select Allow to apply the following properties to this object for each user included in the list: Read displayName Read managedBy Read objectClass Read Name to display the UNIX name Read keywords to display the other UNIX attributes |
Listing Users in RFC 2307-Compliant Zones
In a standard RFC 2307-compliant zone, listing user account information requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account | Click the Properties tab and select Allow to apply the following properties to this object for each user included in the list: Read displayName Read keywords Read managedBy Read objectClass Read uid to display the UNIX name Read uidNumber to display the UNIX UID Read gidNumber to display the GID of the user’s primary group Read logonShell to display the default shell for the user Read unixHomeDirectory to display the user’s home directory Read Public Information to display the userPrincipalName for the user |
Removing Users from Zones
Removing a user account from a standard zone or RFC 2307-compliant zone requires the following permission:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account | On the Object tab, select Allow to apply the following permission to this object only: Delete |
Setting Permissions for Zone Groups
The specific objects and permissions required to work with group accounts can vary depending on the type of zone the group is associated with and the task to be performed.
In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard instead of assigning the permissions manually.
Adding Security Groups to Zones
Adding an Active Directory group to a zone requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container object for the group For example, if you are using classic zones, the ZoneName/Groups container: domain/UNIX/Zones/acme/Groups | On the Object tab, select Allow to apply the following permission to this object only: Create serviceConnectionPoint objects Click the Properties tab and select Allow to apply the following properties to this object only: Read objectClass Note You can grant the required permissions to specific users or groups by selecting the Add or remove groups task in the Zone Delegation Wizard. |
| Group account object in Active Directory For example: domain/UNIX/UNIX groups/group_name | Click the Properties tab and select Allow to apply the following properties to this object only: Read groupType Read objectCategory Read objectClass Read objectGUID Read objectSid |
| Parent container object for the individual zone For example, if you are adding a group to the Finance zone: domain/UNIX/Zones/Finance | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectGUID Write Description |
Modifying Groups in Standard Zones
In a standard zone, modifying a group profile in a zone requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the group account For example, if the UNIX group name is web-qa in the HKLab zone: domain/UNIX/Zones/HKLab/Groups/web-qa then select serviceConnectionPoint objects | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributesEffective Read objectGUID Read Name If you are changing the UNIX group name for a group, you need the following additional permissions applied to this object: Read name Write name Write Name Note The Name property is the common name (cn) of the serviceConnectionPoint object. |
Modifying Groups in RFC 2307-Compliant Zones
In a standard RFC 2307-compliant zone, modifying a UNIX-enabled group in a zone requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the group account | Click the Properties tab and select Allow to apply the following properties to this object only: Read allowedAttributesEffective Read objectGUID Read Name If you are changing the UNIX group identifier for a group, you need the following additional permissions applied to this object: Read gidNumber Write gidNumber Note If you don’t see this attribute listed for the serviceConnectionPoint object, change the object selected to posixGroup objects. If you are changing the UNIX name for a group, you need the following additional permissions applied to this object: Read name Write name Write Name Note The Name property is the common name (cn) of the serviceConnectionPoint object. |
Listing Groups in Zones
In a standard zone, listing group account information requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the group account | Click the Properties tab and select Allow to apply the following properties to this object for each group included in the list: Read displayName Read managedBy Read objectClass Read Name to display the UNIX group name Read keywords to display the UNIX GID |
Listing Groups in RFC 2307-Compliant Zones
In a standard RFC 2307-compliant zone, listing group account information requires the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the user account | Click the Properties tab and select Allow to apply the following properties to this object for each user included in the list: Read displayName Read keywords Read managedBy Read objectClass Read objectGUID Read Name to display the group name Read gidNumber to display the group GID |
Removing Groups from Zones
Removing an Active Directory group from a standard zone or RFC 2307-compliant zone requires the following permission:
| Select this target object | To apply these permissions |
|---|---|
| The serviceConnectionPoint object for the group account | On the Object tab, select Allow to apply the following permission to this object only: Delete |
Setting Permissions for License Keys
Starting Access Manager requires the following permissions on the container object for licenses:
| Select this target object | To apply these permissions |
|---|---|
| The domain root object For example, if the root domain of the forest is arcade.com: DC=arcade,DC=com | Click the Properties tab and select Allow to apply the following properties to this object only: Read objectClass |
| Parent container for the Licenses container object For example: domain/Centrify UNIX | On the Object tab, select Allow to apply the following permission to this object only: List contents |
| Parent container for license keys For example, the Licenses container object you created or selected in the Setup Wizard: domain/Centrify UNIX/Licenses | On the Object tab, select Allow to apply the following permission to this object only: List contents |
To add and remove license keys, your user account must have the following permissions:
| For this target object | You need these permissions |
|---|---|
| Parent container for license keys For example, the Licenses container object you created or selected in the Setup Wizard: domain/Centrify UNIX/Licenses | Click the Properties tab and select Allow to apply the following properties to this object and all child objects: Write Description |
Setting Permissions for NIS Maps
You can delegate administrative permissions for all NIS maps in a zone or for any specific NIS map within a zone by selecting either the NIS Maps parent container object or the specific NIS map object you want to work with. If you select the NIS Maps parent container object, the permissions you set apply to all NIS maps you add to the zone. If you select the individual NIS map object, the permissions you set only apply to that individual NIS map.
To set permissions on NIS maps or NIS map entries
-
Open the ADSI Edit MMC snap-in and connect to the Active Directory domain.
For NIS maps, you must use the Zone Delegation Wizard or ADSI Edit to set Active Directory permissions.
-
In the console tree, navigate to the zone folder.
For example, if you deployed using the recommended organizational structure, expand the domain, IBM, Zones, and select a specific zone name.
-
Select CN=NisMaps to set permissions for all NIS maps in a zone, right-click, then select Properties.
If setting permissions for an individual map, expand CN=NisMaps, then select the map object—such as CN=auto_master—right-click and select Properties.
-
Click the Security tab, then click Advanced.
-
Click Add to search for the user or group to which you want to give administrative privileges, select the user or group in the results, then click OK.
-
Scroll to locate the appropriate permissions for the object and its properties to allow the selected user or group to perform the administrative task, click Allow, then click OK.
In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard instead of assigning the permissions manually.
Adding NIS Maps to a Zone
To add NIS maps to the NIS Maps parent container in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps For example, if you are using classic zones: domain/UNIX/Zones/ZoneName/NISMaps | On the Object tab, select Allow to apply the following permissions to this object and all child objects: Create Container Objects |
Deleting NIS Maps from a Zone
To delete NIS maps in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps | On the Object tab, select Allow to apply the following permissions: Delete Container Objects applied to this object and all child objects. On the Object tab, set Apply onto to Container objects, then select Allow to apply the following permissions: Delete Subtree Note This permission is required if the map contains any entries. |
Adding Map Entries to NIS Maps
To add entries to any NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps | On the Object tab, set Apply onto to Container objects, then select Allow to apply the following permissions: Create classStore Objects |
Modifying Map Entries in NIS Maps
To modify entries in any NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps | Click the Properties tab, set Apply onto to classStore objects, then select Allow for the following properties: Write adminDescription Write Description Write wWWHomePage |
Changing the Map Type for NIS Maps
To change the map type for any NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps | Click the Properties tab, set Apply onto to This object and all child objects, then select Allow for the following properties: Write Description |
Deleting Map Entries from NIS Maps
To delete entries from any NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for NIS Maps | Click the Properties tab, set Apply onto to classStore objects, then select Allow for the following properties: Write name Write Name |
Adding Entries to a Specific NIS Map
To add entries to a specific NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Individual NIS map | On the Object tab, select Allow to apply the following permissions to this object and all child objects: Create classStore Objects |
Modifying Entries in a specific NIS Map
To modify the entries in a specific NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Individual NIS map | Click the Properties tab, set Apply onto to classStore objects, then select Allow for the following properties: Write adminDescription Write Description Write wWWHomePage |
Changing the Map Type for a Specific NIS Map
To change the map type for a specific NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Individual NIS map | Click the Properties tab, set the Apply onto to This object and all child objects, then select Allow for the following properties: Write Description |
Deleting Map Entries from a Specific NIS Map
To delete entries from a specific NIS map in a zone, the user account must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Individual NIS map | Click the Properties tab, set Apply onto to classStore objects, then select Allow for the following properties: Write name Write Name |
Setting Permissions for Password Synchronization
If you want to use the Network Information Service, adnisd, and the IBM Password Filter to support “agentless” authentication of NIS client requests, the computer that will service the requests must be a member of the zone_nis_servers group in the zone and must be able to access the Active Directory attribute that stores the password hash. The specific permissions required depend on the attribute being used to store the password hash.
IBM Password Synchronization Service
If you are using the IBM Password Filter synchronization service, the zone_nis_servers group requires the following permissions:
| If this attribute is used | These permissions are required |
|---|---|
| altSecurityIndentities | Read altSecurityIndentities |
| msSFU30Password | Read msSFU30Password |
| unixUserPassword | Read unixUserPassword All Extended Rights |
Microsoft Password Synchronization Service
If you are using the Microsoft password synchronization service and the IBM Network Information Service, adnisd, to authenticate NIS client requests, you must set the following permissions at the domain level, on the Users container object, or on another container that applies to all users.
| Select this target object | To apply these permissions |
|---|---|
| Users container or a container that applies to all users | Click the Object tab, set the Apply onto to User objects and select Allow to apply the following permission: All Extended Rights You can apply this permission to Domain Computers or to a specific group of computers that contains the computer where the adnisd service is running. |
For information about installing and configuring a Microsoft password synchronization service, see the Microsoft documentation for that service or refer to documentation on the Microsoft Web site.
Setting Permissions for Rights and Roles
If you define specific rights and establish role-based access controls on a zone-by-zone or computer-by-computer basis, you might want to manually assign permissions for users who can configure rights and roles.
In most cases, you can grant the required permissions to specific users or groups by selecting the appropriate task in the Zone Delegation Wizard instead of assigning the permissions manually.
Creating the Authorization Store
All of the information about rights, roles, and role assignments is held in an authorization store for each zone in Active Directory. The name of authorization store object is CN=Authorization under the zone object’s DN. For example, the authorization store for the zone named EMEA_Territories in the Arcade.Net forest is:
cn=Authorization, cn=EMEA_Territories, cn=Zones, cn=UNIX, dc=Arcade, dc=Net
To create the authorization store for a zone, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Parent container for an individual zone For example, a ZoneName container object, such as: domain/Centrify/Zones/arcade | On the Object tab, select Allow to apply the following permissions to this object and all child objects: List contents Read all properties Read Permissions Select Allow to apply the following permissions to this object only: Create msDS-AzAdminManager objects |
Defining Rights And Roles in the Authorization Store
To configure rights, roles, and role assignments, users must have the following permissions for the authorization store:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | On the Object tab, select Allow to apply the following permissions to this object and all child objects: List contents Read all properties Write all properties |
| msDS-AzApplication This object is listed under a globally unique identifier (GUID) for the Authorization object. For example: CN=cab186af-61a0-4d54-a0dd... | On the Object tab, select Allow to apply the following permissions to this object (listed as CN=GUID under the Authorization object) and all child objects: Create and delete msDS-AzOperation objects Create and delete msDS-AzTask objects Create and delete msDS-AzRole objects Create msDS-AzScope objects Note You must grant these permissions on the CN=GUID object if you are granting permissions manually with ADSI Edit. The proper permissions are set automatically for the users when you delegate administrative tasks for a zone. |
Configuring Authorization In Classic Zones
Unlike hierarchical zones, authorization is an optional feature in classic zones. You must be an administrator or the user who created a classic zone to initialize the authorization store in Active Directory, identify the users who should be allowed to configure rights, roles, and role assignments, and enable or disable the enforcement of the rights and role assignments you have configured.
To update the list of users and groups who are allowed to configure DirectAuthorize rights and roles, you must have the Modify permissions right on the Authorization container under the classic zone container applied to this object and all child objects. If you have this permission, you can click Add to add Windows users and groups to the list of users and groups who can configure rights and roles. If you have the Modify permissions right, you can also select a user or group in the list and click Remove a user or group from the list.
Adding Roles
To add roles for users or groups, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzTaskObjectContainer This object is listed under a globally unique identifier (GUID) for the Authorization object. | On the Object tab, select Allow to apply the following permissions to this object: Create msDS-AzTask objects Click the Properties tab, then select Allow for the following properties: Read objectClass |
Modifying Roles
To modify roles for users or groups, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzTaskObjectContainer/CN=roleName This object is listed under a globally unique identifier (GUID) for the Authorization object and a specific role name. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Read description Read msDS-AzApplicationData Write Name Write name Write description Write msDS-AzApplicationData |
Deleting Roles
To delete roles for users or groups, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzTaskObjectContainer/CN=roleName This object is listed under a globally unique identifier (GUID) for the Authorization object and a specific role name. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Allow Delete |
Adding Rights
To add the definition for a right in a zone, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-OpObjectContainer This object is listed under a globally unique identifier (GUID) for the Authorization object. | On the Object tab, select Allow to apply the following permissions to this object: Create msDS-AzOperation objects Click the Properties tab, then select Allow for the following properties: Read objectClass |
Modifying Rights
To modify right definitions in a zone, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzTaskObjectContainer/CN=roleName This object is listed under a globally unique identifier (GUID) for the Authorization object and a specific role name. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Read description Read msDS-AzApplicationData Write Name Write name Write description Write msDS-AzApplicationData |
Deleting Rights
To delete right definitions in a zone, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzOpObjectContainer/CN=pamrightName or msDS-AzOpObjectContainer/CN=pcrightName This object is listed under a globally unique identifier (GUID) for the Authorization object and a specific PAM access right name or privileged command name. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Allow Delete |
Adding or Removing Rights from Roles
To add or remove rights from a role in a zone, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzTaskObjectContainer/CN=roleName This object is listed under a globally unique identifier (GUID) for the Authorization object and a specific role name. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Read msDS-OperationsForAzTask Write msDS-OperationsForAzTask |
Adding Role Assignments
To add a role assignment, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzRoleObjectContainer This object is listed under a globally unique identifier (GUID) for the Authorization object. | On the Object tab, select Allow to apply the following permissions to this object: Create msDS-AzRole objects |
Modifying Role Assignments
To modify role assignments, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzRoleObjectContainer This object is listed under a globally unique identifier (GUID) for the Authorization object. | On the Object tab, select Allow to apply the following permissions to this object: Create msDS-AzRole objects |
| msDS-AzRoleObjectContainer/CN=CRA_guid This object is listed under a globally unique identifier (GUID) for the Authorization object and a unique identifier for the role assignment. | Click the Properties tab, then select Allow for the following properties to allow changes to the assigned user or groups: Read Name Read name Allow Delete Click the Properties tab, then select Allow for the following properties to allow changes to the available time for a role assignment: Read Name Read name Read msDS-AzApplicationData Write msDS-AzApplicationData |
Deleting Role Assignments
To modify role assignments, users must have the following permissions:
| Select this target object | To apply these permissions |
|---|---|
| Authorization | Click the Properties tab, then select Allow for the following properties: Write msDS-AzApplicationData |
| msDS-AzRoleObjectContainer/CN=CRA_guid This object is listed under a globally unique identifier (GUID) for the Authorization object and a unique identifier for the role assignment. | Click the Properties tab, then select Allow for the following properties: Read Name Read name Allow Delete |
Setting Permissions for Zone Provisioning
The Zone Provisioning Agent requires permission to create UNIX profiles, that is, the service connection points in each zone where it needs to perform provisioning operations. The service account that runs the Zone Provisioning Agent requires the Log on as a service right set as a local computer security policy, or in the default domain policy.