Before Install: Prerequisites
For the full set of platform requirements, please visit this web page in the IBM Security Technical Support area:
https://support.delinea.com/s/
Supported Versions of SQL Server and SSRS
To use IBM Security report services, you need to use a SQL Server that is one of the following versions:
- SQL Server 2008 R2
- SQL Server 2012
- SQL Server 2012 R2
- SQL Server 2014
- SQL Server 2016
- SQL Server 2019
For Microsoft SSRS, use the version that correlates with your SQL Server version. For example, if you're using SQL Server 2012 R2, then use Microsoft SSRS version 2012 R2.
If you choose to use a version of SQL Server that requires .NET version 3.5 SP1, be sure to install .NET before configuring report services.
If you run Report Services with Microsoft SQL Server 2012 Service Pack 2 and Visual Studio 2010 on the same system, please update Visual Studio 2010 to Service Pack 1. (Ref: CS-38553a)
Supported Versions of PostgreSQL
IBM Security Report Services works with PostgreSQL databases that are version 11 or later.
Supported Browser Versions
Use the web browser versions that Microsoft supports for use with SQL Server Reporting Services, as mentioned in this page:
https://msdn.microsoft.com/en-us/library/ms156511.aspx
For Internet Explorer, the version of SQL Server and SQL Server Reporting Services (SSRS) that you use also determines which version of Internet Explorer is compatible with your deployment. Please consult the IBM Security Knowledge Base article KB-6671 for details about which version of Internet Explorer you should use.
Required User Permissions for Report Services
Before you install IBM Security report services, be sure you have the appropriate software and user accounts, which includes the following:
- Users with required permissions. Before installation, you must have users to run the IBM Security installer.
- Report service account
- SQL Server service account (this is needed if you're installing using an existing instance)
-
User accounts that can run the Report Configuration Wizard and the Reporting Control Panel.
There are a few user accounts that you need to set up for use with IBM Security report services. Here
is a summary of the user accounts that you need to create and the permissions you need to explicitly grant.
Report Services Account Permissions
| User type | Required Active Directory permissions | Required security policy permissions(group policy, or local policy) | Required SSRS permissions | Required SQL Server or PostgreSQL permissions |
|---|---|---|---|---|
| report service account to run the Reporting Service | For domain-based reporting: Replicating directory changes at the domain level (ADUC) and replicate directory changes in ADSI For zone-based reporting: Read permission |
Log on as a service | ||
| SQL Server service account to run SQL Server | n/a | Log on as a service | member of the securityadmin role | |
| PostgreSQL service account | the account must have permission to connect to PostgreSQL and create a database | |||
| report admin to run the Report Configuration wizard or the Upgrade & Deployment wizard and deploy reports to an existing SQL Server instance | needs to be a member of the domain | n/a | Folder Settings > Content Manager role | member of the securityadmin role (At the very least, the user needs permission to connect to SQL Server and create a database.) |
| report admin to modify the Reports Control Panel | Read permission to the domain root object of the selected domain. Read permission to all computer objects in the selected domain. | n/a | ||
| Report viewer to view reports from SSRS/Internet Explorer | Site settings > System user role Folder settings > browser (assign SSRS roles to Active Directory group or users) | |||
| Report writer read, write, edit access for reports, in addition to the permissions needed to view reports | Site settings > System user role Folder settings > Content Manager role (assign SSRS roles to Active Directory group or users) |
IBM Security Report Services requires administrator permission to install and upgrade. That also means that only an administrator can uninstall and repair IBM Security Report Services. (Ref: CS-40808a)
Grant the Report Service Account Permissions
For your convenience, below are reminders for how to grant the two sets of required permissions for the report service account.
Grant the Permission to Replicate Directory Changes in ADUC
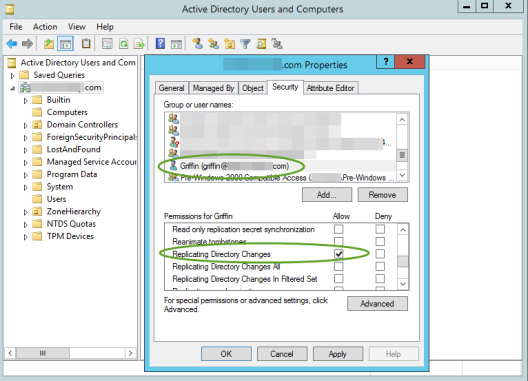
To grant the permission to replicate directory changes at the domain level (read only):
-
Open Active Directory Users and Computers.
-
From the View menu, select Advanced Features.
-
Right-click the domain object and select Properties.
-
Click the Security tab.
-
Select the desired user account (add the account if it's not listed there already).
-
In the Permissions area, next to Replicating Directory Changes, click Allow.
-
Click OK to save your changes.
For more information about setting this permission, see https://support.microsoft.com/en-us/kb/303972.
Grant the Permission To Replicate Directory Changes In ADSI
In addition to granting the replicate directory changes permission in Active Directory Users and Computers (ADUC), you also need to grant the same permission in the ADSI Edit (Active Directory Services Interfaces Editor) console.
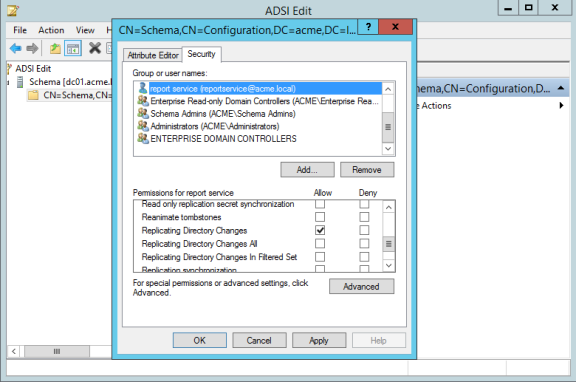
To grant the permission to replicate directory changes in ADSI (read only):
-
Open the ADSI Edit console.
-
From the Action menu, select Connect to.
The Connection Settings dialog box opens.
-
For the Connection Point, go to the "Select a well known Naming Context" drop-down menu and select Schema.
-
Click OK to close the dialog box.
The schema for the current domain displays in the ADSI Edit console.
-
Expand the schema listing so that you can see the first node of the schema, and right-click that node and select Properties.
The Attribute Editor dialog box opens.
-
Click the Security tab.
-
Select the desired user account (add the account if it's not listed there already).
-
In the Permissions area, next to Replicating Directory Changes, click Allow.
-
Click OK to save your changes.
Grant the Permission to Log on as a Service
To grant the log on as a service permission:
-
In the Group Policy Management Editor, apply the following policy to your desired user or group of users:
Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment > Log on as a Service.
For more details about granting the log on as a service policy, see https://technet.microsoft.com/en-us/library/dn221981(v=ws.11).aspx.
SQL Server permissions that are set by the Configuration Wizard
Here are the SQL server permissions that report services grants to each user type, for your information. The Report Services Configuration wizard sets these permissions automatically.
Sql Server Permissions Set by the Report Services Configuration Wizard (table)
| User type | Required SQL Server permissions |
|---|---|
| report services account to run the SQL Server Reporting Service | Snapshot Service (predefined role) |
| SQL Server service account to run SQL Server | If you deploy to an existing SQL Server instance, the configuration wizard makes no changes to the SQL Server service account. If you deploy to a new SQL Server instance: --If the operating system is Windows 2008 and you're using a SQL Server version later than 2012, virtual accounts are used for various SQL Server components, as follows: SQL Server engine: NT SERVICE\MSSQL$<InstanceName> SQL Server Agent: NT SERVICE\SQLAgent$<InstanceName> Full text search: NT SERVICE\MSSQLFDLauncher$<InstanceName> SSRS: NT SERVICE\ReportServer$<InstanceName> --Otherwise, the SQL Server service accounts are configured as follows: SQL Server engine: NT Authority\Network Service SQL Server Agent: NT Authority\Network Service Full text search: NT Authority\Local Service SSRS: NT Authority\Local Service |
| report admin to run the Report Configuration Wizard and deploy reports to an existing SQL Server instance | Connect SQL (cannot be revoked after setup) Create Database, Create any database, or Alter any database member of securityadmin role, or Alter any login permission |
| report admin to modify the Reports Control Panel | SnapshotAdmin (predefined role) |
| Report viewer to view reports from SSRS/Internet Explorer | Login permission SnapshotViewer (predefined role) |
| Report writer read, write, edit access for reports, in addition to the permissions needed to view reports | Login permission SnapshotViewer (predefined role) |
Microsoft SQL Server Reporting System (SSRS) affords only role-based security in their reports. Be sure to grant appropriate access to reports. For example, if a user has access to only some data in the specified domain but all reports, they will be able to view all reports on all data from Active Directory.
PostgreSQL Permissions that are Set by the Configuration Wizard
When you create the PostgreSQL database with the Configuration wizard, the wizard grants the administrator user one permission for Create Database.
Memory Requirements
Be sure that your computers running the following components meet or exceed the RAM requirements listed below.
Domain Controller Memory Requirements
The minimum amount of RAM that you should have available for your domain controller is the sum of the following:
- Active Directory database size (for example, C:\Windows\NTDS\)
- Total SYSVOL size (for example, C:\Windows\SYSVOL)
- Recommended amount of RAM for your operating system
-
Vendor recommended amount of RAM for your various background software agents, such as anti-virus,
monitoring, backup, and so forth.
- Additional RAM to accommodate growth over the lifetime of the server.
For more information, see Microsoft recommendations here: http://social.technet.microsoft.com/wiki/contents/articles/14355.capacity-planning-for-active-directory-domain-services.aspx.
Windows Memory Requirements
Here are the minimum and recommended memory requirements for report services and the report database:
- IBM Security report services: minimum 2 GB RAM, recommended 4 GB or above
- SQL Server report database: minimum 4 GB RAM, recommended 32 GB or above
- PostgreSQL report database: minimum 4 GB RAM, recommended 32 GB or above
SQL Server Recovery Model Requirement
In order for report services to function efficiently, it's recommended that you configure your SQL Server database to use the Simple recovery model. The recovery model configuration determines how SQL Server logs transactions, whether a database backs up the transaction log, and what kinds of restore options are available.
For more information about recovery models, please visit https://msdn.microsoft.com/en-us/library/ms189275.aspx.
To configure the SQL Server database recovery model:
- In SQL Server Management Studio, navigate to the database that you use for report services.
- Right-click the database and select Properties.
- In the Select a Page area, click Options.
- For the Recovery Model option, select Simple.
- Click OK to save the changes.
Impact of Using a New or Existing SQL Server Instance
When you set up your installation of IBM Security report services, you have the option of either using an existing SQL Server instance or installing a new instance. IBM Security recommends that you use a new SQL Server instance, if possible.
If you choose to install a new instance from the IBM Security Management Services installer program, the program installs an instance of SQL Server Express 2008 R2 with Advanced Services.
If you have an existing installation of SQL Server, you can create a new instance there first on your own, using your own installation media. When you install or configure IBM Security report services, you then configure report services to use your existing instance that you created. That way, your SQL Server instances use the same edition and version.
Tip: Please see the information at the following link for details about installing multiple versions and instances of SQL Server:
https://msdn.microsoft.com/en-us/library/ms143694(v=sql.130).aspx
Here are some issues to be aware of if you're going to use a new SQL Server instance:
-
With a new SQL Server instance, you can avoid any potential problematic issues with SSRS,
particularly if you need to reinstall SSRS.
- SSRS won't slow down the regular database operations on other instances.
-
To prevent the SQL Server instance from consuming too much memory, it's recommended to use the
max server memory to control each SQL Server instance's memory usage. The total allowance is
not more than the total physical memory on the machine. If user is not running all of the
instances, none of the running instances will be able to utilize the remaining free memory.
Here are some issues to be aware of if you're going to use an existing SQL Server instance:
-
There can be issues with SSRS and existing instances. If you have to uninstall and reinstall SSRS,
it leaves files behind with the existing instance.
-
Using an existing SQL server instance can use all the free memory with a larger limit of the
max server memory setting.
If you choose to deploy report services using an existing instance of SQL Server, your database administrator may need to know what changes that report services needs to make to the database. (KB-8042)
The only modification that report services makes to an existing database instance is to add two Windows integrated logins, as follows:
| Login | Granted database role for the Report Service database |
|---|---|
| <The specified service account> | SnapshotService |
| [NT Authority\Authenticated Users] | SnapshotViewer |
If these logins already exist, report services does not re-create them.
Deploy in Multi-Forest Environments
If you're deploying report services across multiple forests, there are a few tips to be aware of.
-
It is best to install report services once in a forest, and then monitor domains or zones in other trusted forests.
-
If you use domain-based mode, you need to install report services once in the domain. Make sure that any users who run report services and the service account have access to the domains for which you want to run reports.
If you need to grant access to a user account across a forest with a one-way selective trust, you enable selective authentication for that user.
Enable Selective Authentication Across a Forest with a One-Way Selective Trust
The instructions below are provided as a courtesy; for more information on selective authentication, see the following article:
https://technet.microsoft.com/en-us/library/cc794747(v=ws.10).aspx
How to enable selective authentication for a user across an Active Directory forest that has a one-way selective trust:
- Open Active Directory Domains and Trusts.
- In the console tree, right-click the domain node for the forest root domain, and then click Properties.
- On the Trusts tab, under either Domains trusted by this domain (outgoing trusts) or Domains that trust this domain (incoming trusts), click the forest trust that you want to administer, and then click Properties.
- On the Authentication tab, click Selective authentication, and then click OK.
- Open Active Directory Users and Computers.
- Navigate to the Domain Controller the Report Services will use, right-click the computer object, and then click Properties.
- On the Security tab add the desired user and grant Allow for the Allowed to authenticate permission.
See also the IBM Security knowledge base article KB-8071.
Virtual Machines and Report Services
For production deployments, it is recommended to avoid using virtual machines for use with report services. (KB-7038)
In general, report services works well in virtual machines, including the case of installing SQL Server in a virtual machine.
However, in a large enterprise environment (such as where more than 100,000 users are enabled for authentication service), the SQL queries used for generating reports may have significant CPU, memory and I/O requirements. In these situations, IBM Security recommends the use of physical computers for SQL Server to allow for better tuning of SQL Server without impacting other systems.
Alternatively, you can install SQL Server in a virtual machine. In such cases, IBM Security recommends that you follow the guidelines provided by the virtualization vendors:
https://www.vmware.com/docs/sql-server-on-vmware-best-practices-guide