Proxied Environments
If your Verify Privilege Vault has outbound access through a proxy, its web.config must be modified to specify the proxy configuration.
-
If Verify Privilege Vault is also clustered and has multiple worker roles enabled (see the Background Worker article), the web.config must be updated for each Verify Privilege Vault in the cluster.
Microsoft has more information on this.
For more information about using a distributed engine through a proxy, please refer to the Verify Privilege Vault documentation.
The other option in a clustered environment is to specify a remote site for the data upload, and upload data through a Distributed Engine. If the distributed engine’s host server is also behind a proxy, however, the engine’s IBM SecurityDelinea.DistributedEngine.Service.exe.config must be modified similarly to the web.config in order to specify the proxy settings.
-
For Verify Privilege Vault v10.4 or later, the web-proxy.config can be uncommented and updated to specify the proxy settings.
For Verify Privilege Vault v10.3.000015 or earlier, you must add proxy-related XML to the web.config file immediately following the file’s closing \</configSections\> tag, as depicted here:
Copy</configsections>
<system.net>
<defaultproxy enabled="true" usedefaultcredentials="true">
<proxy usesystemdefault="false" proxyaddress="https://proxy:port" bypassonlocal="true"/>
</defaultproxy>
</system.net>
<configuration type="thycotic.foundation.configuration, thycotic.foundation">
Using Webnode with Proxied Environments
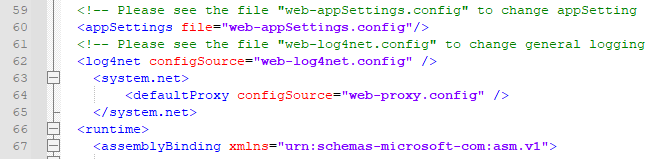
If you are using a webnode, you will need to add the following code:
<system.net>
<defaultProxy configSource="web-proxy.config" />
</system.net>Example:
Distributed Engine (DE) Configuration
IBM Security suggests that you review any exception in the proxy configuration for both web nodes and DEs as a bypass. The configuration files may be overwritten with product updates and changes will be need to be reviewed, and possibly implemented again.
When Verify Privilege Vault and DEs are behind a proxy, certain settings need to be added to webnodes and DEs if they exist in the environment.
To use with the Distributed Engine through a proxy, you will need to add proxy info to IBM Security.DistributedEngine.Service.exe.config between </system.serviceModel> and located in the C:\Program Files\Thycotic Software Ltd\Distributed Engine\ folder on the distributed engine. You may need to refer to this article for other proxy related settings:
For more information about using a distributed engine through a proxy, please refer to the Verify Privilege Vault documentation.
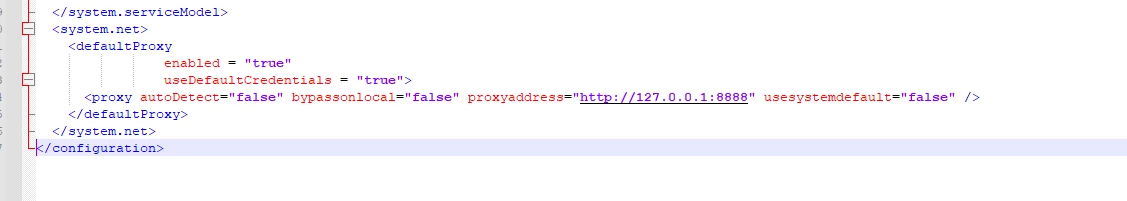
<system.net>
<defaultProxy>
<proxy usesystemdefault="true" />
</defaultProxy>
</system.net>
You will need to restart the DE service after this update and the setting will need to be reapplied after any DE upgrade.
Webnode Configuration
Main Proxy settings are stored in the web-proxy.config file in the Verify Privilege Vault folder on each webnode. Microsoft’s article on Proxy configuration explains all settings.
Example #1
<?xml version="1.0" encoding="utf-8" ?>
<defaultProxy enabled="true">
<proxy
usesystemdefault="true"
proxyaddress="http://192.168.1.1:8080"
bypassonlocal="true"
/>
</defaultProxy>Example #2
<defaultProxy enabled="true">
<proxy proxyaddress—"http://proxy.domain.com:80" bypassonlocal-"true" / >
</defaultProxy>Now, the following files need to be edited to point to the web-proxy.config file.
-
web-embeddedRole-backgroundScheduler.config
-
web-embeddedRole-backgroundWorker.config
-
web-embeddedRole-engineWorker.config
-
web-embeddedRole-messageBroker.config
-
web-embeddedRole-sessionRecordingWorker.config
The code used in these files can be as follows:
<system.net>
<defaultProxy configSource="web-proxy.config" />
</system.net>
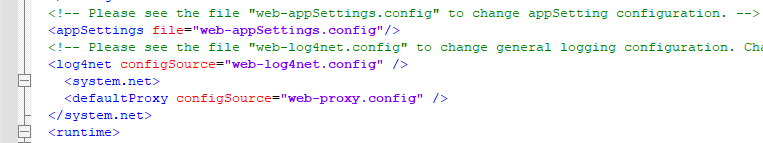
Placement of this setting may effect connection. Make sure this setting is placed before the <runtime> element has been confirmed to make the configuration work.
VP-VA Troubleshooting Tips
Search logs files for “Analytics” or “Amazon,” as VP-VA integration reaches out to AWS and often you can find log entries specifically mentioning AWS connection issues.
DEs
Check the SSDE.log file.
Example:
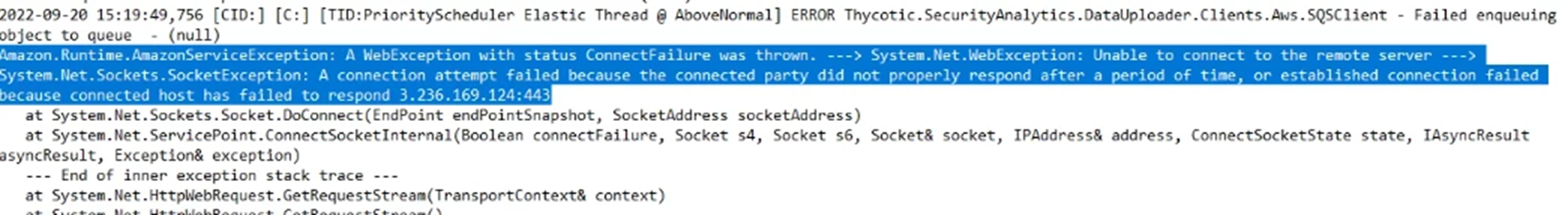
Webnodes
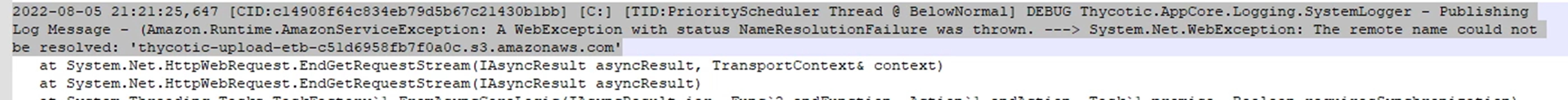
Check the SS-BWSR.log file
Example:
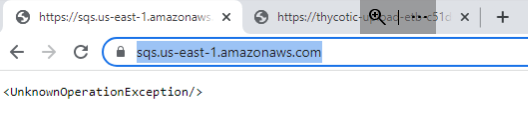
Check to see if the machine can pull up the IP/URL in the logs in web browsers. While these do not specifically show full communication between systems, they can help narrow down the issue.
Example #1:
Example #2: