Configuring Integrated Windows Authentication
Introduction
Integrated Windows Authentication (IWA) allows users to log into Verify Privilege Vault automatically if they are logged into a workstation with their Active Directory credentials.
The SDK is designed to be used as it is shown below and is not designed to be run using IWA to retrieve tokens or Secret information. Given this, the SDK is not supported with IWA.
Setting Up Windows Authentication
Task 1: Configuring Verify Privilege Vault
-
Log into Verify Privilege Vault as a user with Active Directory administration privileges.
-
Navigate to and click Administration > Directory Services (In the General section). The Directory Services page appears, opened to the Domains tab.
-
Click the Add Domain button and select Active Directory Domain or Azure Active Directory Domain. An Active Directory popup appears.
-
If you chose Active Directory Domain:
- Type your FQDN in the Fully Qualified Domain Name text box.
- Type the name for people to read in the Friendly Name text box.
- Click to select the Active check box.
- If you wish to use secure LDAP, click to select the Use LDAPS check box.
- Click the Create New Secret link under Synchronization Secret. A popup appears.
- Click Active Directory Account in the Choose a Secret Template dropdown list. A Create New Secret popup appears.
- Fill in the popup with your desired parameters for your AD secret.
- Click the Create Secret button. The popup disappears and the secret name appears on the previous popup.
- Click the Site dropdown list to select your desired site.
- Click the Multifactor Authentication dropdown list to select your desired type of MFA, if any.
- Click the Validate & Save button to commit your choices. The popup disappears and your directory service appears in the table on the Directory Services page.
-
If you chose Azure Active Directory Domain:
- Type your name for people to read in the Domain Name text box.
- Click to select the Active check box.
- Type your tenant ID in the Tenant ID text box.
- Type your client ID in the Client ID text box.
- Type your client password in the Client Secret text box.
- Click the Multifactor Authentication dropdown list to select your desired type of MFA, if any.
- Click the Validate & Save button to commit your choices. The popup disappears and your directory service appears in the table on the Directory Services page.
-
Click the Configuration tab.
-
Click the Edit button in the Directory Services section. The section becomes editable.
-
If necessary, click to select the following check boxes:
- Enable Directory Services
- Enable Integrated Windows Authentication.
-
Click the Save button.
-
Click the Edit button in the User Synchronization section. The section becomes editable.
-
Ensure the Enable User Synchronization check box is selected.
-
Type the in the Days, Hours, and Minutes text boxes to choose a synchronization interval, which is how often Verify Privilege Vault pulls in users from AD.
-
Select your desired option from the User Account Options dropdown list.
-
Select how to handle inactive users in the Automatic User Management dropdown list.
-
Type your desired number of days in the Days to Keep Operational Log text box.
-
Click the Save button. The Active Directory Configuration page returns to being read only.
-
Click the Domains tab.
-
Click the Synchronize Now button. This pulls all the users of the specified groups into Verify Privilege Vault.
Task 2: Configuring IIS
-
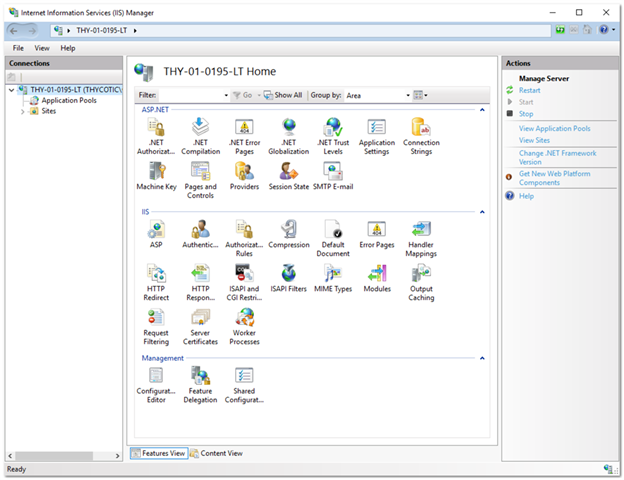
Start the Internet Information Services (IIS) Manager.
-
Navigate to and select your Verify Privilege Vault website in the Connections tree:
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Enable the Windows Authentication parameter by right-clicking it and selecting Enable. For now, ignore the alert if it appears in the Alert section.
If Windows Authentication is not visible, ensure that the Windows Authentication Role service is enabled in Windows. This is different than earlier versions. -
Disable the Anonymous Authentication.
-
Disable the Forms Authentication. The alert in the Alert section should disappear.
-
When finished, the Authentication settings should only have Windows Authentication enabled.
-
Restart your IIS server with an
iisresetcommand. -
On the Verify Privilege Vault folder, ensure users have read or higher permission, and ensure the security settings are set to be inherited by child objects. Because Verify Privilege Vault impersonates those users, they require access to Verify Privilege Vault files.
-
Log in to the Verify Privilege Vault site from an authenticated workstation.
Task 3: Configuring Verify Privilege Vault Launchers
By default, a launcher will not work when using IWA, resulting in an HTTP 401: Unauthorized error. If this is an issue, ensure Verify Privilege Vault is on Windows Server 2008 or later and complete the following steps:
-
Open IIS and browse to your Verify Privilege Vault application.
-
Click the > to see the application's folders.
-
Click to select the launchers folder. The launchers Home panel appears.
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure the Windows Authentication is set to Disabled.
-
Ensure all others are disabled. When you are finished, the settings should have Anonymous Authentication enabled.
-
Click the webservices folder.
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure the Windows Authentication is set to Disabled.
-
Ensure all others are disabled. When you are finished, the settings should have Anonymous Authentication enabled
-
Click the rdp folder.
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure the Windows Authentication is set to Disabled.
-
Ensure all others are disabled.
Task 4: Configuring Distributed Engines
Similarly, Verify Privilege Vault with distributed engines will not work with IWA by default. If this is an issue, complete the following:
-
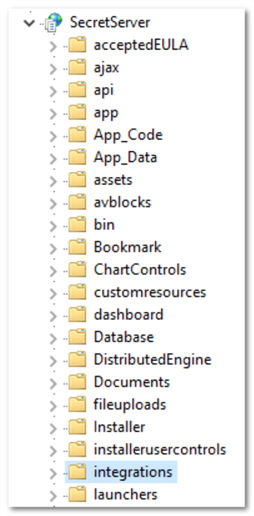
In Windows Explorer, navigate to the
…\SecretServer\folder. This folder is mapped to yourSecretServerfolder in your webserver. -
Create a subfolder named
…\SecretServer\integrations. -
Create a subfolder called
…\SecretServer\apiin the same location. -
In your
…\SecretServer\apifolder, create a subfolder named…\SecretServer\api\DistributedEngine. -
Start IIS Manager:
-
Navigate the Connections tree back to integrations folder in the SecretServer node:
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure the Windows Authentication is set to Enabled.
-
Ensure all others are disabled.
-
Navigate to the
…\SecretServer\api\DistributedEnginefolder. -
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure the Windows Authentication is set to Disabled.
-
Ensure all others are disabled.
Task 5: Configuring Disaster Recovery
Similarly, Verify Privilege Vault Disaster Recovery will not work with IWA by default. If this is an issue, complete the following:
-
In Windows Explorer, navigate to the
…\SecretServer\folder. This folder is mapped to yourSecretServerfolder in your webserver. -
Create a subfolder named
…\SecretServer\integrations. -
Start IIS Manager:
-
Navigate the Connections tree back to integrations folder in the SecretServer node:
-
Double-click the Authentication icon in the IIS section to open the Authentication pane.
-
Ensure the Anonymous Authentication is set to Enabled.
-
Ensure all others are disabled.
Task 6: Configuring Client Certificates
If you are using client certificates, configure the following in IIS for launchers to work:
-
Click to select the launchers folder. The launchers Home panel appears.
-
Double-click the SSL Settings icon. The settings panel appears.
-
Click to set the Client Certificates selection button to Accept.
-
A dialogue box requiring a yes response pops up.
-
Click Yes.
-
Click to select the Webservices folder.
-
Once again, double-click the SSL Settings icon.
-
This time, set the Client Certificates selection button to Ignore.
If you are not automatically logged in to Verify Privilege Vault after setting up IWA, IIS may not be handling the credentials correctly. To fix this, recreate the web site in IIS.
When testing IWA, keep in mind the requirements at Your Browser May Prompt You for a Password.
You may not be able to log in using IWA on the server running Verify Privilege Vault for Server 2008 or later because of security settings.
Troubleshooting
AD User Prompted for Credentials Even Though IWA Is Active
A user is logged onto their machine with the same Active Directory credentials they can log into Verify Privilege Vault with, but the browser still prompts them for their credentials to reach the site. Ensure your Verify Privilege Vault site is included in a security zone that allows for automatic logon:
-
In your browser, go to Internet Options > Security.
-
Click the Trusted Sites security zone.
-
Click the Custom Level button. The Security Settings – Trusted Sites Zone dialog box appears.
-
Scroll down to User Authentication.
-
Click to select the Automatic logon with current user name and password selection button.
-
Click the OK button.
Logging in as a Local Account Is Not Available
In Verify Privilege Vault 10.0 and later, Verify Privilege Vault requires Integrated Mode in IIS. The Integrated Mode can only support either Window Authentication or Forms Authentication (used for local account authentication), not both. Because of this limitation, Forms Authentication must be disabled for the site when using Integrated Windows Authentication. Thus, logging in as Verify Privilege Vault local account is not available when IWA is enabled.
Installing Windows Authentication in Windows Server 2012 Manager
-
In Server Manager, click the Manage menu and select Add Roles and Features. The Add Roles and Features wizard appears.
-
Click the Next button. The Select installation type window appears.
-
Select the installation type.
-
Click the Next button. The Server selection window appears.
-
Select the destination server.
-
Click the Next button. The Server roles window appears.
-
Click to expand Web Server (IIS) > Web Server > Security.
-
Click to select Windows Authentication.
-
Click the Next button. The Select features window appears.
-
Click the Next button. The Confirmation window appears.
-
Click the Install button. The Results window appears.
-
Click the Close button.