Creating Discovery Rules
Introduction
Verify Privilege Vault discovery rules play a pivotal role in automating the process of finding, importing, and managing passwords, API keys, and other credentials throughout an IT environment.
Discovery rules offer several advantages:
-
Automated Discovery: Discovery rules simplify identifying potential secrets across various platforms and environments, ensuring that no sensitive credentials remain unmanaged or unprotected.
-
Policy Enforcement and Risk Reduction: Discovery rules help enforce consistent security policies across an IT environment. This consistency is crucial for minimizing security breaches and ensuring compliance with regulatory standards.
-
Efficient Secret Management: Discovery rules reduce the administrative burden on IT teams by automating secret candidate discovery and importation.
-
Dynamic Adaptation: Discovery rules help to flexibly adapt to IT environments, which are constantly changing with the addition of devices and applications.
isvp-vault offers a feature related to discovery rules that allows you to see what accounts would match a rule. This is part of the discovery process where discovery rules are used to automate the identification and management of credentials across various platforms. Here's how it works:
-
Discovery Account Rules: These rules are search queries against the accounts found by discovery. When these rules are created and run, accounts that match the rules can be automatically imported as secrets. This means you can define criteria for accounts, and the system will identify which accounts matches these criteria.
-
Viewing Discovery Results: After running a discovery scan, you can view the results in the Discovery Network View. This view allows you to see which accounts have been discovered and whether they match any existing rules. You can filter and search through these results to identify specific accounts that meet the criteria set by your discovery rules.
Creating Local Account Rules
Discovery account rules are search queries against the accounts found by discovery, visible in the Discovery Network View. When these rules are created and run, accounts that match the rules can be automatically imported as secrets. When matches are found, email notifications can also be sent out.
The rule order determines the rule application order. Drag rules to reorder them. Rules can specify a combination of the domain or OU, the computer name and the account name.
To create a rule:
-
Select Discovery. The Discovery Analysis tab of the Discovery page appears.
-
Select the Network View tab.
-
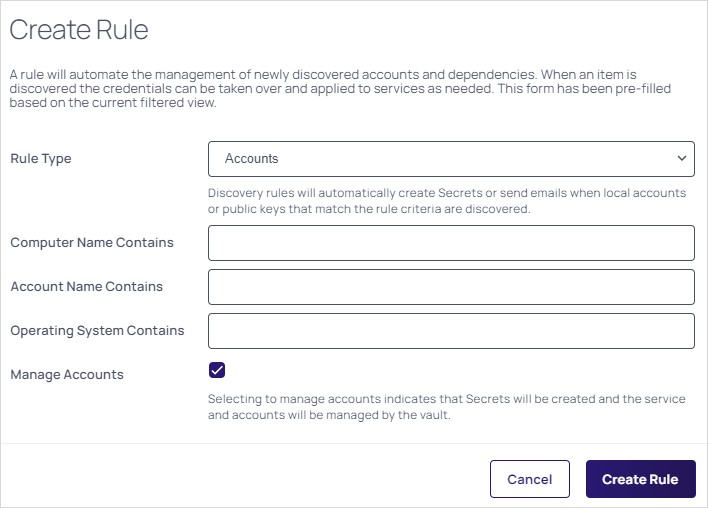
Click the Create Rule button. The Create Rule popup appears:
-
From the Rule Type dropdown list, select Accounts.
-
(Optional) Type in text strings for the following if you want to limit the scope of the rule:
-
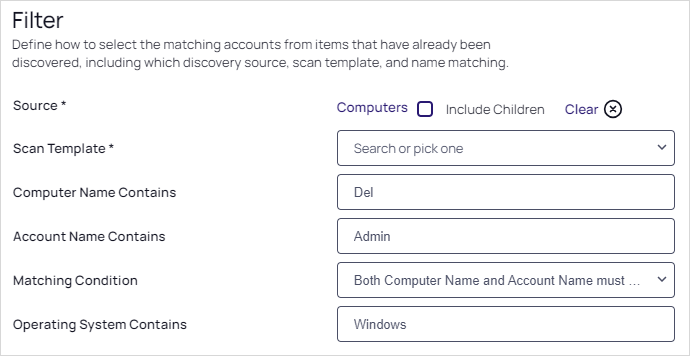
Computer Name Contains
-
Account Name Contains
-
Operating System Contains
For this example,
Del,Admin, andWindowshave been entered.Discovery rules automatically create secrets or send emails when local accounts or public keys that match the rule criteria are discovered. -
-
Select the Manage Accounts checkbox if you want secrets to be created and the service and accounts to be managed by Verify Privilege Vault.
-
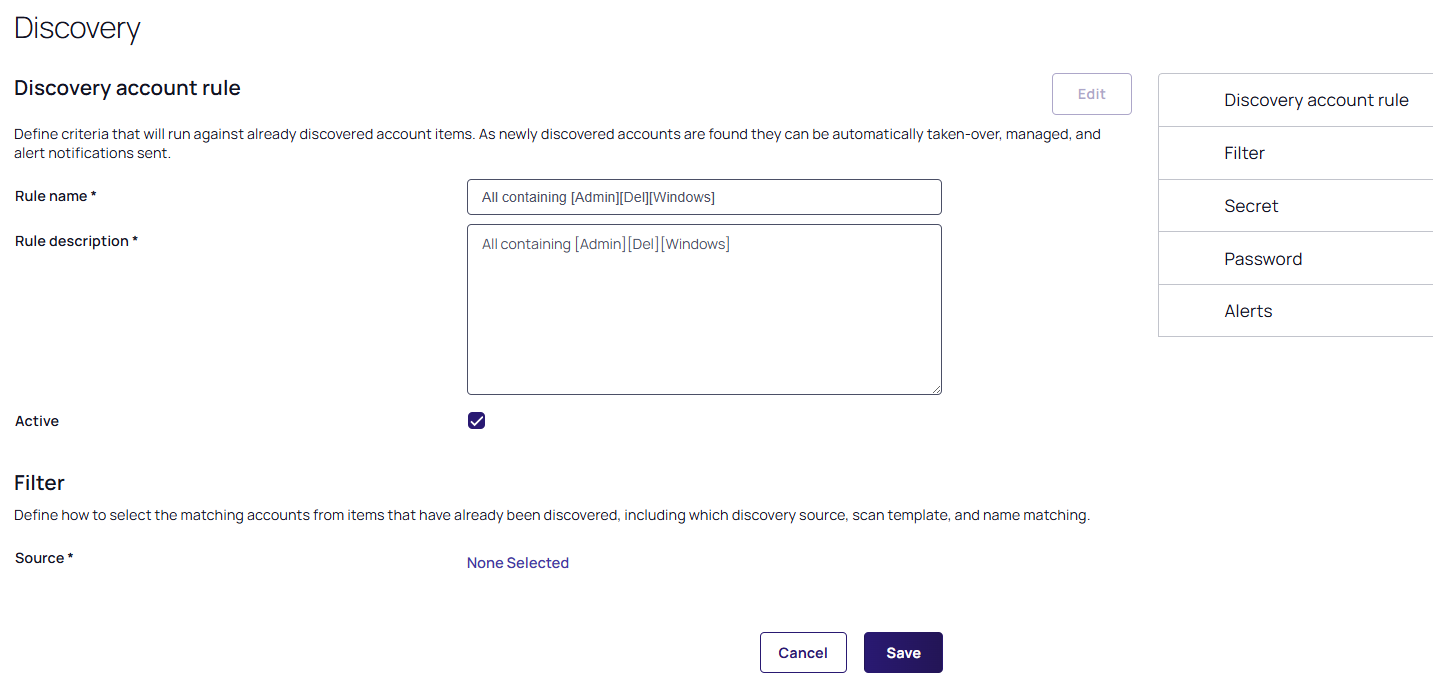
Click the Create Rule button. The Discovery account rule page appears with the values you typed:
-
Type the name of the new rule in the Rule Name textbox if you want to change the suggested name.
-
Click the None Selected link in the Filter section to choose a discovery source. The Pick OU popup appears.
-
Navigate to and select the OU of your choice, this appears as your source. Additional controls also appear, which differ with each source. For this example the following source was used:
-
Select the Include Children checkbox if you want to include any child OUs in the scan.
-
From the Scan Template dropdown list, select an output template. The Secret and Alerts sections appear below the Filter section.
-
From the Matching Condition dropdown list, pick which of the filtering parameters must match.
The completion checklist updates to show that you completed the Filter section. -
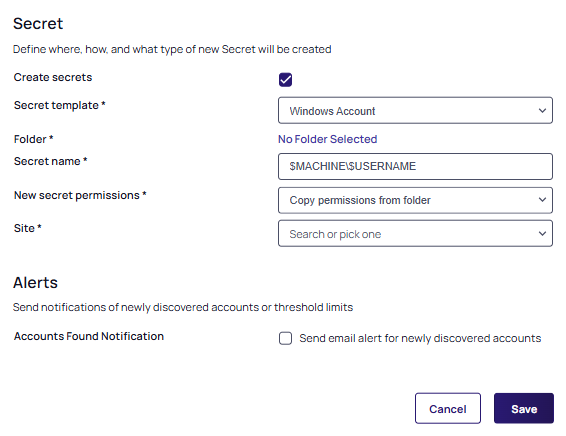
Scroll to the Secret section:
-
The Create Secrets checkbox is selected by default.
-
From the Secret Template dropdown list, select the secret template the new secret will originate from if a default is not available automatically.
-
Click the Folder link to select a folder for the new secret to belong to.
You cannot use personal folders for this purpose. -
Type the naming convention for the new secret in the Secret Name text box.
A naming convention is automatically suggested based on the hostname and username, such as$DOMAIN\$USERNAME. -
From the New Secret Permissions dropdown list, select whether you want secrets to copy (standalone) or inherit (change with the folder) the permissions from the folder.
-
From the Site dropdown list, select the Verify Privilege Vault local installation or a distributed engine to run the rule from. The Password Section appears.
The completion checklist updates to show that you completed the Secret section. -
Scroll to the Password section:
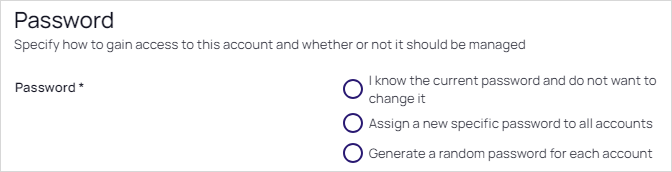
Remote password changing must be enabled to change the password. -
Select the I know the current password… option if you do not want Verify Privilege Vault to change the account password when the secret is created.
Complete the following:
-
In the Current Password text box, type the password.
-
Leave the Password Changing dropdown list set to Use privileged account.
-
Click the No Secret Selected link to choose a secret for the privileged account for ongoing use.
-
-
Select the Assign a new specific password to all accounts option if you want all the new secrets to have the same password, which you can later change.
Complete the following:
This option will change the password on the remote machine for any newly discovered accounts.-
(Optional) Type a value in the Takeover Threshold text box.
If the number of accounts that will be taken over exceeds the maximum threshold, the import is canceled and the subscribed users are notified by email. -
Type the new password in the New Password text box.
-
From the Password Type dropdown list, select the desired type.
-
For Initial Takeover Secrets, you have the option of selecting the No Secret Selected link and choosing a secret for the privileged account for the initial takeover.
Or if you want to have a set of secrets that can be tried until one works, click the (Switch to Multiple Reset Secrets) link, and select Add Secret to choose a secret. The name of the secret appears. Repeat as needed. -
Leave the Password Changing dropdown list set to Use privileged account.
-
For Password Changing Privileged Account, click the Add Secret button to choose a secret or secrets for the privileged account for ongoing use.
-
-
Select the Generate a random password for each account option if you want to have Verify Privilege Vault create a strong password for the secret.
This option will change the password on the remote machine for any newly discovered accounts.-
(Optional) Type a value in the Takeover Threshold text box.
If the number of accounts that will be taken over exceeds the maximum threshold, the import is canceled and the subscribed users are notified by email. -
From the Password Type dropdown list, select the desired type.
-
For the Initial Takeover Secrets, click the Add Secret button to choose a secret or secrets for the privileged account.
-
Leave the Password Changing dropdown list set to Use privileged account.
-
For Password Changing Privileged Account, click the Add Secret button to choose a secret or secrets for the privileged account for ongoing use.
Note that the completion checklist updates with a check mark to show that you completed the Password section.
-
-
Scroll to the Alerts section:
-
Select the Send email alert for newly discovered accounts checkbox to enable the Subscribed Users dropdown list.
-
From the Subscribed Users dropdown list, select one of the following:
-
Discovery Administrators, if you only want to notify admins.
-
Specific Users, if you want to define a list of people to notify.
-
-
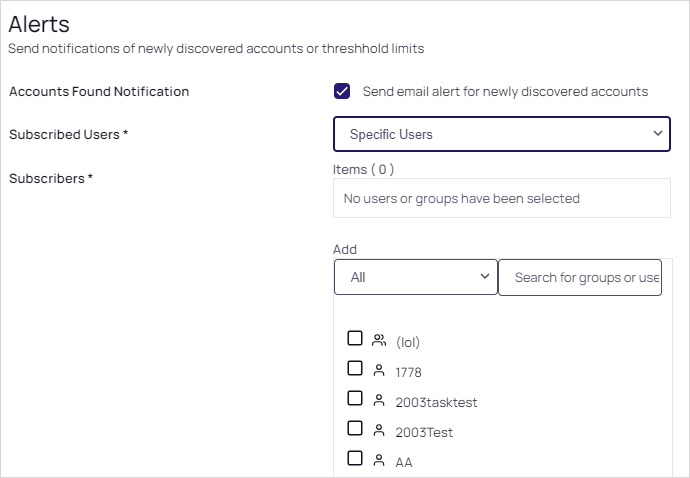
If you chose Specific Users, new controls appear:
-
In the Add section, select or search for users and groups. As you click each one, they appear in the Items text box.
The completion checklist updates to show that you completed the Alerts section. -
Select Save at the bottom of the page to keep your changes.
Creating Dependency Rules
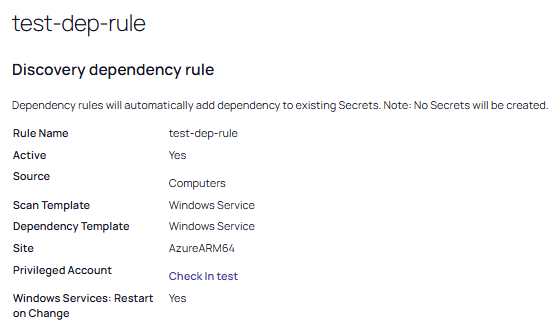
Dependency rules automatically add dependencies (Windows services, schedule tasks, application pools) to existing secrets. You can receive email notifications of linkages by adding an event subscription in the Event Subscriptions page. Rules can specify a combination of the domain or OU.
To create a rule:
-
Access Discovery. The Discovery Analysis tab appears.
-
Select the Network View tab.
-
Click the Create Rule button. The Create Rule popup appears.
-
From the Rule Type dropdown list, select Dependencies.
-
Click the Create Rule button. The New Rule page appears.
-
Type the name of the new rule in the Rule Name text box.
-
Click the None Selected link to choose a discovery source. The Pick OU popup appears.
-
Select the OU of your choice, it will appear as the source. The Scan Template dropdown list appears.
-
From the Scan Template dropdown list, select an output template. For this example, the Windows Service template was chosen.
-
From the Dependency Template dropdown list, select a dependency template. Once again, we chose Windows Service.
-
From the Site dropdown list, select the local installation of Verify Privilege Vault or a distributed engine to run the rule from.
-
For Privileged Account, click the No Secret Selected link to choose a secret for the scanning account. The chosen secret appears as a link.
-
Select the Windows Services: Restart on Change checkbox if you want the services restarted after discovery.
-
Select Save to keep your changes. The page for your new rule appears: