Distributed Engine Configuration and Sizing
Requirements
Supported Windows Server OS Versions
As of Verify Privilege Vault version 11.9.x:
-
Windows Server 2019 or newer is required for both the Web Server and Database Server in the minimum configuration.
-
Windows Server versions 2016-2022 are supported, with 2025 pending further QA validation.
Verify Privilege Vault DEs require that one of the following two server features be installed when the Verify Privilege Vault website is running on a Windows Server. This depends on which protocol is selected in the engine's callback settings. If HTTPS is selected, the HTTP activation is required. If TCP is selected, then TCP activation is required.
This is accomplished by going to one of the following in the Windows Server:
- .NET Framework 4.5 Features > WCF Services > HTTP Activation
- .NET Framework 4.5 Features > WCF Services > TCP Activation
If the feature is not installed, there will be an error message in the DE logs:
(405) Method Not Allowed. ---> System.Net.WebException: The remote server returned an error: (405) Method Not Allowed.
Distributed Engine Installation
All interaction between the Verify Privilege Vault Cloud tenant and your on-premises network uses our distributed engine service to communicate. The work tasks that distributed engine completes includes Active Directory authentication, password changing, and performing heartbeats. The machine where the engine is installed must be able to communicate outbound on port 443.
To install the Distributed Engine:
-
Access Verify Privilege Vault.
-
Search for Distributed Engine. The Distributed Engine page loads.
-
Click the Add Engine button. The Download Engine popup appears.
-
Select the related Processor Architecture for either 64-bit or 32-bit from the dropdown list.
-
Select the related Preconfigured Site from the dropdown list.
-
Click Download now.
You can install a distributed engine on your workstation or laptop for testing purposes, but for production installations, the distributed engine server should be installed on a server. Verify Privilege Vault uses the distributed engine to communicate with your domain, so if your machine is turned off, users cannot log in with their domain accounts. This will also cause heartbeat and remote password changing to fail. -
Access your downloaded
.zipfile and perform an extraction to an appropriate location. -
Run
setup.exeas an administrator to install the engine service and verify the folder location of the installation on your local machine. -
Go back to the Distributed Engine page. The Sites and Engines tab loads automatically.
-
Expand the Pending Engines section. The engine you installed should appear here.
-
Select the engine by clicking on it. Its details will automatically expand.
-
Hover over the details of the engine and the 3-dot vertical menu appears.
-
Select the Activate option. The Activate popup asking for confirmation will appear.
-
Select New Site to add a new site. The Add site popup appears:
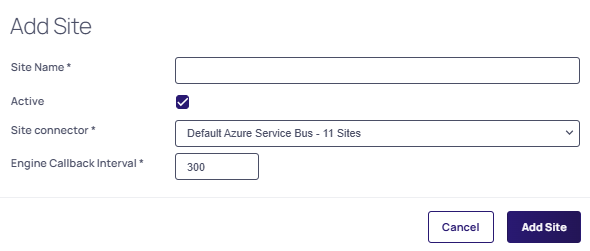
-
Add a Site Name, select the Active checkbox and leave the Engine Callback Interval at the default 300 value.
-
For the Site Connector, leave the Default Azure Service Bus - 11 Sites option unless otherwise directed.
-
Click Add Site to save your changes.
-
Access the newly created site by clicking on its name (it's a link). The Site tab loads by default.
-
In the Site section, click Validate Connectivity. The Validate Connectivity popup appears.
- Set the Timeout in seconds (which represents how long, in seconds, to wait for a successful round trip from site to bus to engine and then back to site).
- Click Validate.
It may take several minutes for the engine to register. If it does not immediately validate, wait a few minutes and try again. If an error occurs it appears in the popup window, for example:
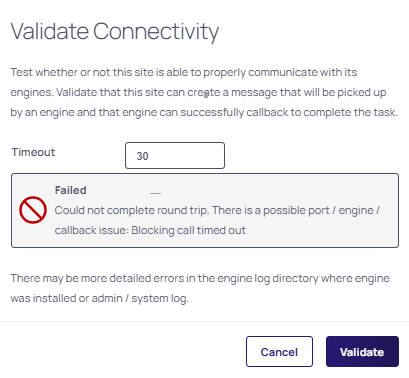
Configuring Engines for PowerShell Use
Verify Privilege Vault can be configured to use PowerShell for several key task types:
-
Discovery
-
Heartbeat
-
Password Change
-
Script Tests
Customers using PowerShell extensively for these tasks may, however, experience high CPU usage, as PowerShell is more resource-intensive compared to cmd or bash. To address this, you can limit the number of "shells" (tasks) a user can run on a machine. These "shells" represent the tasks the engine is executing under the user account associated with the Engine Service.
This limit is controlled by the MaxShellsPerUser setting for WinRM, which PowerShell uses. You can configure this setting through Group Policy, the registry, or directly with PowerShell. If MaxShellsPerUser is set, the engine will only execute the allowed number of PowerShell tasks and queue any additional tasks in the Service Bus for later execution. If it’s not set, the engine will run tasks as normal without restriction.
In cases where PowerShell scripts are unreliable or prone to timeouts—especially under heavy loads from Verify Privilege Vault—the engine may encounter issues. Since the Distributed Engine allows scripts to run for up to 15 minutes, extended timeouts can cause problems. To mitigate this, you can use the Prefetch feature, which controls how many tasks the engine can consume at one time. For instance, you could limit the number of concurrent Heartbeats by setting a specific prefetch value.
Additionally, a configuration setting allows you to match the prefetch count for all consumers that use PowerShell to the MaxShellsPerUser value. This setting can be found in the app-prefetch.config file located in the application directory.