How to Configure User Self-Service Options
You can enable users to perform certain tasks related to their accounts. These tasks include password reset and account unlock options. If you want to enable these features for Active Directory users, you need to run the IBM Security Connector under an account with the necessary permissions and follow these procedures.
This scenario includes the following topics:
Configure Password Reset Self-Service Options
You can enable users to reset their passwords and specify additional authentication requirements for a password reset.
To Enable the Password Reset Self-Service Options
-
Log in to Admin Portal, click Access > Policies tab, and select the policy set.
-
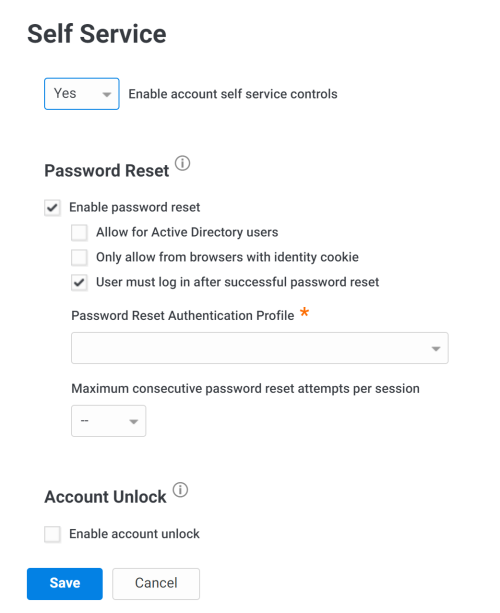
Click User Security Policies > Self Service.
-
Select Yes in the Enable account self service controls drop-down.
-
Enable the Password Reset option.
-
Limit who can reset their passwords.
-
The “Allow for Active Directory users” option enables users with Active Directory accounts who have forgotten their password to log in and reset their password. If you do not set this option, the “Forgot your password?” link is not displayed in the login prompt for users with Active Directory accounts. If you set this option, then you need to configure the Active Directory Self Service Settings on this page.
-
The “Only allow from browsers with identity cookie” option restricts password reset to those users who have already logged in successfully. If this check box is not enabled, then anybody can use the password reset options.
The Privileged Access Service writes the identity cookie the first time the user logs in successfully. However, when users clear the history on their browsers, it removes this cookie.
-
The “User must log in after successful password reset" option requires the user to log in after a password reset.
-
-
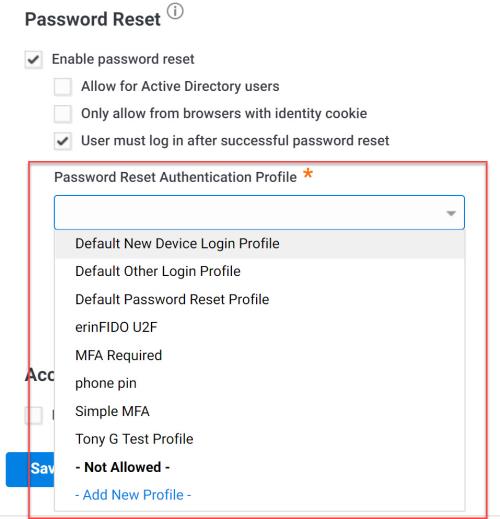
Select the authentication profile to specify the authentication mechanisms/second-factor authentication users must provide before they can reset their passwords.
You can use a default profile, use an existing profile, or create a new one.
See Creating Authentication Profiles for more information.
Self-service password reset is unavailable inside the MFA grace period.
For more information about setting the MFA grace period for Windows or Mac, see or , respectively.
-
Configure options for enabling password reset for Active Directory users.
This option is only available if you have enabled the “Allow for Active Directory users” option.
-
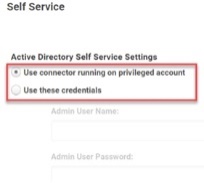
Select Use connector running on privileged account to run the connector under an account that has the Reset Password permission. Unless you have changed the connector account after you ran the connector installation wizard, the connector is run as a Local System account process. By default, a Local System account does not have the Reset Password permission. See Permissions Required for Alternate Accounts and Organizational Unitsto set the permission.
Optionally, after you select this Use connector running on privileged account setting, you can assign password reset permission for Active Directory users by creating a security group in Active Directory, delegate that group the Reset Password permission (see Password Reset Permissions), and add the connector’s computer object(s) to that group.
-
Select Use these credentials to use an account with the required permission to reset the password. For example, any account in the connector’s Domain Admins group can reset another user’s Active Directory account password.
-
-
Set the additional policy parameters.
The additional policy parameters let you manage the following password reset behaviors:
-
Maximum forgotten password resets allowed within window
Use the drop-down list to set a maximum for the number of times users can reset their password within the capture window. If users exceed this limit, the next time they attempt to reset the password, they get a message that they have reset their password too often and must wait before attempting again.
-
Capture window for forgotten password resets
Use the drop-down list to set the time period for maximum forgotten password resets. When users exceed the number or resets in this time period, they cannot reset the password again. This value also specifies how long from the last reset attempt the user must wait before they are allowed to reset the password.
-
-
Specify the Maximum consecutive password reset attempts per session option.
This option specifies the number of attempts users have to reset their password for that session before they are taken back to the log-in page. The default is 5 attempts.
-
Click Save.
What Your Users See
After you enable this policy setting and push the policy, users can do the following
-
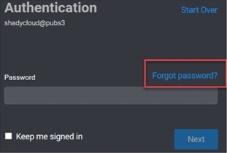
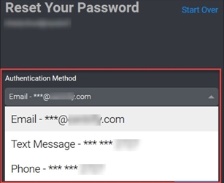
Click the Forgot password? link from the Privileged Access Service login window.
The authentication mechanisms you specified in the authentication profile (step 6 above) are shown to users as options for confirming their identities before they can reset their passwords.
-
Select the authentication mechanism you want to use.
-
Click Next.
-
Satisfy the selected authentication mechanism.
-
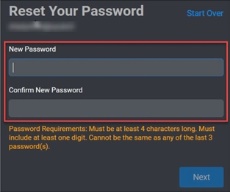
Enter your new password.
-
Click Next.
Configure Account Unlock Self-Service Options
You can enable users to unlock their accounts.
To enable account unlock policies:
-
Log in to Admin Portal, click Access > Policies tab, and select the policy set.
-
Click User Security Policies > Self Service.
-
Select Yes in the Enable account self service controls drop-down.
-
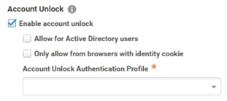
Enable the Account Unlock option.
-
Limit who can unlock their accounts.
-
The “Allow for Active Directory users” option enables users with Active Directory accounts to unlock their accounts. If you do not set this option, the “Unlock your account?” link is not displayed in the login prompt for users with Active Directory accounts. If you set this option, then you will need to configure the Active Directory Self Service Settings.
-
The “Only allow from browsers with identity cookie” option restricts account unlock to those users who have already logged in successfully. If this box is not set, anybody can use the account unlock option.
The Privileged Access Service writes the identity cookie the first time the user logs in successfully. However, when users clear the history on their browsers, it removes this cookie.
-
-
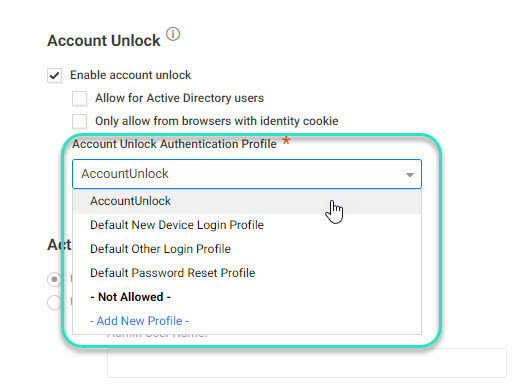
Select the authentication profile to specify the authentication mechanism/second-factor authentication users must provide before they can unlock their accounts.
You can use a default profile, use an existing profile, or create a new one. Users can't use the same factors to unlock the account that they use to login, so make sure the authentication profile used for account unlock has additional factors selected and the user account has the necessary attributes to use them.
For example, if the user typically logs in with the "Password" and "Email confirmation code" challenges, you could select the "Text message (SMS)confirmation code" challenge in the authentication profile used for self-service account unlock. To pass an SMS challenge, the user account must have a valid value for the "Mobile Number" attribute.
See Creating Authentication Profiles for more information.
-
Configure options for enabling account unlocking for Active Directory users.
-
Select Use connector running on privileged account to run the connector under an account that has the User Account Control permission. Unless you have changed the connector account after you ran the connector installation wizard, the connector is run as a Local System account process. By default, a Local System account does not have the User Account Control permission. See Permissions Required for Alternate Accounts and Organizational Units to set the permission.
Optionally, after you select this Use connector running on privileged account setting, you can assign account unlock permission for Active Directory users by creating a security group in Active Directory, give a user or group permission to read and write the Lockout Time attribute for an OU or other container, and add the connector’s computer object(s) to that group.
Select Use these credentials and provide the account user name and password to use an account with the required permission to unlock the account. For example, any account in the connector’s Domain Admins group can unlock another user’s Active Directory account.
-
-
Click Save.