Understanding Group Policies for Mac Users and Computers
IBM group policies allow administrators to extend the configuration management capabilities of Windows Group Policy Objects to managed Mac computers and to users who log on to Mac computers. This chapter provides an overview to using the IBM Security Mac group policies that can be applied to Mac computers and users
For reference information about the Mac OS X-specific computer and user policies that you can set, see the following topics.
For additional information about creating and using group policies and Group Policy Objects, see your Windows or Active Directory documentation, such as https://technet.microsoft.com/en-us/windowsserver/bb310732.aspx.
For information about other IBM group policies that are not specific to Mac computers and users, see the Group Policy Guide.
The following topics are covered:
Understanding Group Policies and System Preferences
Applying Standard Windows Policies to Mac OS X
Configuring Mac-specific Parameters
Understanding Group Policies and System Preferences
In many organizations, administrators who have both Windows and Mac computers in their organization want to manage settings for their Windows and Macintosh computers and users using a standard set of tools. In a Windows environment, the standard method for managing computer and user configuration settings is through Group Policy Objects applied to the appropriate site, domain, or organizational unit (OU) for different sets of computer and user accounts.
IBM Security provides this capability for Mac computers and users through a group policy extension. The IBM Security administrative template for Mac OS X (centrify_mac_settings.xml or centrify_mac_settings.adm) provides group policies that can be applied from a Windows server to control Mac OS X settings and behavior. These group policies can be applied to Mac OS X computers and to users who log on to those computers
Through the IBM Security administrative template for Mac OS X, Windows administrators using the Group Policy Management Editor can centrally access and control native Mac system preferences.
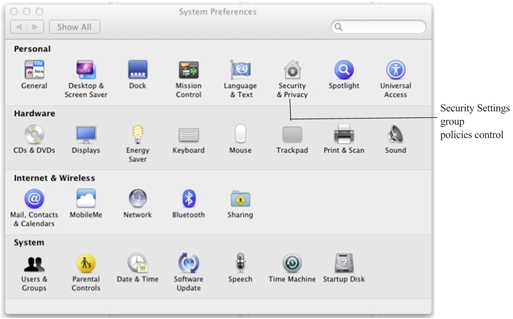
In the current IBM Security administrative template for Mac OS X, IBM group policies control settings for Personal, Hardware, Internet & Network, and System preferences, including:
-
Accounts, (General) Appearance, Desktop & Screen Saver, Dock, Energy Saver, Network, Security & Privacy, Sharing, Software Update, and so on.
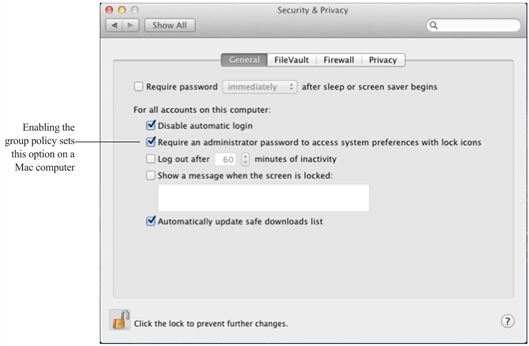
When you enable a group policy in a Windows Group Policy Object, you effectively set a corresponding system preference on the local Mac computer where the group policy is applied. For example, if you enable the group policy Computer Configuration > IBM Security Settings > Mac OS X Settings > Security > Require password to unlock each secure system preference, it is the same as selecting the General tab of the Security & Privacy system preference, then clicking the Require an administrator password to access system preferences with lock icons option on a local Mac OS X computer. Once the group policy is enabled in the Windows Group Policy Object and updated on the local Mac computer, the corresponding option is checked:
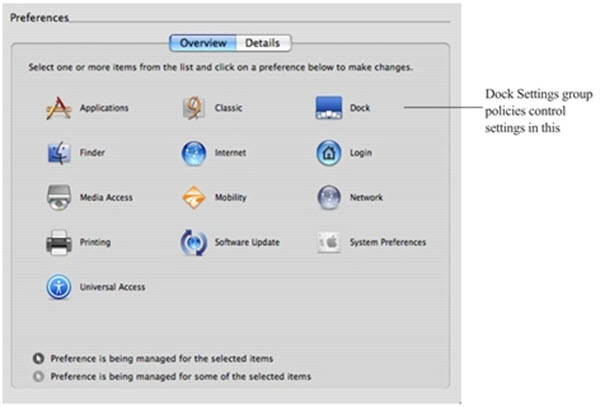
In addition to the system preferences that are typically set on individual computers, there are many Mac configuration settings that are typically set from a Mac OS X server using the Workgroup Manager. These workgroup policies control application or media access, synchronization rules for mobile user accounts, the look and operation of the Dock, and other settings. The IBM Security administrative template for Mac provides centralized access to many of these Workgroup Manager settings, including Applications, Dock, Media Access, Mobility, Software Update, and System Preferences.
Not all group policies apply to all versions of the Mac operating environment or all computer models. If a particular system preference does not exist, is not applicable to the installed operating system, or is implemented differently on some computers, the group policy setting may be ignored or overridden by a local setting.
Group policies are available after you install the IBM Security administrative template for Mac as described in Installing the Administrative Template, below. After you install the administrative template, the Windows administrator can use Active Directory MMC snap-ins or the Group Policy Management Console to create and link Group Policy Objects to sites, domains, or organizational units that include Mac computers that are joined to an Active Directory domain. Administrators can then use the Group Policy Management Editor to enable and configure the specific policies they want to enforce on Mac computers that are joined to the Active Directory domain.
See the Group Policy Guide for more information about using Active Directory Users and Computers or using the Group Policy Management Console or adding other IBM Security administrative templates to a Group Policy Object.
Linking Group Policy Objects
To apply group policies to Mac computers, you can link an existing group policy object (GPO) that you are using for a Windows or UNIX computer, or create a new GPO to link to a domain or OU that contains your Mac computers and users. In general, it is recommended that you create an OU specifically for your Mac computers and link a new GPO to that OU. However, there is no problem adding the Mac group policies to an existing GPO and configuring policies for Mac computers; Mac OS X-specific policies that are applied to Windows or UNIX computers are simply ignored.
You apply GPOs to Mac users the same way; link the GPO to an OU containing the users. Group policies are only applied to users and computers in the organizational unit (OU) linked to the Group Policy object (GPO) and any of the child OUs. If your users and computers are in different OUs (which is common), IBM Security recommends using user Group Policy loopback processing to make sure user policies are applied to everyone who logs on to a Mac. This is a standard Microsoft Group Policy that applies to every user to the computer. See Setting User-based Group Policies for more information about applying user policies.
Installing Mac Group Policies
IBM group policies for Mac consist of two components
- The DirectControl agent for Mac and its associated configuration and system plug-in files that reside on the Mac computer. The DirectControl agent and related files determine the policies that have been applied to the local computer, or to the user who is logging on, and implement the policy through system preferences or other local configuration settings. This guide assumes that you have installed the DirectControl agent on your Mac computers.
- An administrative template (
.xmlor.admxfile) that describes the policy settings available to the Group Policy Management Editor. The administrative template must be installed on a Windows computer that has the Group Policy Management Editor and the IBM Security Group Policy Management Editor Extension. The Group Policy Management Editor and the IBM Security Group Policy Management Editor Extension must be available for you to enable and configure policies. See the Mac Quick Start Guide for more information.
Installing the Administrative Template
IBM Security provides templates in both XML and ADMX format. In most cases it is best to use the XML templates, which provide greater flexibility, such as the ability to edit settings after setting them initially, and in many cases contain validation scripts for the policies implemented in the template
However, in certain cases, you may want to add templates by using the ADMX files. For example, if you have implemented a set of custom tools for the Windows ADMX-based policies, and want to extend those tools to work with the IBM Security policies, you can implement the policies with ADMX template files. The Group Policy Management Editor will automatically read all ADMX files stored in the %systemroot%PolicyDefinitions folder.
The ADMX templates do not support extended ASCII code for locales that require double-byte characters. For these locales, you should use the XML templates.
To install the IBM Security XML administrative template for Mac group policies
This procedure assumes that you are using the Group Policy Management Console and have created a Mac OS X-specific GPO. For information about using a different console, such as ADUC, see the Group Policy Guide.
-
Open the Group Policy Management Console and select the Group Policy Object that you are using for Mac computers, right-click, then click Edit to open the Group Policy Management Editor.
-
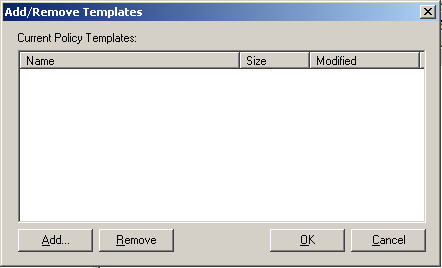
Expand Computer Configuration > Policies and select IBM Security Settings. Right click and click Add/Remove Templates.
-
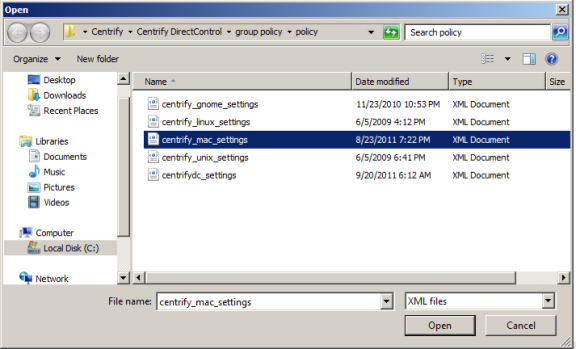
Click Add, then navigate to the directory that contains the IBM Security
centrify_mac_settings.xmladministrative template. By default, IBM Security administrative templates are located in theC:Program Files\Common Files\Centrify Shared\Group Policy Management Editor Extension\policyfolder. -
Select the
centrify_mac_settings.xmlfile, then click Open to add this template to the list of Policy Templates. -
Click OK.
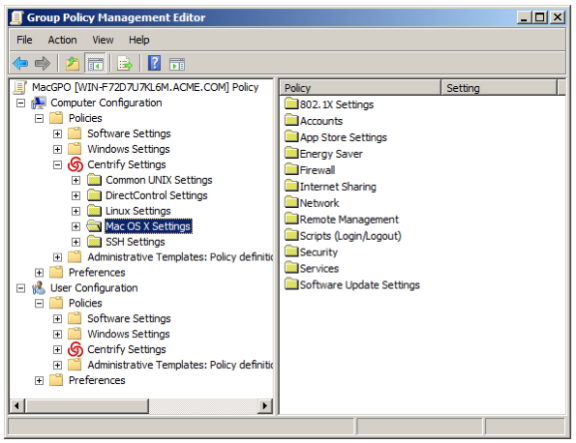
You should now see the categories of Mac group policies listed as Mac OS X Settings under IBM Security Settings in the Group Policy Management Editor. For example:
If you update IBM Security to a new version, new templates may be included with the installation. To make any new policies included in the templates available for use, you must reapply each template by following the steps in one of these procedures. If you see the message, The selected XML file already exists. Do you want to overwrite it?, click Yes. This action overwrites the template with any new or modified group policies. It does not affect any configuration in the template that has been applied; that is, any policies that you have enabled remain enabled.
Setting Mac Group Policies
Like other group policies, policies for Mac users and computers are organized into categories within the Group Policy Management Editor under Computer Configuration > Policies > IBM Settings > Mac OS X Settings (Setting Computer-based Group Policies) or IBM Security Settings > Mac OS X Settings (Setting User-based Group Policies). In general, these categories map directly to different types of Mac system preferences and individual policy settings within the categories map to specific settings within the system preference.
Normally, once enabled, policies get applied at the next group policy refresh interval, after the user logs out and logs back in, or after the computer has been rebooted. Some Mac group policies, however, require the user to log out and log back in or the computer to be rebooted. The description of each group policy indicates whether the policy can be applied “dynamically” at the next refresh interval or requires a re-login or a reboot.
You may also update group policies manually by running the adgpupdate command on an individual computer. See the next section, Updating Configuration Policies Manually.
The system preference updated on an individual computer must be closed, then reopened for the group policy setting to be visible.
In most cases, group policies can be Enabled to activate the policy or Disabled to deactivate a previously enabled policy. Changing a policy to Not Configured has no effect for any Mac group policies. Once a group policy is set on a local computer, it remains in effect even if the computer leaves the Active Directory domain. The administrator or users with an administrative account can change settings manually at the local computer, but any manual changes are overwritten when the group policy is applied.
Updating Configuration Policies Manually
Although there are Windows group policy settings that control whether group policies should be refreshed in the background at a set interval, IBM Security also provides a command line program to manually refresh group policy settings at any time. This command line program, adgpupdate, forces the adclient daemon to contact Active Directory and collect group policy settings. With the adgpupdate command, you can specify whether you want to refresh computer configuration policies, user configuration policies, or both.
When you run the adgpupdate command, the adclient daemon does the following:
- Contacts Active Directory for computer configuration policies, user configuration policies, or both. By default,
adclientcollects both computer and user configuration policies. - Determines all of the configuration settings that apply to the computer, the current user, or both, and retrieves those settings from the System Volume (
SYSVOL). - Writes all of the configuration settings to a virtual registry on the local computer.
- Starts the
runmappersprogram to initiate the mapping of configuration settings using individual mapping programs for user and computer policies. - Resets the clock for the next refresh interval.
For more information about using the adgpupdate command, see the adgpupdate page or Using adgpupdate in the Administrator’s Guide for Linux and UNIX.
Applying Standard Windows Policies to Mac OS X
Every Group Policy Object includes several default Windows-based group policy categories and default Windows-based administrative templates for user and computer configuration. Most of the settings in the default Windows policies and administrative templates only apply to Windows computers and Windows user accounts. However, some of the common Windows configuration settings for password enforcement, such as the policies for minimum password length and complexity, do apply to Mac computers. If these settings are enabled for a Group Policy Object applied to a site, domain, or OU that includes Mac OS X computers, the settings are enforced for Mac users and computers.
The following sections describe the standard Windows group policies that you can apply to Mac computers and users and where you can find these policies when viewing a Group Policy Object in the Group Policy Management Editor.
Group Policy Refresh and Loopback Processing
The Computer Configuration > Administrative Templates > System > Group Policy object contains the following policies that you can use to control how group policies are refreshed and applied.
- Turn off background refresh of Group Policy
- Group Policy refresh interval for computers
- User Group Policy loopback processing mode
Synchronizing Time
By default, the local Network Time Protocol (NTP) Client is enabled and synchronizes your computer’s clock to the Domain Controller. If you do not want your local NTP service to synchronize to the NTP service on the Domain Controller, explicitly disable the (Windows) Enable Windows NTP Client group policy. You can also synchronize to a different NTP server by specifying one in the Configure Windows NTP Client group policy.
To set these policies, in the Group Policy Editor, click Computer Configuration > Administrative Templates > System > Windows Time Service > Time Providers. The following policies are available to control time synchronization settings.
- Enable Windows NTP Client
- Configure Windows NTP Client
Specifying Time Sync Polling Interval
The Computer Configuration > Administrative Templates > System > Windows Time Service > Global Configuration Settings policy allows you to control the max polling interval with the MaxPollInterval option.
Configure Interactive Log On
Select the Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options object to configure the following policies related to interactive log on.
These policies apply to SSH login only, not to login through the graphical user interface.
- Interactive logon: Message text for users attempting to log on
- Interactive logon: Prompt user to change password before expiration
Set Password Requirements
Select the Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy object to set password requirements.
- Enforce password history
- Maximum password age
- Minimum password age
- Minimum password length
- Password must meet complexity requirements
- Store passwords using reversible encryption
Configuring Mac-specific Parameters
Most configuration parameters apply to both Mac or only to actual UNIX or Linux systems. All these parameters are described in the Configuration and Tuning Reference Guide. However, the following parameters apply only to Mac OS X and are described in this section.
- adclient.autoedit.mac.netlogin
- adclient.mac.map.home.to.users
- adclient.network.wait.max
- mac.auto.generate.new.login.keychain
- mac.protected.keychain.enable
- mac.protected.keychain.user.default
- mac.protected.keychain.delete
- mac.protected.keychain.lock.inactivity
- mac.protected.keychain.lock.when.sleeping
- mac.keychain.sync.enabled
- mac.keychain.sync.polling.interval
- logger.login.log
adclient.autoedit.mac.netlogin
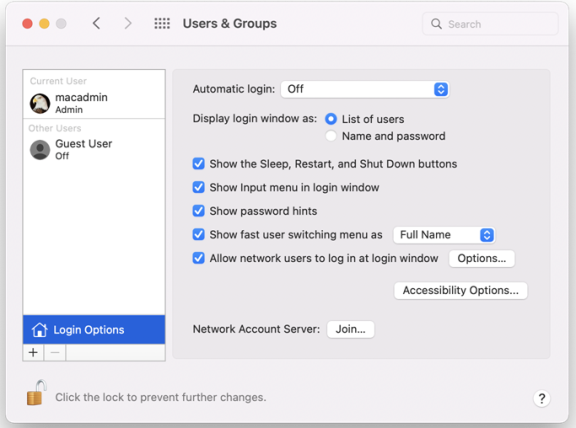
System Preferences > Users & Groups (Accounts) has a login option: Allow network users to log in at login window:
If this option is deselected, Active Directory users will not be able to log into the computer. The configuration parameter adclient.autoedit.mac.netlogin controls whether this option can be deselected by users. By default, the parameter is true in the /etc/centrifydc/centrifydc.conf file:
adclient.autoedit.mac.netlogin: true
In this case, even if a user deselects the box, the box is selected again when adclient is restarted, effectively preventing a user from deactivating network login.
If you want to allow a user to deactivate network login, set the parameter to false. If a user deselects network login in System Preferences > Accounts, the next time adclient starts, network users will be unable to log in to the computer.
adclient.mac.map.home.to.users
On some versions of Mac OS X, /home is an automount point. If a zone user’s home directory is set to /home/username, the operating system cannot create the home directory and the user cannot log in. Therefore, you should not specify /home/username as the home directory for any Mac OS X users, but since this is a typical UNIX home directory, there may be Active Directory users who have a /home/username home directory.
To avoid potential problems, you can configure IBM Security to change /home/username to /Users/username (the default Mac OS X home directory), in one of two ways:
-
Enable the group policy, Map /home to /Users.
-
Set the parameter,
adclient.mac.map.home.to.userstotrueto enable the change for the local computer only; for example:adclient.mac.map.home.to.users:true
adclient.network.wait.max
The IBM Security agent for Mac OS X performs network checks during startup to determine whether the device is connected to the domain. The adclient.network.wait.max parameter sets the maximum time the agent waits for the network before deciding to boot in either connected or disconnected mode. The default value is five seconds.
If DNS latency is high in your environment, the agent might determine that the device is in a Disconnected state too soon.
You can increase the value for the adclient.network.wait.max parameter if it’s appropriate for your network environment; however, this might result in increased boot times.
logger.login.log
Login events are captured in /var/log/centrifydc-login.log by default. You can turn off this feature by setting the logger.login.log parameter to off. Refer to Collecting Information Specific to Login Events for more information about /var/log/centrifydc-login.
mac.auto.generate.new.login.keychain
Use this parameter to automatically generate a new login keychain if a user’s keychain password does not match the password they used to successfully login.
The default value is false.
Refer to Auto Generate New Login Keychain for more information about the group policy that controls this parameter.
mac.protected.keychain.enable
Setting this parameter to true creates a new keychain protected by either an asymmetric token stored on a smart card or by a password, depending on the log in type.
The default value is false.
Refer to Enable Protected Keychain for more information about the group policy that controls this parameter.
Changing the group policy setting for this parameter does not change the parameter's value in this file. The two are set independently, with the group policy setting taking priority.
mac.protected.keychain.user.default
Setting this parameter to true sets the protected keychain as the default keychain for that user.
The default value is true.
Refer to Enable Protected Keychain for more information about the group policy setting that controls this parameter.
Changing the group policy setting for this parameter does not change the parameter's value in this file. The two are set independently, with the group policy setting taking priority.
mac.protected.keychain.delete
Setting this parameter to true deletes the existing password-protected Login Keychain after logging in.
The default value is false.
This parameter only works if mac.protected.keychain.enable is set to true.
Refer to Enable Protected Keychain for more information about the group policy setting that controls this parameter.
Changing the group policy setting for this parameter does not change the parameter's value in this file. The two are set independently, with the group policy setting taking priority.
mac.protected.keychain.lock.inactivity
Use this parameter to set the period of inactivity in minutes to automatically lock the protected keychain.
The default value is 0, which means the protected keychain is never automatically locked.
Refer to Lock Protected Keychain after Number of Minutes of Inactivity for more information about the group policy that controls this parameter.
Changing the group policy setting for this parameter does not change the parameter's value in this file. The two are set independently, with the group policy setting taking priority.
mac.protected.keychain.lock.when.sleeping
Setting this parameter to true locks the protected keychain when the Mac sleeps.
The default value is false.
Refer to Lock Protected Keychain When Sleeping for more information about the group policy that controls this parameter.
Changing the group policy setting for this parameter does not change the parameter's value in this file. The two are set independently, with the group policy setting taking priority.
mac.keychain.sync.enabled
This configuration parameter enables Keychain synchronization for the users on a mac.
If this parameter is enabled, the current login user will receive a password change notification when his/her password is changed remotely. When the user clicks on the notification, the IBM Security Keychain Sync utility appears and allows the user to synchronize the Keychain password.
Password changes can only be detected when the machine is in connected mode.
The default value is false.
Refer to Enable Keychain Synchronization for more information about the related group policy.
mac.keychain.sync.polling.interval
This configuration parameter sets the password change detection interval when mac.keychain.sync.enabled is enabled.
This parameter determines the time (in minutes) between checking for changed passwords. There is a random zero to five minute variance in the actual interval each device is checked for a changed password to maintain performance. As a result, the minimum interval is five minutes.
Valid intervals are between 5 minutes and 1440 minutes (1 day).
The default value is 30.
Refer to Enable Keychain Synchronization for more information about the related group policy.