Setting Computer-Based Group Policies
IBM group policies allow administrators to extend the configuration management capabilities of Windows Group Policy Objects to managed Mac computers and to users who log on to Mac computers. This chapter provides reference information for the IBM Mac group policies that can be applied specifically to Mac computers
The computer-based group policies are defined in the IBM Mac administrative template (centrify_mac_settings.xml) and accessed from Computer Configuration > Policies > IBM Settings > Mac OS X Settings. See Understanding Group Policies for Mac Users and Computers for general information about how IBM Security uses group policies to manage Mac settings and for information on how to install the group policy administrative templates.
For reference information about user-based policies, see Setting User-based Group Policies.
For information, see Applying Standard Windows Policies to Mac OS X and Configuring Mac-specific Parameters.
For more complete information about creating and using group policies and Group Policy Objects, see your Windows or Active Directory documentation. For more information about adding and using other IBM group policies that are not specific to Mac computers and users, see the Group Policy Guide
Setting Computer-Based Policies for Mac
The following table provides a summary of the group policies you can set for Mac computers. These group policies are in the IBM Mac administrative template (centrify_mac_settings.xml) and accessed from Computer Configuration > Policies > IBM Settings > Mac OS X Settings.
| Use this policy | To do this |
|---|---|
| Allow Certificates with No Extended Key Usage Certificate Attribute | For smart card log in, allow the use of certificates that do not contain the extended key usage (EKU) attribute. This is a Windows policy that is defined in the Administrative Templates > Windows Components > Smart Card folder using an adm template. |
| Map /home to /Users | Map the /home/username directory to /Users/username. This is a Mac OS X-specific policy but defined in the Direct Control Settings > Adclient Settings folder using the centrifydc_settings.xml template. |
| 802.1x Settings | Create login and system profiles for wireless authentication. These group policies correspond to 802.1X Options in the Networks system preference. |
| Accounts | Control the look and operation of the login window on Mac computers and map zone groups to the local administrator group. These group policies correspond to Login Options in the Accounts system preference. |
| App Store Settings Deprecated | Control the users and groups who can access the App Store. These group policies correspond to settings in the Sleep and Options panes in the Energy Saver system preference. |
| Custom Settings | Customize and install configuration profiles. |
| Energy Saver | Control sleep and wake-up option on Mac computers. These group policies correspond to settings in the Sleep and Options panes in the Energy Saver system preference. |
| Firewall | Control the firewall configuration on Mac computers. These group policies correspond to settings in the Firewall pane of the Sharing system preference. |
| Internet Sharing | Manage Internet connections on Mac computers. These group policies correspond to settings in the Internet pane of the Sharing system preference. |
| Network | Control DNS searching and proxy settings. These group policies correspond to settings in the TCP/IP and Proxies panes of the Network system preference. |
| Remote Management | Control Apple Remote Desktop access for zone users. These group policies correspond to the Manage > Change Client Settings options in Apple Remote Desktop. |
| Security & Privacy | Control security settings on Mac computers. These group policies correspond to settings in the Security system preferences. |
| Services | Control access to various services on Mac computers. These group policies correspond to settings in the Services pane of the Sharing system preference. |
| Software Update Settings | Control the options for automatic software updates on Mac computers. These group policies correspond to settings in the Software Update system preference. |
For information about specific policies and how to set them, see the policy description (Explain text) or the corresponding discussion of the specific system preference or individual setting in the Mac Help.
Allow Certificates with no Extended Key Usage Certificate Attribute
Path
Computer Configuration > Policies > Administrative Templates: Policy Definitions> Windows Components> Smart Card.
Description
The group policy, “Allow certificates with no extended key usage certificate attribute” is defined in a Windows administrative template file (.adm), not in centrify_mac_settings.xml, and is in Administrative Templates, not in Mac Settings.
To enable or disable this policy, click Computer Configuration > Policies > Administrative Templates: Policy Definitions > Windows Components > Smart Card.
Enabling this policy setting allows the use of certificates for smart card login that do not have the Extended Key Usage (EKU) attribute set. Normally, certificates that are used for smart card login require this attribute with a smart card logon object identifier.
When you enable this policy, it sets the smartcard.allow.noeku parameter to true in the IBM configuration file. Certificates with the following attributes can also be used to log on with a smart card:
- Certificates with no EKU
- Certificates with an All Purpose EKU
- Certificates with a Client Authentication EKU
If you disable or do not configure this policy setting (and do not set the smartcard.allow.noeku parameter to true in the IBM configuration file) only certificates that contain the smart card logon object identifier can be used with smart card log in.
After changing the value of this parameter, you must re-enable smart card support by running the following sctool command as root:
[root]$ sctool -E
You must also specify the --altpkinit or --pkinit parameter when you run sctool with the -E option.
Map /home to /Users
Path
Computer Configuration > Policies > IBM Settings > DirectControl Settings > Adclient Settings.
Description
The Mac group policy, Map /home to /Users is defined in the centrifydc_settings.xml file, not in centrify_mac_settings.xml, and is in IBM Security Settings, not in Mac Settings.
To enable or disable this policy, click Computer Configuration > Policies > IBM Settings > DirectControl Settings > Adclient Settings.
On some versions of Mac OS X, /home is an automount point. If a zone user’s home directory is set to /home/username, the operating system cannot create the home directory and the user cannot log in. Therefore, you should not specify /home/username as the home directory for any Mac users, but since this is a typical UNIX home directory, there may be Active Directory users who have a /home/username home directory. To avoid potential problems, enable this group policy, Map /home to /Users, to configure IBM Security to change /home/username to /Users/username (the default Mac home directory). If you do not enable this policy, the change does not take effect.
This policy modifies the adclient.mac.map.home.to.users parameter in the IBM configuration file.
802.1X Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Settings to create profiles for wireless network authentication. The profiles you specify with these group policies are created in the Network system preferences pane.
Enable Machine Ethernet Profile
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings > Enable Machine Ethernet Profile
Description
Enable this policy to create an 802.1X ethernet profile so users can authenticate to an 802.1X-protected network by using the specified machine certificate.
This group policy only supports macOS 10.15 and lower.
This policy supports the TLS protocol for certificate-based authentication for computers.
Before you can enable this policy, you must have a Windows server configured for 802.1X wireless authentication. The configuration includes certificate templates that are configured for auto-enrollment of domain computers and automatically downloaded to Mac computers when they join the domain. See Configuring 802.1X Wireless Authentication for details about what you must configure before enabling the current policy.
After enabling this policy, set the following:
-
Template Name: Type the name of the auto-enrollment machine certificate that has been pushed down from the Windows domain server.
When pushed to a Mac computer, certificate names are prepended with
auto_; for example:auth_Centrify-1X
This group policy runs a script that looks for the specified certificate template in the /var/centrify/net/certs directory (which contains the certificate templates pushed down from the domain controller) and creates an Ethernet profile from this certificate.
Once enabled, this policy takes effect dynamically at the next group policy refresh interval.
Enable Machine Wi-Fi Profile
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings Enable Machine Wi-Fi Profile
Description
Enable this policy to create an 802.1X Wi-Fi profile for wireless network authentication for a computer.
This group policy only supports macOS 10.15 and lower.
This policy supports WEP or WPA/WPA2 security with the TLS protocol for certificate-based authentication for computers.
Before you can enable this policy, you must have a Windows server configured for 802.1X wireless authentication. The configuration includes certificate templates that are configured for auto-enrollment of domain computers and automatically downloaded to Mac computers when they join the domain. See Configuring 802.1X Wireless Authentication for details about what you must configure before enabling the current policy.
After enabling this policy, set the following:
-
SSID: Type the SSID for the wireless network.
-
Template Name: Type the name of the auto-enrollment machine certificate that has been pushed down from the Windows domain server.
When pushed to a Mac computer, certificate names are prepended with auto_; for example:
auth_Centrify-1XThis group policy runs a script that looks for the specified certificate template in the
/var/centrify/net/certsdirectory (which contains the certificate templates downloaded from the domain controller) and creates a WiFi profile from this certificate. -
Security Type: Select the security type from the drop-down list.
-
Other options: Select one or more of the following options:
- Auto join: Select this option to specify that the computer automatically join a Wi-Fi network that it recognizes. Do not select this option to specify that the logged in user must manually join a Wi-Fi network.
- Hidden network: Select this option if the Wi-Fi network does not broadcast its SSID.
- Proxy PAC URL: The URL of the PAC file that defines the proxy configuration. You can enter any string without spaces.
- Proxy PAC Fallback: Allows the device to connect directly to the destination if the PAC file is unreachable. This option is disabled by default.
Once enabled, this policy takes effect dynamically at the next group policy refresh interval.
Enable User Ethernet Profile
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings > Enable User Ethernet Profile
Description
Enable this policy to create an 802.1X ethernet profile so users can authenticate to an 802.1X-protected network by using the specified user certificate.
This group policy only supports macOS 10.15 and lower.
This policy supports the TLS protocol for certificate-based authentication for users.
By default, the auto-enrolled user certificates are pushed down to ~/.centrify/autouser_(name).{cert.key.chain}. Certificates are also imported into each user’s login keychain.
Before you can enable this policy, you must have a Windows server configured for 802.1X wireless authentication. The configuration includes certificate templates that are configured for auto-enrollment of domain computers and automatically downloaded to Mac computers when they join the domain. See Configuring 802.1X Wireless Authentication for details about what you must configure before enabling the current policy.
Users must perform these steps after login to authenticate to the network as the user:
- Select System Preferences > Network > Ethernet.
- If there are any pre-existing 802.1X connections, click Disconnect to disconnect the pre-existing connections. For example, if a machine 802.1X Ethernet policy has been set, the computer will already be authenticated using the machine credential.
- Click Connect. This action prompts the user with a list of available user identities in certificate-key pair format.
- Choose the appropriate auto-enrolled user identity.
Enable User Wi-Fi Profile
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings > Enable User Wi-Fi Profile
Description
Enable this policy to create an 802.1X Wi-Fi profile for wireless network authentication for a user.
This group policy only supports macOS 10.15 and lower.
This policy supports the TLS protocol for certificate-based authentication for users.
By default, the auto-enrolled user certificates are pushed down to ~/.centrify/autouser_(name).{cert.key.chain}. Certificates are also imported into each user’s login keychain.
The resulting profile is signed using the first available auto-enrolled machine certificates, which are under /var/centrify/net/certs/auto_(name).{cert.key.chain}. If an auto-enrolled machine certificate is not available, the profile will be unsigned.
Before you can enable this policy, you must have a Windows server configured for 802.1X wireless authentication. The configuration includes certificate templates that are configured for auto-enrollment of domain computers and automatically downloaded to Mac computers when they join the domain. See Configuring 802.1X Wireless Authentication for details about what you must configure before enabling the current policy.
After enabling this policy, set the following:
- SSID: Type the SSID for the wireless network.
- Security Type: Select the security type from the drop-down list.
-
Other options: Select one or more of the following options:
- Auto join: Select this option to specify that the computer automatically join a Wi-Fi network that it recognizes. Do not select this option to specify that the logged in user must manually join a Wi-Fi network.
- Hidden network: Select this option if the Wi-Fi network does not broadcast its SSID.
- Proxy PAC URL: The URL of the PAC file that defines the proxy configuration. You can enter any string without spaces.
- Proxy PAC Fallback: Allows the device to connect directly to the destination if the PAC file is unreachable. This option is disabled by default.
Users must perform these steps after login to authenticate to the network as the user:
- Select System Preferences > Network > Wi-Fi.
- If there are any pre-existing 802.1X connections, click Disconnect to disconnect the pre-existing connections. For example, if a machine 802.1X Ethernet policy has been set, the computer will already be authenticated using the machine credential.
- Click Connect. This action prompts the user with a list of available user identities in certificate-key pair format.
- Choose the appropriate auto-enrolled user identity (a certificate-key pair).
Specify System Profile (Deprecated)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > 802.1X Wireless Settings > Specify System Profile (Deprecated)
Description
This group policy is provided for backward compatibility with Mac OS X 10.6. If your environment does not contain any 10.6 computers, do not use this group policy.
Enable this policy to specify 802.1X system profile for wireless network authentication.
System profile can establish a wireless connection without a user login.
To add a system profile, enable the policy and click Add to enter the profile name and setting, then type a name for the profile.
The setting must follow this format:
Network;Security Type;AuthenticationMethod, where each field is separated by a semi-colon (;)- Network is the wireless network name
- Security type is one of
802.1X WEP,WPA Enterprise,WPA2 Enterprise - Authentication method is one or more of the following, separated by commas:
TTLS, PEAP, LEAP, MD5
For example:
OFFICE1;WPA Enterprise;PEAP
OFFICE2;802.1X WEP;TTLS,PEAP
Automatically turn on Airport; to automatically turn on AirPort device if this type of profile is specified. Otherwise, the status of the AirPort device will not change.
Once enabled, this policy takes effect dynamically at the next group policy refresh interval.
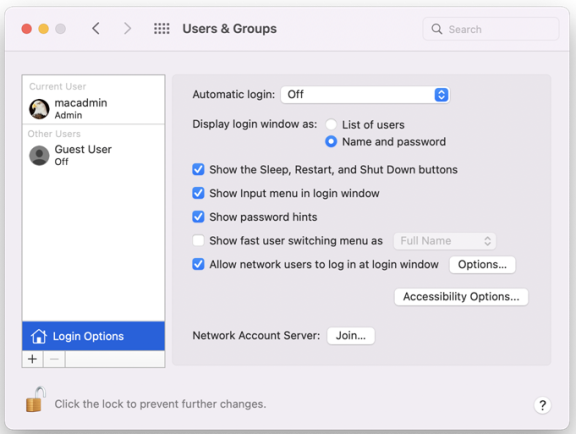
Accounts
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Accounts
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Accounts settings to manage the options from the Accounts ( ) system preference on Mac computers. These group policies correspond to the options displayed when you select the Accounts system preference, then click Login Options. For example:
) system preference on Mac computers. These group policies correspond to the options displayed when you select the Accounts system preference, then click Login Options. For example:
Set Login Window Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Accounts > Set login window settings
Description
Configure the Login Options on a computer. If you enable this policy, you can configure the Login Window to:
-
Display a text string as a login banner. The Banner you specify is displayed when the user is prompted to log on.
-
Display a List of Users or a Name and Password field. Displaying the Name and Password requires users to provide their account name and password, and is more secure than displaying a list of user names.
-
Show the Restart, Sleep, and Shut Down buttons.
-
Show the Input menu in the login window to allow users to change the current Keyboard Layout.
-
Show password hints in the login window.
-
Use VoiceOver at the login window.
-
Enable fast user switching.
-
Display the HostName, IP Address, and OS X or macOS Version. Users need to click the clock in the top right corner to view each field.
-
Disable reopening applications when logging back in. Check this to always uncheck the Reopen Windows when logging back in checkbox at logout, restart, or shutdown.
-
Hide all Local Users with a UID less than 500.
-
Enabling the options in this group policy is the same as clicking Login Options in the Accounts system preference and setting the corresponding login window options.
This policy does not impact lock screens. It only impacts the login window.
If you click Enable Fast User Switching, this setting does not take effect until the Login Options in the Accounts system preference is opened manually by a user on the local host. This step is required to display the list of users in the upper-right corner of the menu bar. After users log on, the user's full name, short name, or icon identifier is displayed in the menu bar. If you want to change how users are displayed in the menu, you also must do so manually from the Login Options in the Accounts system preference.
Once enabled, this group policy takes effect when users log out and log back in or when the computer is rebooted.
Map Zone Groups to Local Admin Group
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Accounts > Map zone group to local admin group
Description
Specify one or more zone groups to map to the admin group on the local computer. Members of the groups you specify here have administrative privileges on the local computer, including:
- The use of
sudocommand in a shell - The ability to unlock and make changes to System Preferences.
Be certain to create a zone group in Access Manager (or adedit) and add users who you want to have administrative privileges on managed Mac computers.
If the local computer is connected to the domain through Auto Zone, you cannot create a zone group because there are no zones. However, all Active Directory groups are valid for the joined computer, so you can map any group to the local admin group, but you need to know the group’s UNIX name, which you can retrieve on the local computer by using the adquery command, as shown in the following example.
[root]#adquery group -n
To set this policy
- Open the policy and select Enabled.
- Click Add.
- Enter the name of a zone group in the box (or the UNIX group name if connected through Auto Zone). Then click OK.
Map Zone Groups to Local Group
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Accounts > Map zone group to local group
Description
Specify one or more zone groups to map to a Mac local group on the local computer. Members of the zone groups you specify here will be given the privileges of the local group on the local computer; for example:
-
If you map to the
_lpadminand_lpoperatorlocal groups, members of the zone group can manage printer settings on the local computer. -
If you map to the admin local group, members of the zone group obtain administrator privileges on the local computer.
To obtain administrator privileges for a zone group, you can either map to the local admin group with this policy, or use the Map zone groups to local admin group policy. However, do not do both as the results are unpredictable.
Be certain to create a zone group in Access Manager (or adedit) and add users who you want to have administrative privileges on managed Mac computers.
If the local computers is connected to the domain through Auto Zone, you cannot create a zone group because there are no zones. However, all Active Directory groups are valid for the joined computer, so you can map any group to the local admin group, but you need to know the group’s UNIX name, which you can retrieve on the local computer, by using the adquery command, as follows
[root]#adquery group -n
To set this policy
-
Open the policy and select Enabled.
-
Click Add.
-
Enter the name of a local group and of a zone group in the respective boxes (or the UNIX group name if connected through Auto Zone), then click OK.
You can repeat this step multiple times to map the zone group to more than one local group.
App Store Settings Deprecated
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > App Store Settings (Deprecated)
Description
This policy has been deprecated and is no longer supported. Enabling it will have no effect. It is provided simply to allow you to disable the policy if it was set in an earlier version of the product. You can use the Application Access Settings (deprecated) group policies to control access to the App Store if you wish.
Prohibit Access to the App Store (Deprecated)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > App Store Settings (Deprecated) > Prohibit Access to the App Store (Deprecated)
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > App Store > Prohibit Access to App Store group policy to control access to the App Store.
By default, all users can access the App Store. Enable this group policy to prohibit access to App Store to all users except the root user and those you specifically authorize with the options, Allow these users to access App store, and Allow these groups to access App Store.
You can set the following options with this policy:
| Use this option | To do this |
|---|---|
| Allow these users to access App Store | The names of local or AD users who are allowed to access the App Store. When this policy is enabled, only users on this list and the root user are allowed to access the App Store. |
| Allow these groups to access App Store | The names of local or AD groups that are allowed to access the App Store. When this policy is enabled, only users in the specified groups, and the root user, are allowed to access the App Store. |
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Custom Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Custom Settings
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Custom Settings group policy settings to customize and install configuration profiles. The “Install MobileConfig Profiles” policy installs a device profile. To install a user profile, use the same policy in User Configuration > Policies > IBM Settings > Mac OS X Settings > Custom Settings.
Enable Profile Custom Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Custom Settings > Enable profile custom settings
Description
Enable this group policy to use the Custom payload to specify preference settings for applications that use the standard plist format for their preference files.
This group policy only supports macOS 10.15 and lower.
You can use this GP to add specific keys and values to an existing preferences plist file. However, not all applications work with managed preferences, and in some cases only specific settings can be managed.
By default, you should place the plist files with preference settings in the folder \\domain\SYSVOL\<domain>\customsettings.
To add a file, click Add and enter name of a file that you placed in the SYSVOL location. The file you specify is relative to this path:
\\domain\SYSVOL\domain\customsettings
For example, if you enter:
com.apple.plist
the file that is imported is:
\\domain\SYSVOL\domain\customsettings\com.apple.plist
Install MobileConfig Profiles
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Custom Settings > Install MobileConfig Profiles
Description
Enable this group policy to install mobile configuration profiles on managed Mac computers.
There is a Computer Configuration version of this policy (which installs device profiles) and a User Configuration version (which installs user profiles).
This group policy only supports macOS 10.15 and lower.
Before enabling this policy, you must create a directory and copy mobile configuration files to SYSVOL on the domain controller. SYSVOL is a well-known shared directory on the domain computer that stores server copies of public files that must be shared throughout the domain.
Specifically, create the following directory on the domain controller:
\\domainName\SYSVOL\domainName\mobileconfig
and copy one or more mobile configuration profile files to this directory. See Deploy Configuration Profiles to Multiple Computers for details on how to do this.
To specify mobile configuration files to install, enable the policy, then click Add. Enter the name of a mobile configuration file that you placed in SYSVOL on the domain controller. Include the .mobileconfig suffix with the name.
If you specify a file that is not in the SYSVOL mobileconfig directory, the profile will not be installed.
If you add new files to the existing list in the group policy, those profiles will be installed — existing profiles will not be touched. If you remove previously specified files, the profiles defined by these files will be uninstalled.
If you add two or more profile files that have the same payloadIdentifier, only one of them will be installed.
If you change the group policy to “Disabled” or “Not Configured”, all existing profiles that were installed previously by the group policy will now be uninstalled from the managed Mac computers.
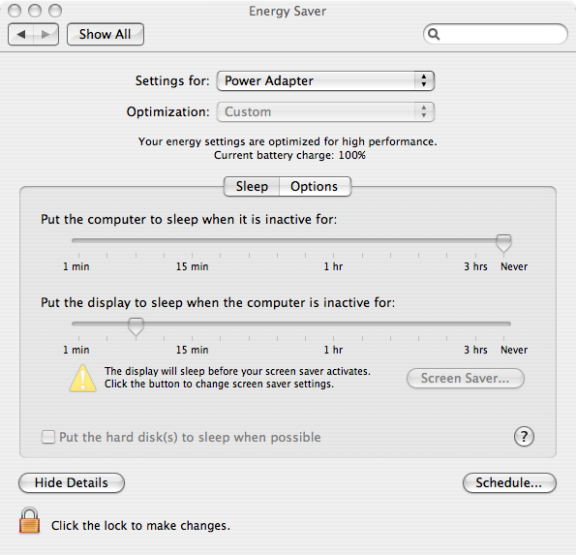
Energy Saver
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver settings to manage sleep and wake-up options from the Energy Saver ( ) system preference on Mac computers. For example:
) system preference on Mac computers. For example:
You can configure power options or schedule startup and shutdown times.
Open the appropriate folder to set power options when running on AC power or battery power. Each folder has the identical set of group policies:
- On AC power
- On battery power
Allow Power Button to Sleep the Computer
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Allow power button to sleep the computer
Description
Allow the power button to sleep the computer.
Enabling this group policy is the same as selecting the Allow power button to sleep the computer option in the Options pane of Energy Saver system preference.
This policy can take effect dynamically at the next group policy refresh interval.
Put The Hard Disk(s) to Sleep When Possible
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Put the hard disk(s) to sleep when possible
Description
Put computer hard disks to sleep when they are inactive.
Enabling this group policy is the same as selecting the Put the hard disk(s) to sleep when possible option in the Sleep pane of Energy Saver system preference.
This policy can take effect dynamically at the next group policy refresh interval.
Restart Automatically After a Power Failure
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Restart automatically after a power failure
Description
Enable to set the computer to automatically restart after a power failure.
Enabling this group policy is the same as selecting the Restart automatically after a power failure option in the Options pane of Energy Saver system preference.
This policy can take effect dynamically at the next group policy refresh interval.
Set Computer Sleep Time
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Set computer sleep time
Description
Specify the number of minutes of inactivity to allow before automatically putting a computer into the sleep mode.
If you enable this group policy, the period of inactivity you specify applies only when the computer is using its power adapter. If the computer is inactive for the number of minutes you specify, it is put in sleep mode.
Enabling this group policy is the same as selecting a time using the Put the computer to sleep when it is inactive for slider in the Sleep pane of Energy Saver system preference.
To prevent the computer from ever going into sleep mode, enter 0 for the number of minutes, or disable the policy.
This policy can take effect dynamically at the next group policy refresh interval.
Set Display Sleep Time
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Set display sleep time
Description
Specify the number of minutes of inactivity to allow before automatically putting the display into the sleep mode.
If you enable this group policy, the period of inactivity you specify applies when the computer is using its power adapter. If the computer is inactive for the number of minutes you specify, the display is put in sleep mode.
Enabling this group policy is the same as selecting a time using the Put the display to sleep when it is inactive for slider in the Sleep pane of Energy Saver system preference.
To prevent the display from ever going into sleep mode, enter 0 for the number of minutes, or disable the policy.
This policy can take effect dynamically at the next group policy refresh interval.
Wake When the Modem Detects a Ring
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Wake when the modem detects a ring
Description
Automatically take a computer out of sleep mode when the modem detects a ring. This group policy allows a computer that has been put to sleep to remain available to answer the modem.
This policy can take effect dynamically at the next group policy refresh interval.
Wake for Ethernet network administrator access
Automatically take a computer out of sleep mode when the computer receives a Wake-on-LAN packet from an administrator. This group policy allows a computer that has been put to sleep to remain available to network administrator access.
Enabling this group policy is the same as selecting the Wake for Ethernet network administrator access option in the Options pane of Energy Saver system preference.
This policy can take effect dynamically at the next group policy refresh interval.
Scheduled Events
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Scheduled events
Description
To configure sleep/shutdown times and startup times, open the Scheduled events folder (Computer Configuration Policies > IBM Settings > Mac OS X Settings > EnergySaver > Scheduled events).
Set Machine Sleep/Shutdown Time
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Scheduled events > Set machine sleep/shutdown time
Description
Specify a time to shut down or put the computer to sleep.
Enabling this group policy is the same as selecting the Schedule button in the Energy Saver system preference, then specifying times and days to shut down or put the computer to sleep.
After enabling this policy, specify values for the following:
- Action: Select sleep or shutdown
- Set machine sleep/shutdown time: Enter a time in the format HH:mm using a 24 hour clock; for example, to shut down or put the computer to sleep at 10:05 P.M:
22:05
- Sleep/shutdown machine on every: Select the days of the week on which to shut down or sleep the computer at the specified time. All days are selected by default.
This policy can take effect dynamically at the next group policy refresh interval.
Set Machine Startup Time
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Energy Saver > Scheduled events > Set machine startup time
Description
Specify a time to start up the computer.
Enabling this group policy is the same as selecting the Schedule button in the Energy Saver system preference, then specifying times and days to start up the computer.
After enabling this policy, specify values for the following:
- Set machine startup time: Enter a time in the format HH:mm using a 24 hour clock; for example, to start up the computer at 7:55 A.M.:
07:55
- Start machine on every: Select the days of the week on which to start the computer at the specified time. All days are selected by default.
This policy can take effect dynamically at the next group policy refresh interval.
Firewall
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall settings to manage the firewall options on Mac computers.
Enabling the IBM firewall group policies is the same as setting options from System Preferences > Security > Firewall.
With the IBM Firewall Group Policies, you can allow all incoming connections, or limit connections to the specified services and applications. You cannot block all connections:
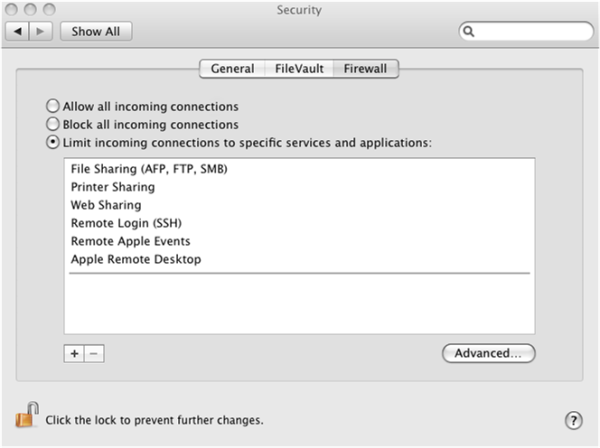
In addition, group policies are available for the Advanced firewall settings, Enable Firewall Logging, and Enable Stealth Mode.
Enable Firewall
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable firewall
Description
Prevent incoming network communication to all services and ports other than those explicitly enabled for the services specified in the Services pane of the Sharing system preferences.
This group policy turns on default firewall protection.
-
Block all incoming connections:
Block all incoming connections except those required for basic Internet services, such as DHCP, Bonjour, and IPSec.
-
Automatically allow signed software to receive incoming connections:
Allows software signed by a valid certificate authority to provide services accessed from the network. This setting will not take effect if Block all incoming connections is selected.
This policy takes effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable iChat
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable iChat
Description
On Mac OS X Servers, enabling this policy has no effect. If the firewall is enabled, the iChat service is not allowed through the firewall.
If the firewall is enabled, enabling this group policy is the same as clicking the On checkbox to allow communication through the firewall for iChat Bonjour. If you do not enable this group policy, traffic for iChat Bonjour will be blocked from the local computer.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable iPhoto Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable iPhoto Sharing
Description
On Mac OS X Servers, enabling this policy has no effect. If the firewall is enabled, the iPhoto Sharing service is not allowed through the firewall.
If the firewall is enabled, enabling this group policy is the same as clicking the On checkbox to allow communication through the firewall for iPhoto Bonjour Sharing. If you do not enable this group policy, traffic for iPhoto Bonjour Sharing will be blocked from the local computer. Users will be able to access iPhoto collections on other computers, but the local computer cannot be used to serve any iPhoto collections.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable iTunes Music Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable iTunes Music Sharing
Description
Enabling this group policy is the same as clicking the On checkbox to allow communication through the firewall for iTunes Music Sharing.
On Mac OS X Servers, enabling this policy has no effect. If the firewall is enabled, the iTunes Music Sharing service is not allowed through the firewall.
If you do not enable this group policy, traffic for iTunes Music Sharing will be blocked from the local computer. Users will be able to access iTunes collections on other computers, but the local computer cannot be used to serve any iTunes collections.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Network Time
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable network time
Description
On Mac OS X Servers, enabling this policy has no effect. If the firewall is enabled, the Network Time service is not allowed through the firewall.
If the firewall is enabled, enabling this group policy is the same as clicking the On checkbox to allow communication through the firewall for Network Time. If you do not enable this group policy, traffic from the Network Time service will be blocked.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Block UDP Traffic
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Block UDP traffic
Description
Enabling this group policy is the same as clicking the Block UDP Traffic checkbox in the Advanced firewall settings.
This group policy does not block UDP communications that are related to requests initiated on the local computer.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Firewall Logging
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Firewall > Enable firewall logging
Description
Log information about firewall activity, including all of the sources, destinations, and access attempts that are blocked by the firewall. The activity is recorded in the secure.log file on the local computer.
Enabling this group policy is the same as clicking the System Preferences > Security > Firewall then clicking Enable Firewall Logging in the Advanced firewall settings.
On Mac OS X Servers, enabling this policy has no effect.
This policy takes effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Stealth Mode
Prevent uninvited traffic from receiving a response from the local computer.
Enabling this group policy is the same as clicking the System Preferences > Security > Firewall then clicking Enable Stealth Mode in the Advanced firewall settings.
If you enable this group policy, the local computer will not respond to any network requests, including ping requests. Because the computer will not reply to ping requests, using this policy may prevent you from using network diagnostic tools that require a response from the local computer.
On Mac OS X Servers, enabling this policy has no effect.
This policy takes effect dynamically at the next group policy refresh interval without rebooting the computer.
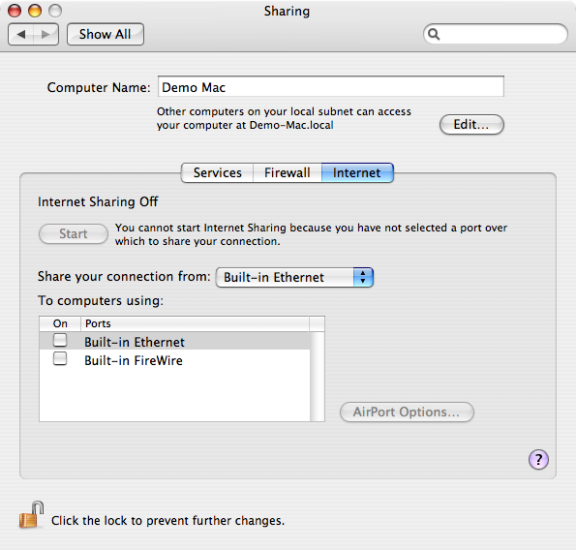
Internet Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Internet Sharing
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings >Internet Sharing group policy to prevent any kind of Internet sharing on the local computer. This group policy can only be used to prevent Internet sharing. Although this group policy corresponds to a setting on the Internet pane of the Sharing ( ) system preference, you can not use it to start Internet sharing, configure the shared connection, or set any other options. For example:
) system preference, you can not use it to start Internet sharing, configure the shared connection, or set any other options. For example:
Disallow All Internet Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Internet Sharing > Disallow all Internet Sharing
Description
Prevent any kind of Internet sharing on the local computer. Enabling this group policy is the same as clicking Stop to prevent other computers from sharing an Internet connection on a local computer in the Internet pane of the Sharing system preference.
For this group policy, clicking Disabled or Not Configured has no effect. If you have previously Enabled the group policy, Internet sharing will remain off until you manually start it on the local computer.
Once enabled, this group policy takes effect when users log out and log back in, or dynamically at the next group policy refresh interval without rebooting the computer.
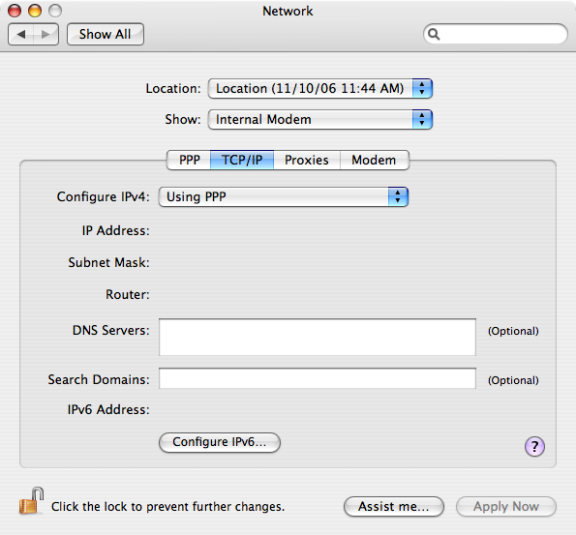
Network
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network settings to manage DNS search requests and proxy settings. These group policies correspond to settings in the TCP/IP and Proxies panes of the Network ( ) system preference on Mac computers. For example:
) system preference on Mac computers. For example:
Legacy Location Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings
Description
Use Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings to configure network settings for the Automatic network location.
Adjust List of DNS servers
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Adjust list of DNS servers
Description
Control the list of DNS servers when performing DNS lookups.
To use this policy, click Enabled, then click Add, type the IP address for a DNS server, then click OK to add the server to the list of DNS servers. Add as many servers as you want in this manner. When you are finished adding the servers, click OK to close the dialog box.
At any time while the policy is enabled, you can select an address in the list and click Edit to change the address, or Remove to remove it as a DNS server.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Adjust List of Searched Domains
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Adjust list of searched domains
Description
Control the list of domains to search when performing DNS lookups.
To use this policy, click Enabled, then click Add, type a domain name, then click OK to add the domain to the list of domains to search. Add as many domains as you want in this manner. When you are finished adding the domains to search, click OK to close the dialog box.
At any time while the policy is enabled, you can select a domain in the list and click Edit to change the name, or Remove to remove it as a domain to be searched.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Configure Proxies
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Configure Proxies
Description
Configure proxy servers to provide access to services through a firewall.
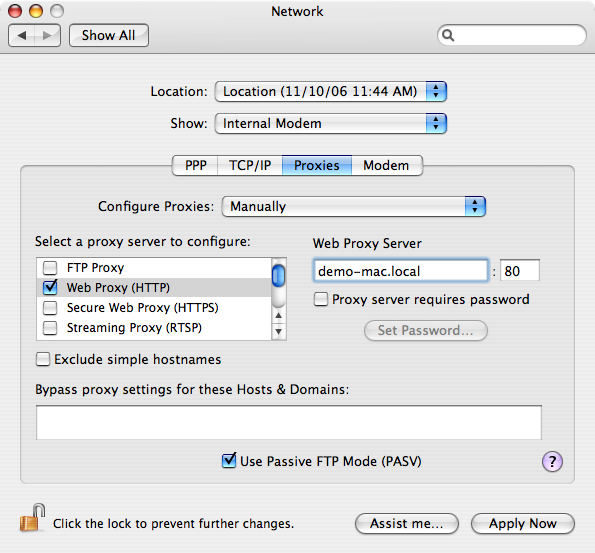
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Configure Proxies settings to manage settings on the Proxies panes of the Network system preference. For example:
These group policies enable you to configure the host names (or IP addresses) and port numbers for the computers providing specific services, such as File Transfer Protocol (ftp), Hypertext Transfer Protocol (http), and HTTP over Secure Sockets Layer (https), through a firewall. A proxy server is a computer on a local network that acts as an intermediary between computer users and the Internet to ensure the security and administrative control of the network.
Enable Proxies
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Configure Proxies > Enable Proxies
Description
Configure the host name (or IP address) and port number for the computers providing specific services. Within this category, you can enable the following proxy servers:
- Use the Enable FTP Proxy policy to configure the host name and port number for the FTP proxy server (FTP protocol).
- Use the Enable Web Proxy policy to configure the host name and port number for the Web proxy server (HTTP protocol).
- Use the Enable Secure Web Proxy policy to configure the host name and port number for the Secure Web proxy server (HTTPS protocol).
- Use the Enable Streaming Proxy policy to configure the host name and port number for the Streaming proxy server (RTSP protocol).
- Use the Enable SOCKS Proxy policy to configure the host name and port number for the Streaming proxy server (SOCKS protocol).
- Use the Enable Gopher Proxy policy to configure the host name and port number for the Gopher proxy server.
- Use the Enable Streaming Proxy policy to configure the host name and port number for the Streaming proxy server (RTSP protocol).
- Use the Enable Proxies using a PAC file policy to configure proxy servers from a proxy configuration file.
These policies can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Exclude Simple Hostnames
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Configure Proxies > Exclude simple hostnames
Description
Prevent requests to unqualified host names from using proxy servers. If you enable this policy, users can enter unqualified host names to contact servers directly rather than through a proxy.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Use Passive FTP Mode (PASV)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Configure Proxies > Use Passive FTP Mode (PASV)
Description
Use the FTP passive mode (PASV) to access Internet sites when computers are protected by a firewall.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Bypass Proxy Settings for these Hosts & Domains
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy location settings > Configure Proxies > Bypass Proxy settings for these Hosts & Domains
Description
Specify fully-qualified host names and domains for which you want to bypass proxy settings.
You should use this policy to define the hosts or domains that should never be contacted by proxy.
To use this policy, click Enabled, then click Add, type a host or domain name, and click OK to add the entry to the Show Contents list.
Each host or domain should be listed as a separate line in the Hosts and Domains list. For each host or domain, click Add, type the host or domain name, and click OK to add the host or domain as a new entry in the list. When you are finished adding items to the list, click OK to close the policy dialog box.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Location 1 and Location 2
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 2
Description
Use Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1 to configure network settings for an additional network location. The group policies in Location 2 are identical, and allow you to configure network settings for another network location.
Adjust List of DNS Servers
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1/Location 2 > Adjust list of DNS servers
Description
Control the list of DNS servers when performing DNS lookups.
To use this policy, click Enabled, then click Add, type the IP address for a DNS server, then click OK to add the server to the list of DNS servers. Add as many servers as you want in this manner. When you are finished adding the servers, click OK to close the dialog box.
At any time while the policy is enabled, you can select an address in the list and click Edit to change the address, or Remove to remove it as a DNS server.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Adjust List of Searched Domains
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1/Location 2 > Adjust list of searched domains
Description
Control the list of domains to search when performing DNS lookups.
To use this policy, click Enabled, then click Add, type a domain name, then click OK to add the domain to the list of domains to search. Add as many domains as you want in this manner. When you are finished adding the domains to search, click OK to close the dialog box.
At any time while the policy is enabled, you can select a domain in the list and click Edit to change the name, or Remove to remove it as a domain to be searched.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Network Location
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1/Location 2 > Enable network location
Description
Enable all network location settings under the current location category and set its location name. This policy must be enabled to apply settings in this location category (for example, Location1).
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Configure Proxies
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Location 1/Location 2 > Configure Proxies
Description
Configure proxy servers to provide access to services through a firewall. The group policies in this folder are the same as the ones in Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Network > Legacy Location settings> Configure Proxies. Refer to Configure Proxies for more information.
Remote Management
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Remote Management
Description
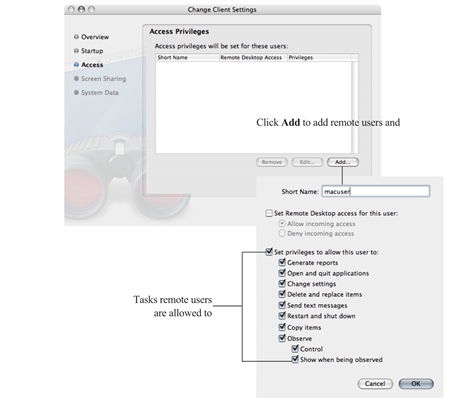
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Remote Management settings to control Apple Remote Desktop access for zone users. You can use these group policies to give Active Directory group members permission to remotely control Mac computers without physically having to activate the Apple Remote Desktop on the remote Mac computer.
The Remote Management group policies correspond to the Manage > Change Client Settings options in Apple Remote Desktop and are similar to access privileges defined on a client computer using the Sharing system preference. For example:
Because the group policies correspond to the Manage > Change Client Settings options in Apple Remote Desktop, the group policy settings are not displayed in the local system preference on the Mac client. Although the tasks you can assign to different groups by group policy correspond to tasks you can assign using the local Sharing system preference on a Mac client computer, the group policy settings do not update the local system preference to display check marks for the tasks that the remote users have been given permission to perform.
Enable Administrator Access Groups
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Remote Management > Enable administrator access groups
Description
Allow all users who are members of the following Apple Remote Desktop administrator groups to access this computer using Apple Remote Desktop.
Before enabling this group policy, you should create each Active Directory security group you intend to use and add a UNIX profile for each group to the zone, using the exact UNIX group names (ard_admin, ard_reports, ard_manage, ard_interact).
Creating UNIX profiles with these group names displays a warning message because the names are longer than eight characters. You can safely ignore this warning message.
Enabling this policy allows users in the following groups to manage Mac computers through Apple Remote Desktop:
-
ard_admingives all members of the group the ability to remotely control the computer desktop. -
ard_reportsgives all members of the group the ability to remotely generate reports on the computer. -
ard_managegives all members of the group the ability to manage the computer using Apple Remote Desktop. Users in this group can perform the following tasks by using Apple Remote Desktop:- Generate reports
- Open and quit applications
- Change settings
- Copy Items
- Delete and replace items
- Send text messages
- Restart and shut down
-
ard_interactgives all members of the group the ability to interactively observe or control the computer using Apple Remote Desktop.Users in this group can perform the following tasks by using Apple Remote Desktop:
- Send text messages
- Observe
- Control
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
See Setting Up Local and Remote Administrative Privileges for information on how to use this group policy with the Map Zone Groups to Local Admin Group policy to enable both local and remote administrative access for the same group of users.
Scripts (Login/Logout)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (Login/Logout)
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (Login/Logout) > Specify multiple login scripts group policy to deploy login scripts that run when an Active Directory or local user logs on. When you use this group policy, the login scripts are stored in the Active Directory domain’s system volume (sysvol) and transferred to the Mac computer when the group policies are applied. Login scripts are useful for performing common tasks such as mounting and un-mounting shares
This policy is also available as a user policy. If you specify scripts using both the computer and user policies, the computer scripts are executed first.
Specify Multiple Login Scripts
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (Login/Logout) > Specify multiple login scripts
Description
Specify the names of one or more login scripts to execute when an AD or local user logs on. The scripts you specify run simultaneously in no particular order.
Before enabling this policy, you should create the scripts and copy them to the system volume (sysvol) on the domain controller. By default, the login scripts are stored in the system volume (SYSVOL) on the domain controller in the directory:
\\domain\SYSVOL\domain\Scripts
\scriptname1
\scriptname2
...
After enabling this policy, click Add and enter the following information:
-
Script: The name of the script and an optional path, which are relative to
\\domain\SYSVOL\domain\scripts\For example, if the domain name is
ajax.organd you enter a script name ofstart.sh, the script that gets executed on the domain controller is:\\ajax.org\SYSVOL\ajax.org\Scripts\mlogin.sh
You can specify additional relative directories in the path, if needed; for example, if you type submlogin.sh, the file that gets executed is:
\\ajax.org\SYSVOL\ajax.org\Scripts\sub\mlogin.sh
- Parameters: An optional set of arguments to pass to the script. These arguments are interpreted the same way as in a UNIX shell; that is, space is a delimiter, and backslash is an escape character. You can also use
$USERto represent the current user's name. For example:
arg1 arg2 arg3
arg1 'a r g 2' arg3
Be certain authenticated users have permission to read these files so the scripts can run when they log in.
Once this group policy is enabled, it takes effect when users log out and log back in.
Scripts (LaunchDaemons)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (launchDaemons)
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (LaunchDaemons) > Specify multiple LaunchDaemon scripts group policy to deploy scripts that run when launchd starts (system boot up). When you use this group policy, the LaunchDaemon scripts are stored in the Active Directory domain’s system volume (sysvol) and transferred to the Mac computer when the group policies are applied. Using LaunchDaemons to run scripts allows you to run the scripts as root, where the Specify multiple login scripts group policy can only be run as the logged in user.
Refer to the following Apple resources to learn more about Launch Daemons and Agents.
- https://developer.apple.com/library/content/documentation/MacOSX/Conceptual/BPSystemStartup/Chapters/CreatingLaunchdJobs.html
- https://developer.apple.com/library/content/technotes/tn2083/_index.html#//apple_ref/doc/uid/DTS10003794
Specify Multiple LaunchDaemon Scripts
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Scripts (launchDaemons) > Specify multiple LaunchDaemon scripts
Description
Enable this group policy to specify multiple scripts to run automatically when launchd starts (system boot up).
The scripts you specify run simultaneously in no particular order.
Before enabling this policy, you should create the scripts and copy them to the system volume (sysvol) on the domain controller. By default, the LaunchDaemon scripts are stored in the system volume (SYSVOL) on the domain controller in the directory:
\\domain\SYSVOL\domain\Scripts
\scriptname1
\scriptname2
...
After enabling this policy, click Add and enter the following information:
-
Script: The name of the script and an optional path, which are relative to
\\domain\SYSVOL\domain\scripts\.For example, if the domain name is
ajax.organd you enter a script name ofstartup.sh, the script that gets executed on the domain controller is:\\ajax.org\SYSVOL\ajax.org\Scripts\startup.sh
You can specify additional relative directories in the path, if needed; for example, if you type submlogin.sh, the file that gets executed is:
\\ajax.org\SYSVOL\ajax.org\Scripts\sub\startup.sh
- Parameters: An optional set of arguments to pass to the script. These arguments are interpreted the same way as in a UNIX shell; that is, space is a delimiter, and backslash is an escape character. For example:
arg1 arg2 arg3
arg1 'a r g 2' arg3
Security & Privacy
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy
Description
Use the IBM group policies found in Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy to manage the Keychain, public and private keys, and the options from the Security & Privacy ( ) system preference on Mac OS X computers.
) system preference on Mac OS X computers.
Auto Generate New Login Keychain
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy Settings > Auto Generate New Login Keychain
Description
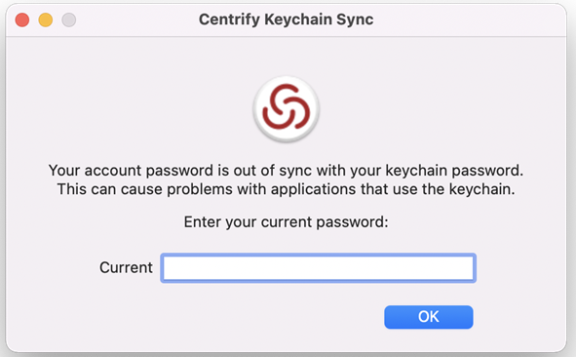
Use this policy to automatically generate a new login keychain if a user’s keychain password does not match the password they used to successfully login, resulting in the message “the system was unable to unlock your login keychain”.
This commonly occurs if someone has changed their account password on another system.
If this policy is enabled, a new keychain will be generated when a password sync issue is discovered. This new keychain will be set as the default login keychain and the previous keychain will be moved to a backup.
IBM Security recommends disabling this policy if you plan to use Enable Keychain Synchronization.
This policy is disabled by default.
Certificate Validation Method
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Certificate validation method
Description
Specify the certificate validation method to use for the Mac computer.
This group policy has no effect on the “Keychain Access > Preferences > Certificates” settings. Keychain Access > Preferences are per-user settings, which are not used by a Mac computer during login. This group policy changes IBM SmartCardTool > Revocation settings, which represent the system settings used by a Mac computer during login.
This policy allows you to choose either one, or both of the two common methods for verifying the validity of a certificate:
-
Certificate Revocation List: Use a certificate revocation list (CRL) from a revocation server.
-
Online Certificate Status Protocol: Use an online certificate status protocol (OCSP) responder to validate certificates.
If you select this option, you can specify a local responder to override the one provided in the certificates.
For each validation option, you can select one of the following settings:
-
Off: No revocation checking is performed.
-
Best attempt: The certificate passes unless the server returns an indication of a bad certificate.
This setting is recommended for most environments.
-
Require if cert indicates: If the URL to the revocation server is provided in the certificate, this setting requires a successful connection to a revocation server as well as no indication of a bad certificate.
Specify this option only in a tightly controlled environment that guarantees the presence of a CRL server or OCSP responder. If a CRL server or OCSP responder is not available, SSL and S/MIME evaluations could hang or fail.
-
Require for all certs: This setting requires successful validation of all certificates.
Use only in a tightly controlled environment that guarantees the presence of a CRL server or OCSP responder. If a CRL server or OCSP responder is not available, SSL and S/MIME evaluations could hang or fail.
-
Local Responder: If you choose to validate the certificate via OCSP, you can specify a local responder to override that provided in the certificates.
-
Priority: The priority determines which method (OCSP or CRL) is attempted first.
If the first method chosen returns a successful validation, the second method is not attempted, unless you choose to require both.
Disable Automatic Login
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Disable automatic login
Description
Disable the automatic login setting. If you enable this group policy, it overrides the Login Options set in the General tab of the Security & Privacy system preference.
For this group policy, clicking Disabled or Not Configured has no effect.
Once enabled, this group policy takes effect when the computer is rebooted.
Disable Location Services
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Disable Location Services
Description
Disable the “Enable Location Services” setting. If you enable this group policy, it overrides the Enable Location Services setting in the Privacy tab of the Security & Privacy system preference.
As of MacOS Catalina, it is not enough to wait for the next group policy refresh or execute adgpupdate. You also need to restart the Mac for this GP to take effect.
For this group policy, clicking Disabled or Not Configured has no effect.
Once enabled, this group policy takes effect at the next group policy refresh interval.
Enable Smart Card Support
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Enable smart card support
Description
Enable users to logon with smart cards. If you enable this group policy, it adds smart card support to the authorization database on Mac computers that are linked to the group policy object.
IBM Security smart card support for macOS is based on the macOS modern native framework, CryptoTokenKit
See Configuring a Mac Computer for Smart Card Login for details.
Select Enable smart card support for the SUDO command, then when executing the SUDO command, smart card user can authenticate identity by smart card PIN.
Select Enable smart card support for the SU command, then when executing the SU command, smart card user can authenticate identity by smart card PIN.
Select Enable smart card support for the LOGIN command, then when executing the LOGIN command, smart card user can authenticate identity by smart card PIN.
Select Enforce smart card login, then only smart card users with a smart card can log in to the Mac machine.
Edit Exception group to add a exception group for the "Enforce smart card login", then any users belong to this group always can log in to the Mac machine by a username and password. In general, we recommend set a exception group, for example, admin, when Enforce smart card login is selected.
Select one of options in Certificate trust behavior to set smart card certificate trust behavior, the meaning of number:
0: Smart card certificate trust isn’t required.
1: Smart card certificate and chain must be trusted.
2: Certificate and chain must be trusted and not receive a revoked status.
3: Certificate and chain must be trusted and revocation status is returned valid.
Once enabled, this policy takes effect dynamically at the next group policy refresh interval.
Enable FileVault 2
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Enable FileVault 2
Description
This group policy allows you to select whether to use one institutional key for multiple Mac computers, or computer-specific (“personal”) keys.
To use one institutional key for multiple Mac computers, select Use Institutional Recovery Key. Then click Select to select the certificate that contains the FileVault master keychain that can unlock the encrypted disk. You must already have created a FileVault master keychain and exported the certificate for the master keychain to a Windows domain server before you perform this step.
To use computer-specific (“personal”) keys instead of one institutional key, leave Use Institutional Recovery Key unchecked. In this situation, a personal recovery key is created for the Mac computer and stored in the computer object in Active Directory. The key is created and sent to the computer object in Active Directory after the “Managed By” user logs in, logs out, and provides the user password.
This policy is available only for OS X 10.9 and later.
For complete instructions, see Configuring Filevault 2.
Enabling this group policy does not immediately enable FileVault 2 protection on a Mac computer. FileVault 2 protection is enabled when the FileVault-enabled user (that is, the “Managed By” user) logs on to the computer. Disabling this group policy does not disable FileVault 2 protection — disabling FileVault 2 can only be done manually.
Once enabled, this group policy takes effect at the next group policy update interval or when you execute the adgpupdate command.
Enable Gatekeeper
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Enable Gatekeeper
Description
Enable the Gatekeeper feature, which controls access to the Mac App store. This policy overrides the “Allow applications downloaded from” setting on the General tab of the Security & Privacy system preference pane.
After enabling the policy, select one of the following options:
- Mac App Store Only allow installation of applications that have been downloaded from the Mac App store.
- Mac App Store and identified developers. Only allow installation of applications that have been downloaded from the Mac App Store or were created by Apple-sanctioned developers.
- Anywhere Allow installation of any applications.
Enable Keychain Synchronization
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Enable Keychain synchronization
Description
This group policy controls whether to enable keychain synchronization, which synchronizes the login keychain to the login user’s AD password when a password change is detected.
Keychain synchronization is password-focused and should not be used in smart card environments.
Set the Password change detection interval (minutes) option to determine the time (in minutes) between checking for changed passwords. There is a random zero to five minute variance in the actual interval each device is checked for a changed password to maintain performance. As a result, the minimum interval is five minutes.
The default value is 30 minutes.
The Store AD password in the login Keychain option is used to streamline updates of the user's login Keychain password. If this option is enabled the Keychain Sync utility stores the user's AD password in the login keychain the next time the user logs in. If the password is changed after the policy is enabled but before the previous password is stored in the login keychain, the keychain sync application requests the previous password.
When this option is selected, the user's AD password is encrypted using a static AES256 key that is unique to that user and stored in the login Keychain as an application password. The key and password are added to the keychain using the SecItemAdd API. In addition, an Access Control List ensures that only the Keychain Sync utility can access the key used to encrypt and decrypt the password.
IBM Security recommends disabling Auto Generate New Login Keychain before enabling this policy
Please note the following limitations with the Store AD Password in the login Keychain option:
-
This option only works on macOS 10.12 or later.
-
The user’s AD password is inaccessible when the login keychain is locked.
The most common scenario that causes this is if a user’s AD password is changed and the user logs out before synchronizing the keychain, then logs back in. When the user logs back in, the password check fails due to the new password, locking the login Keychain and preventing the Keychain Sync utility from accessing it.
-
Password changes can only be detected when the machine is in connected mode.
User experience when the AD password is already stored in the login Keychain
-
The login user receives a password change notification when his/her password is changed remotely.
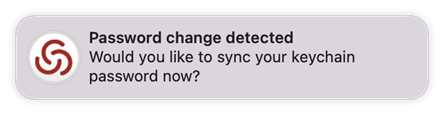
-
When the user clicks Yes on the notification, the IBM Security Keychain Sync utility appears and asks for the current password to synchronize the keychain.
After entering the current password and clicking OK, the Keychain Sync utility synchronizes the login keychain with the new password.
User experience when the AD password is not yet stored in the login Keychain
-
The login user receives a password change notification when his/her password is changed remotely.

-
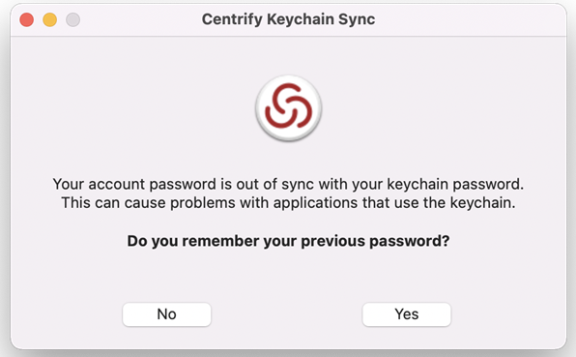
When the user clicks Yes on the notification, the IBM Security Keychain Sync utility appears and asks if the user remembers the previous password.
-
The user clicks Yes or No.
-
If the user clicks No, the Keychain Sync utility creates a new login keychain.
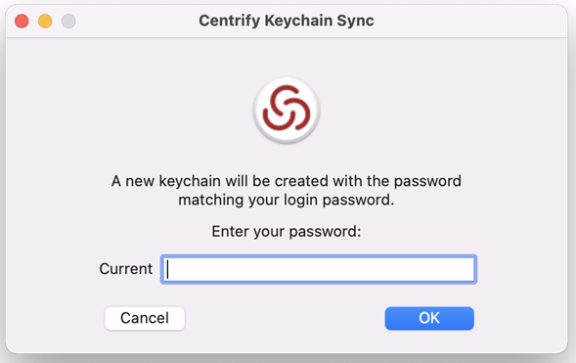
-
If the user clicks Yes, the Keychain Sync utility asks for the previous and current passwords.
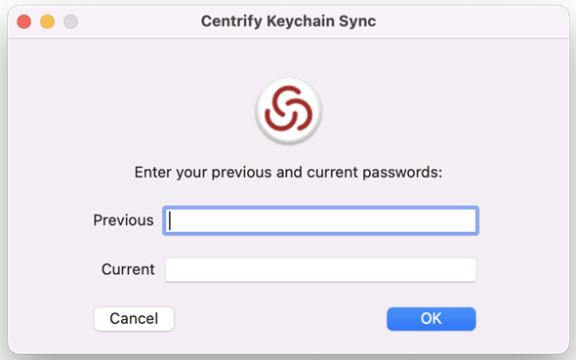
After entering the previous and current passwords and clicking OK, the Keychain Sync utility synchronizes the login keychain with the new password.
Log Out After Number of Minutes of Inactivity
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Log out after number of minutes of inactivity
Description
Specify the number of minutes of inactivity to allow on a computer before automatically logging out the current user. The default value is 5 minutes.
Setting the value to less than 5 minutes disables automatic logout. If you plan to disable automatic logout, it is recommended that you set the value to 0 to preserve backward compatibility.
Disabling this policy does not disable automatic logout.
This policy takes effect when users log out and log back in after the next group policy refresh.
Require a Password to Wake this Computer from Sleep or Screen Saver
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy Settings > Require a password to wake this computer from sleep or screen saver
This group policy only supports macOS 10.15 and lower.
Description
Lock the computer screen when the computer goes into sleep or screen saver mode and requires users to enter a user name and password to unlock the screen.
Enabling this group policy is the same as clicking the Require a password to wake this computer from sleep or screen saver option in the Security system preference.
After this group policy is enabled, it takes effect dynamically at the next group policy refresh interval.
Require Password to Unlock Each Secure System Preference
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Require password to unlock each secure system preference
Description
Lock sensitive system preferences to prevent users who aren’t administrators from changing them. This group policy requires users to provide an administrator’s password to unlock each secure system preference before they can make changes.
If you enable this policy, users must provide an administrator password to access any secure system preference. If the current user is logged on as an administrator and this policy is not configured or disabled, the user can access and change secure system preferences without providing the administrator password.
This policy can take effect dynamically at the next group policy refresh interval.
Use Secure Virtual Memory
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Use secure virtual memory
Description
Prevent passwords from being recoverable from virtual memory.
Any time a password is entered, it is possible for system to write that password in a block of memory that it dumps to a file in /var/vm, making the password recoverable.
Enabling this group policy ensures that the virtual memory /var/vm files are encrypted, preventing any passwords written there from being recovered.
This policy can take effect dynamically at the next group policy refresh interval.
Allow All Applications to Access the Auto-Enrollment Private Key(S)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Public Key Policies > Allow all applications to access the auto-enrollment private key(s)
Description
Enabling this policy allows all applications to access the auto-enrollment private key(s) in the System keychain.
See Configuring Auto-Enrollment for more information about auto-enrollment keys.
This setting only applies to a new auto-enrollment private key(s); it will not update already imported auto-enrollment private key(s) that are in the System keychain.
Allow Specific Applications to Access the Auto-Enrollment Private Key(S)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Public Key Policies > Allow specific applications to use the auto-enrollment private key(s)
Description
Enabling this policy allows specified applications to access the auto-enrollment private key(s) in System keychain.
After you enable this policy, click Add to enter the path to the application you want to allow access to the auto-enrollment private key, then click OK. You can click Add again to add additional applications.
For example, to give Google Chrome and IBM Security Agent access to the auto-enrollment private key, enter the application path for Google Chrome:
/Applications/Google Chrome.app
Click OK. Then click Add and enter the application path for IBM Security Agent:
/Applications/Centrify Agent.app
After this group policy is enabled, the list of applications specified in the group policy are added to the access control list of the auto-enrollment private key in System keychain.
See Configuring Auto-Enrollment for more information about auto-enrollment keys.
This setting only applies to a new auto-enrollment private key. It does not change auto-enrolled private keys that are already in the keychain.
If the group policy Allow all applications to access the auto-enrollment private key(s) (above) is enabled, this group policy will be ignored.
Do Not Allow the Private Key(S) to be Extractable
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Public Key Policies > Do not allow private key(s) to be extractable
Description
Enabling this policy prevents exporting the auto-enrollment private key(s).
This setting only applies to a new auto-enrollment private key. It does not change the auto-enrolled private key(s) that are already in the keychain.
Store The Private and Public Key(S) Only in the Keychain
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Security & Privacy > Public Key Policies > Store the private and public key(s) only in the keychain
Description
Enable this group policy to store the auto-enrollment key(s) only in the keychain.
User certificate auto-enrollment always uses the Keychain and is not controlled by any Group Policy.
802.1X profiles installed through the "Mac OSX Settings -> 802.1X Settings" Group Policies will no longer be signed if this GP is enabled before profiles are installed.
Services
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services settings to manage access to the service options from the Sharing ( ) system preference on Mac computers. These group policies correspond to the options displayed on the Services pane. For example:
) system preference on Mac computers. These group policies correspond to the options displayed on the Services pane. For example:
Enable Personal File Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Personal File Sharing
Description
Allow users on other Mac computers access to Public folders on the local computer. If you enable this group policy, all users can access files in the Public folder through the Apple File Sharing protocol. Users with appropriate permission can also access other folders on the local computer if properly authenticated.
Enabling this group policy is the same as opening the Sharing system preference, selecting File Sharing, then clicking the Options button and selecting the Share Files and Folders using AFP option.
On Mac OS X Servers, enabling this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Windows Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Windows Sharing
Description
Allow users on Windows computers access to shared folders on the local computer through SMB/CIFS file shares.
Enabling this group policy is the same as opening the Sharing system preference, selecting File Sharing, then clicking the Options button and selecting the Share Files and Folders using SMB option.
On Mac OS X Servers, this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Personal Web Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Personal Web Sharing
Description
Allow users on other computers to view Web pages in each user’s sites folder on the local computer.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Web Sharing option.
On Mac OS X Servers, enabling this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Remote Login
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Remote Login
Description
Allow users on other computers to access this computer using SSH.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Remote Login option.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable FTP Access (deprecated)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable FTP Access
Description
Allow users on other computers to exchange files with this computer using FTP applications.
Enabling this group policy is the same as opening the Sharing system preference, selecting File Sharing, then clicking the Options button and selecting the Share Files and Folders using FTP option.
On Mac OS X Servers enabling this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Apple Remote Desktop
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Apple Remote Desktop
Description
Allow others to access this computer using the Apple Remote Desktop program.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Remote Management option.
If you enable this group policy, you can set the following access privileges:
- Allow guest users to request permission to control the screen
- Prevent VNC viewers from controlling the screen.
Because allowing VNC viewers to control the screen requires setting a password to take control of the screen and this behavior presents a potential security issue, this group policy can only be used to disallow VNC access.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Remote Apple Events
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Remote Apple Events
Description
Allow applications on other Mac computers to send Apple Events to the local computer.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Remote Apple Events option.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Printer Sharing
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Printer Sharing
Description
Allow other people to use printers connected to the local computer.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Printer Sharing option.
On Mac OS X Servers, enabling this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Enable Xgrid
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Services > Enable Xgrid
Description
Allow clustered Mac OS Xgrid controllers to distribute tasks to the local computer for completion.
Enabling this group policy is the same as opening the Sharing system preference and selecting the Xgrid Sharing option.
On Mac OS X Servers enabling this policy has no effect.
This policy can take effect dynamically at the next group policy refresh interval without rebooting the computer.
Software Update Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Software Update Settings
Description
Use the Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Software Update Settings group policies to manage software updates. The group policies in this category enable you to set the interval for checking for software updates and to identify a specific server from which updates should be received.
These group policies correspond to settings you make using the Software Update ( ) system preference on client Mac OS X computers and the Software Update preference in the Workgroup Manager on Mac OS X servers. For example, the interval for checking for software updates is typically configured Software Update system preference on client Mac computers:
) system preference on client Mac OS X computers and the Software Update preference in the Workgroup Manager on Mac OS X servers. For example, the interval for checking for software updates is typically configured Software Update system preference on client Mac computers:
Identifying a software update server to use for downloading updates is configured on a Mac OS X server using the Software Update preference in the Workgroup Manager. For example:
The software update group policies are computer policies, applied as the root user, and apply to all users of the computer. Setting these group policies updates the plist files for individual users with the group policy parameters, such as update server URL, update interval, and so on. However, to prevent local users from using Software Update in System Preferences to manually set software update server parameters, an administrator should also limit access to the Software Update Preferences Pane by setting the group policy, Limit Items Shown in System Preferences, and then enabling the group policy, Enable System Preferences Pane: System > Enable Software Update.
Otherwise, you may see anomalous behavior. For example, a user can open Software Update and change parameters, such as disabling software updates (by deselecting Check for updates). If the user then re-enables software updates, the update server resets to the Apple software update server, not the server specified in the software update server group policy. However, at the next login, or at the next adgpupdate period, the Server URL and other group parameters will be re-applied.
The Software Update Settings contain separate folders that allow you to specify a different update server for each operating system version that you are running. For example, if you have computers with different versions of OS X in your environment, you can specify a different update server for each one by enabling the Specify software update server policy in each of the version-specific folders. In order to do this you must enable Use version specific settings.
If you do not enable Use version specific settings, Legacy Settings are used instead. If you applied Software Update Settings to computers running previous versions of the product, those settings are in Legacy Settings, though you may update them if you wish.
The Automatically download and install software updates policy applies to all computers, regardless of version.
Automatically Check For Software Updates (Legacy, Currently Supported)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Software Update Settings > Automatically check for software updates (Legacy, Currently supported)
Description
There are actually separate versions of this policy in version-specific folders.
Periodically check for updated versions of the software installed on the local computer and automatically download and install newer versions. You can configure the version-specific versions of this policy the same way you can configure the Software Update system preference for the corresponding operating system version.
This policy takes effect when users log out and log back in.
Use Version Specific Settings
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Software Update Settings > Use version specific settings
Description
Enable the use of version-specific settings.
You can then set platform-specific preferences settings for each platform in your environment, which enables you to specify a different update server depending on the version of Mac OS X running on a computer. For example, if you have only 10.10 computers, you can enable this policy and then use Mac OS X 10.10 settings. If you have 10.10 and 10.9 computers, enable this policy, and then configure the version-specific policies as appropriate:
- Mac OS X 10.10 Settings
- Mac OS X 10.9 Settings
If this policy is disabled or not configured, Legacy Settings are used instead of version-specific settings. Likewise, IBM Security versions prior to 4.4.2 always use Legacy Settings and ignore this policy setting.
If you configured Software Update Settings with a version of the product prior to 4.4.2, these settings are saved to Legacy Settings when you upgrade to the current IBM Security version. You can keep or edit these settings as you wish.
Specify Software Update Server (Legacy, Currently Supported)
Path
Computer Configuration > Policies > IBM Settings > Mac OS X Settings > Software Update Settings > Specify software update server (Legacy, Currently supported)
Description
There are actually separate versions of this policy in version-specific folders.
This enables you to specify a separate update server based on the version of the Mac OS X computer.
Type the URL that identifies the computer you are using as the software update server. It is recommended that you specify the hostname of the server rather than the IP address; for example:
http://myHost.local:8088
In addition, to ensure that DNS associates the hostname of the update server with the IP address, add a line such as the following to the /etc/hosts file:
192.168.2.79 myHost.local
where: 192.168.2.79 is the IP address of the update server and myHost.local is the hostname.
This policy can take effect dynamically at the next group policy refresh interval.