Creating and Using Roles and Desktops
At the end of the last chapter, you restarted the Windows client computer and logged in with your administrator account.
This chapter describes how to define access rights and create roles that grant elevated privileges, assign roles to users and groups, and view details about the rights and roles available. This chapter also shows you how to select and switch between roles for running local applications and connecting to network computers.
Verifying that your Account is Assigned Basic Login Rights
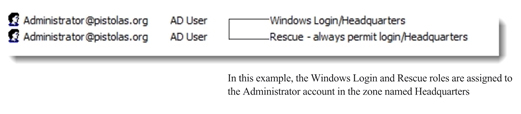
At this point, you should be logged on to the Windows client computer with an administrator account that has been assigned the “Windows Login” and “Rescue always permit login role” predefined roles as described in Assigning Yourself the Default Windows Login Role. Because the client computer has Access Manager and the Agent for Windows installed, you can verify that your account has been assigned these predefined roles using Access Manager or the Authorization Center.
To use Access Manager to verify your assigned roles:
-
Expand Zones and the zone you created in Creating the First Zone.
-
Expand Authorization and select Role Assignments.
In the right pane, you should see your role assignments displayed similar to this:
Assigning the Windows Login Role to a Group
After a computer joins a zone, users must be granted access to that computer by being assigned a role with the right to log on. So far, only the Administrator account has that privilege. This exercise illustrates how you can give that privilege to other users through their Active Directory group membership.
In most cases, you can assign the Windows Login role to all local Windows users, all Active Directory users, or both, if you want to automatically allow new users to log on locally or remotely. However, the Window Login role does not override any native Windows security policies. For example, if the Local Security Policy on the domain controller does not allow Domain Users to log on locally, assigning the Windows Login role to the Domain Users security group will not allow members of that group to log on locally.
If the Windows client computer you are using for the evaluation does not allow
users to log on locally or does not accept remote desktop connections, you might
have to make Eval Group a member of a specific Windows security group, such as
Server Operators or Remote Desktop Users, to complete further exercises.
To assign the Windows Login role to an Active Directory group:
-
On the Window client computer, open Access Manager.
-
Expand the zone, then expand Authorization.
-
Right-click Role Assignments and select Assign Role.
-
Select Windows Login from the list of role definitions, then click OK to display Assign Role.
By default the role is set to start immediately and never expire.
-
Select Accounts below to assign the role to the group you created in Creating an Active Directory User and Group.
For purposes outside of this exercise, you could assign the role to more users by selecting All accounts and then specifying All Active Directory accounts, _All local Windows accounts, All local UNIX accounts, or any combination of these three selections.
-
Click Add AD Account to display Add User Role Assignment.
-
Change the Find filter from User to Group.
-
Type all or part of the group name, click Find Now, then select the group in the results and click OK.
For example, type
Evalto search forEval Groupand select that group in the results. -
Click OK to complete the assignment and close the Assign Role window.
Now all members of
Eval Groupcan log on to this computer.
To verify the role assignment, you can log off as the administrator and log in
as the user you created in Creating an Active Directory User and Group, for
example, amy.adams. When you log on using the new account, the default desktop
has no administrative privileges. For example, the new user cannot stop or start
services on the local computers because the account do not have the
administrative privileges required to do so. The next exercise shows you how to
give a user elevated privileges when she is running a specific application.
Adding Predefined Rights to a Zone
There are many predefined rights available that grant access to specific Windows applications. For example, there is a predefined Performance Monitor right that allows you to run Performance Monitor on a computer without being a local administrator or knowing an administrative password.
You can add any or all of these predefined rights to any zone so they are available to include in role definitions. Alternatively, you can add predefined rights to individual role definitions without adding them to zones. In either case, you create grant predefined rights in the context of a role definition.
To add predefined rights to a zone and the Windows Login role:
-
On the Windows client computer, open the Access Manager console.
-
Expand Zones and the parent zone or child zones until you see the zone (for example, Headquarters) where you want to add predefined rights.
-
Expand Authorization > Role Definitions.
-
Select the Windows Login role definition, right-click, then select Add Right.
-
Select Any Windows Rights from the Type list to filter the list of rights displayed.
-
Select the Headquarters zone from the list of zones, and then click Create Predefined Rights.
The list of predefined rights that you can add to the Headquarters zone and to the Windows Login role is displayed. In the next steps, you will select which rights to add to the Headquarters zone. From the rights that you add to the Headquarters zone, you will select which, if any, to also add to the Windows Login role.
-
From the list of predefined rights, select the rights that you want to add to the Headquarters zone and to the Windows Login role, and then click OK.
By default, all of the predefined rights that you select will be added to the Headquarters zone and to the Windows Login role. In the next step, you will deselect rights so that they are added only to the zone and not to the role.
-
Deselect predefined rights that you do not want to add to the Windows Login role.
Rights that you deselect are added only to the Headquarters zone. Rights that you leave selected are added to both the Headquarters zone and the Windows Login role.
-
Click OK to add the predefined rights to the zone, role, or both according to your selections in Step 8.
If you deselected all available predefined rights, the OK button is not available to click. In this scenario, click Cancel to add the rights to the zone without adding them to the role definition.
After you perform this step, the predefined rights that you deselected are not added to the Windows Login role, but are added to the Headquarters zone so that they can be added later to roles in the zone as needed.
You can click Refresh in Access Manager to see the predefined rights listed as Windows application rights.
Creating an Application Right
An application right lets you run a specific application as a different user. An administrator assigns an application right rather than a desktop right when the user needs only occasional administrative responsibilities for a specific application and needs only temporary or infrequent use of the elevated privileges. (Desktop rights provide administrative access to more than a single application at a time. See Creating a Desktop Right for details about desktop rights.)
If you have completed the exercises in the previous sections, you are ready to create your first application right. If you have not completed all of the exercises to this point, you might not be able to perform all of the following exercises successfully.
In the following exercises, you will:
- Verify the Active Directory domain user
amy.adamsdoes not have permission to use the Windows Control Panel to change security settings. - Configure a new application right that gives administrative privileges for the Control Panel application.
- Define a new role that uses the application right.
- Assign the role definition that includes the Control Panel application right
to the Active Directory domain user
amy.adams. - Verify that the role assignment grants the user
amy.adamsthe right to change a setting in Control Panel.
To verify the user does not have administrative privileges for the Control Panel:
-
On the Windows client computer, log on as the amy.adams domain user account.
-
Use Windows Explorer to open the C:\Windows\System32 folder.
-
Create a shortcut for the control.exe program on the desktop.
-
Use the shortcut to open the Control Panel, select System and Security, then open Allow a program through Windows Firewall.
Notice that you cannot make changes to the list of Allowed programs and features. If you click Change Settings, you are prompted to enter an administrator account name and password.
-
Click Cancel to close Allow programs to communicate through Windows Firewall and close the Control Panel.
-
Log off as amy.adams and log on with your administrator account.
To create a new application right for the Control Panel:
-
On the Windows client computer, open Access Manager and expand to display Authorization > Windows Right Definitions.
-
Select Applications, right-click, then select New Windows Application.
-
On the General tab, type Control Panel Right for the name of this application right and an optional description.
-
Click the Match Criteria tab, then click Add.
In the Match Criteria tab, you specify one or more application executable files to be included in this application right. You can specify application executable files in many ways. The capability to specify more than one executable file in a single application right takes into account situations in which one application might reside in different locations on different computers. For details about different ways of specifying executable files, see the “Defining desktop application rights” help topic in the Access Manager online help.
In this example, you will specify one application executable file using the application executable name and path.
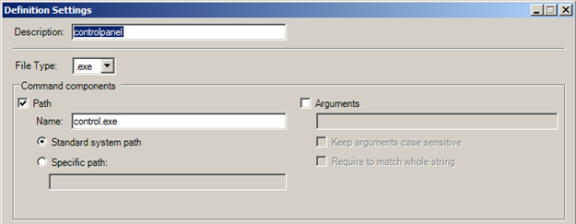
-
Type a name for the criteria definition, select Path, then type the application executable name control.exe to specify the Windows Control Panel as the application to which this right grants access. For example:
-
Click OK to use the default standard system path for the application without specifying any other criteria.
-
Click the Run As tab, select Self with added group privileges, then click Add Built-in Groups to select the administrative group to use.
For the evaluation, you should use a built-in group to avoid adding test users and groups to your Active Directory environment. Alternatively, you could specify an existing user account, create a new user account for this right, or select Self with added group privileges, then click Add AD Groups to search for and select a previously-defined Active Directory group with administrative privileges.
-
Select the Administrators group, then click OK.
-
Select Re-authenticate current user to require users to authenticate their identity when they use a role with this right.
-
Select Require multi-factor authentication If you would like to enable multi-factor authentication for the right.
Before you enable multi-factor authentication, you should be aware that multi-factor authentication for IBM Security-managed Windows computers relies on the infrastructure provided by Privileged Access Service. For more information on preparing to use multi-factor authentication, see the Multi-factor Authentication Quick Start Guide.
-
Click OK again to complete the definition of the application right.
The new application right is now defined. Next you must create a new role definition to use the application right.
-
To update the list of application rights in Access Manager so that you can review the new application right, select Action > Refresh.
To define a new role with an application right for the Control Panel:
-
Select Role Definitions, right-click, then select Add Role.
-
In the General tab, type ControlPanelAdmin as the name of the new role.
Do not change the default settings for the System Rights tab and the Audit tab.
-
Click OK.
The new role definition is created, but the role does not have any rights yet.
-
Select the ControlPanelAdmin role listed under Role Definitions, right-click, then select Add Right.
-
Select Control Panel Right in the list of rights, then click OK.
You can filter the list of rights. For example, you can filter rights by name, type, zone, or description. After you select the right and click OK, the role definition has one right. You can add other rights to it. After you have identified all of the access rights for the role definition, you can assign the role to a user or group.
To assign the role definition with the application right to a user or group:
- Select Role Assignments, right-click, then select Assign Role.
- Select ControlPanelAdmin in the list of role definitions, then click OK to display Assign Role.
- Click Add AD Account to search for and select the user amy.adams, then click OK.
- Select Role Assignments to see that the user amy.adams is assigned the Windows Login and ControlPanelAdmin roles.
- Open the Privilege Elevation Service Settings (from the Agent Configuration shortcut > Privilege Elevation Service > Settings), click the Troubleshooting tab, then click Refresh to force the agent to get the latest authorization information without waiting for the cache to expire.
To verify the user has administrative privileges for the Control Panel:
-
Log off as the administrator and log in as amy.adams.
-
Right-click the control.exe shortcut on the desktop.
If you want to open an application from the Start menu, press the Shift key when you right-click.
-
Select Run with Privilege.
Selecting Run with Privilege is similar to selecting standard Windows “Run as” or “Run as administrator” menu items, but does not require you to provide a password for an administrative or shared service account. Instead, you always use your own password to authenticate your identity.
-
Select ControlPanelAdmin in the list of the roles available, then click OK.
-
Type the password for the amy.adams login account, then click OK.
-
Select System and Security, then open Allow a program through Windows Firewall.
Notice that you can now make changes to the list of programs allowed through the firewall.
This section showed you how to set up a role that allows privilege escalation for a single application and how the user can select that role to run the application with privileges without knowing the administrator’s user name or password.
Creating a Desktop Right
In the preceding section, you saw how to elevate privileges by creating an application right for a specific application. To grant administrative access to more than a single application at a time, you can allow users to open a desktop that has administrative privileges.
If you have completed the exercises in the previous sections, you are ready to create your first desktop right. If you have not completed all of the exercises to this point, you might not be able to perform the following exercise successfully.
In the next exercise, you will create a desktop access right, create a new role,
assign the desktop right to the new role, and assign the role to Eval Group. At
the end of this exercise, you will use the desktop right to modify a restricted
folder. The steps in this exercise are similar to the steps that you performed
in the preceding exercise to create an application right.
To create a role definition with a desktop access right:
-
Log on with your administrator account and open Access Manager.
-
Create the new desktop right.
-
Select Windows Right Definitions > Desktops, right-click, then select New Windows Desktop.
-
Type DesktopRight as the name of the new desktop right on the General tab.
-
Click the Run As tab, then click Add Built-in Groups.
-
Select the Administrators group, then click OK.
-
Select Re-authenticate current user to require users to authenticate their identity when they use a role with this right, then click OK.
-
Select Require multi-factor authentication If you would like to enable multi-factor authentication for the right.
Before you enable multi-factor authentication, you should be aware that multi-factor authentication for Verify Privilege Server Suite-managed Windows computers relies on the infrastructure provided by Privileged Access Service. For more information on preparing to use multi-factor authentication, see the Multi-factor Authentication Quick Start Guide.
-
-
Create a new role definition.
- Select Role Definitions, right-click, then select Add Role.
- Type DesktopAdmin as the name of the new role on the General tab.
- Click OK.
-
Add the desktop right to the new role.
- Select Role Definitions, right-click the DesktopAdmin role, and select Add Right.
- Select DesktopRight and click OK.
-
Assign the role to a group.
- Select Role Assignments, right-click, then select Assign Role.
- Select DesktopAdmin from the list and click OK to display Assign Role.
- Click Add AD Account.
- Change the Find filter from User to Group.
- Search for and select the group you created for the evaluation (for example, Eval Group), then click OK.
- Verify that the account is included in the Accounts list in the Assign Roles dialog box, then click OK.
- Open the Privilege Elevation Service Settings (from the Agent Configuration shortcut > Privilege Elevation Service > Settings), click the Troubleshooting tab, then click Refresh to get the latest authorization information.
To verify that the role with desktop rights grants elevated privileges:
-
Log off as the administrator and log on as amy.adams.
-
Open Windows Explorer and go to the C:\Windows folder.
-
Try to create a new folder in this location.
From the default desktop for this account, the user does not have the necessary privileges to create a new folder. The only way she can create a new folder is by using administrator credentials.
-
Click the carat in the system tray notification area to display hidden icons, then click the IBM Security icon to display the applet options.
-
Select New Desktop.
-
Select the DesktopAdmin role, then click OK.
-
Type the password for the logon account, then click OK.
Notice that your new role is displayed when you left click on the IBM Security icon in your task bar.
-
Try to create a new folder in the C:\Windows directory.
Now you can create a new folder because the desktop that you are using has all of the rights associated with the Administrators group.
On Windows 10 and Windows Server 2016 systems, task bar menus are not available in an Elevated Desktop.
In this exercise, you created a role with the right to create a desktop with administrator privileges. You found that opening a new desktop with that role allowed you to perform administrative functions using your own credentials.
Switching Among Active Desktops
You can have multiple desktops available for you to use. For example, you might have separate desktop roles for managing Exchange and SQL Server that grant different rights. After you create a desktop for each role, you can switch between desktops by clicking the Verify Privilege Server Suite icon, then selecting the desktop you want to use. You can also set up hot keys to switch between desktops using a keystroke combination.
When you are finished working with a desktop, you can click the Verify Privilege Server Suite icon, then select Close Desktop.
Creating a Network Right
In the preceding section, you saw how you can provide a user with a desktop that has elevated privileges on a local computer (the Windows client computer in this case). However, using administrative privileges on your local Windows client computer does not give you privileges on a remote computer. In this section, you create a network access right that gives a user administrator privileges on a remote computer.
To illustrate network access rights using the local Windows client computer and a remote computer, you must install the Agent for Windows on the remote computer and join that remote computer to the zone you created in Creating the First Zone.
You can use the domain controller or another computer as the remote computer for this exercise. Install the Agent for Windows on the computer that you are using as the remote computer and join that computer to the Headquarters zone before proceeding.
If you are using only one Windows client computer for the evaluation and cannot install the agent on the domain controller or another remote computer, you should skip this exercise.
To prepare for the exercise that demonstrates this feature:
-
Install the Agent for Windows on the computer that you are using as the remote computer.
See Installing the Agent for Windows for more information.
-
Log on to the remote computer with your administrator account and create a folder on the C: drive named ShareFolder.
-
Select the folder, right-click, then select Properties.
-
Click the Sharing tab, then click Share.
-
Select Find people, type “back” to search for and select the built-in Backup Operators group, then click OK.
-
Right-click the Backup Operators group and set the Permission Level to Read/Write, then click Share.
-
Click Done, click Close to exit, then log off the remote computer as the administrator.
-
Log on to the local Windows client computer as amy.adams.
-
Try to open ShareFolder on the remote computer.
-
Verify that Windows tells you that you do not have sufficient permissions, then click Cancel.
To create a network access right and add it to the DesktopAdmin role:
-
Log on to the local Windows client computer with your administrator account and open Access Manager.
-
Create the new network access right.
-
Select Windows Right Definitions > Network Access_, right-click, then select New Network Access.
-
Type ShareAccess as the name of the new access right on the General tab.
-
Click the Access tab, select Self with added group privileges, then click Add Built-in Groups.
-
Select the Backup Operators group, then click OK.
-
Select Re-authenticate current user to require users to authenticate their identity when they use a role with this right, then click OK.
-
Select Require multi-factor authentication If you would like to enable multi-factor authentication for the right.
Before you enable multi-factor authentication, you should be aware that multi-factor authentication for IBM Security-managed Windows computers relies on the infrastructure provided by the Privileged Access Service. For more information on preparing to use multi-factor authentication, see the Multi-factor Authentication Quick Start Guide.
-
-
Add the new right to the existing DesktopAdmin role.
- Under Role Definitions, select the DesktopAdmin role, right-click, then select Add Right.
- Select the ShareAccess right in the list, then click OK.
-
Assign the role to a selected computer in the zone.
- Expand the zone to Computers > computer name> Role Assignments node. If you are using a local and remote computer for this exercise, select the remote computer for making the role assignment.
- Select Role Assignments, right-click, then select Assign Role.
- Select DesktopAdmin in the list of roles, then click OK.
-
Assign the role to an Active Directory group.
- Click Add AD Account.
- Change the Find filter from User to Group to search for and select the group you created for the evaluation (for example, Eval Group), then click OK.
- Verify that the account is included in the Accounts list in the Assign Roles dialog box, then click OK.
- Open the Privilege Elevation Service Settings (from the Agent Configuration shortcut > Privilege Elevation Service > Settings), click the Troubleshooting tab, then click Refresh to get the latest authorization information.
To verify the role with network access rights grants elevated privileges:
-
Log on to the local Windows client computer as amy.adams.
If you try to open ShareFolder in the default desktop, Windows denies access.
-
Open the applet, select New Desktop, and select the DesktopAdmin role.
This role has the network access right that gives you remote access to the computer running as the account with Read/Write permission.
-
Open ShareFolder and verify that Windows gives you access.
In this exercise, you added a remote access right to a role that already had a desktop right and saw how changing desktops changes the user’s rights.
Reviewing Rights and Roles in the Authorization Center
The Authorization Center is an option available from the applet menu. You can use the Authorization Center to display detailed information about your currently available rights and role assignments.
To view the Authorization Center:
- Click the IBM Security icon in the notification area.
- Select Open Authorization Center.
- Click through the tabs to view detailed information about your rights, roles, role assignments, and auditing status.