Creating a Unix Discovery Source
Discovery sources define a set of discovery operations. You must create a discovery source based on the built-in types prior to running discovery.
Creating the Discovery Source
See Creating a Discovery Source for details.
Editing Unix Discovery Source Scanners
-
Select Discovery > Sources. The Sources tab of the Discovery page appears.
-
In the list of existing discovery sources, click the name of the one you want to edit.
-
Select the Scanners tab. The Discovery flow for that source and its scanners appear:
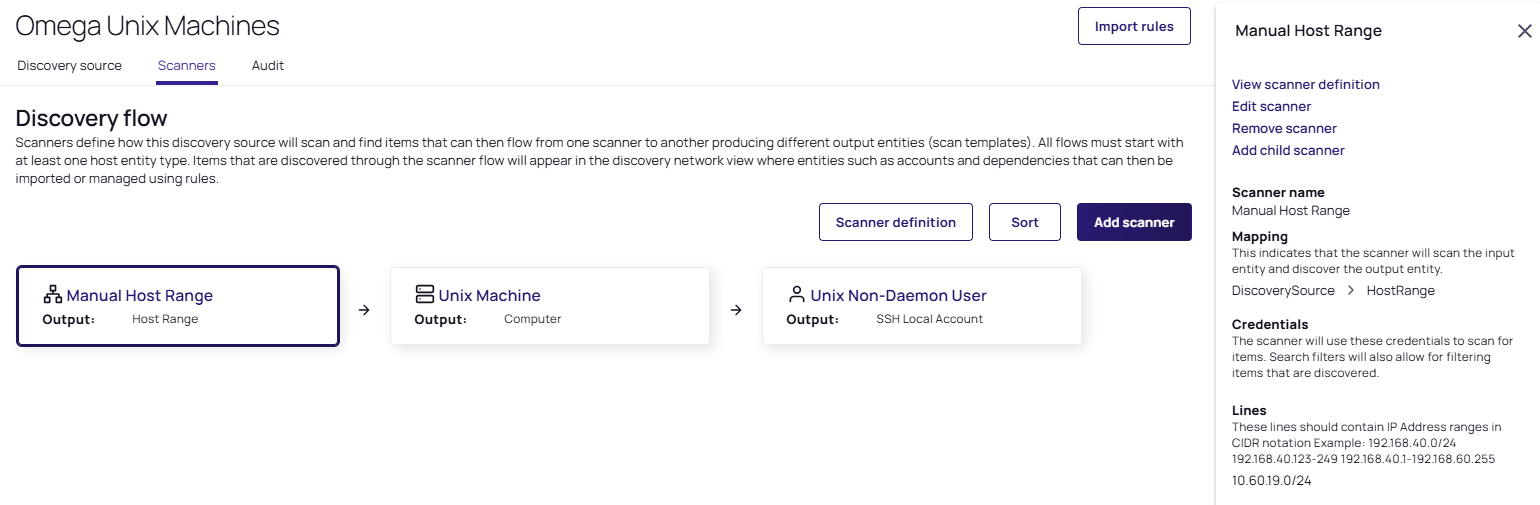 To add a dependency scanner, one needs to be available which has an input template matching an unused output scan template. The output template must be unique for each scanner, but the input template may be shared.
To add a dependency scanner, one needs to be available which has an input template matching an unused output scan template. The output template must be unique for each scanner, but the input template may be shared. -
Manual Host Range is typically the first scanner of the discovery source, which is the input template. This means the initial data comes from information you enter into the discovery source when you create it. The output template is named Host Range.
-
Click the Manual Host Range scanner. The details pop-out appears to the right of the screen. Note the following:
- You have four links at the top, View scanner definition, Edit scanner, Remove scanner, and Add child scanner.
- The Mapping section indicates the scanner will look through the input entity and discover the output entity. For this scanner these are DiscoverySource and HostRange, respectively.
-
The Credentials section displays the secret credentials used to scan for items and allows for filtering.
- The Unix discovery source finds all machines and local accounts on a set of manually defined host ranges for Unix machines accessible with SSH.
- The Lines section lists multiple, distinct IP address ranges on the same discovery source.
-
The Unix Machine scanner is the consumer of the Computer output template, and has the following configurations available that differ from the previous scanner:
- The Mapping section the input entity that is used and what the scan will discover as the output entity. For example: HostRange > Computer.
-
The Ports section displays the comma-separated list of port values (1-65535) used for the scanner.
-
The Max TCP Connections section determines how many concurrent TCP connections will be used during a scan.
-
The Attempt Authentication option allows the server to attempt to login and determine the operating system of any machines found. This requires a Credential Secret and a Command Set.
-
The Parse Format option details the format in which the scanner will parse the operating system and hostname from a found machine after the commands are run, when using authenticated scanning.
-
The Identify computer by host name option, if true, allows for computers to be considered unique by host name, not just their IP address. This is helpful if one machine is bound to multiple IP addresses. If you change this option after having run discovery any secrets previously linked will not automatically transfer to the new computer.
-
The Unix Non-Daemon User scanner has the following configurations available that differ from the previous scanners:
- The User Regex Format text box contains a regular expression that finds the lines of text received during the scan that are valid for user parsing. The matched groups in the regular expression should correspond to the comma-separated items in the parse format.
- The Parse Format text box defines the order of values retrieved during a scan. If the parse names match the fields defined in the imported secret, the values are populated from the data collected on the scan.
- The Newline Separator Character dropdown defines the character that divides the lines in the output received during a scan.