Creating Computer Groups
To add new Computer Groups for your organization’s environment:
-
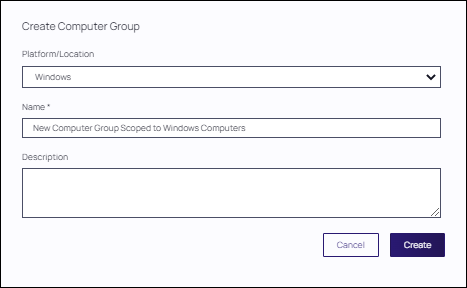
On the Computer Groups page, click Create Computer Group.
-
From the Platform/Location drop-down list box, select macOS, Secured Scope, Unix/Linux, or Windows.
-
From the Create Computer Group window, enter a Name and Description for your new group.
Creating Filter Rules and Collections
When initially created, the computer group includes all computers in the platform you selected. To further refine the computers you want to include in the computer group, you add filter rules. Rules target the appropriate computers in your organization’s network by including or removing certain groups, collections, or Active Directory Organizational Units (OUs)..
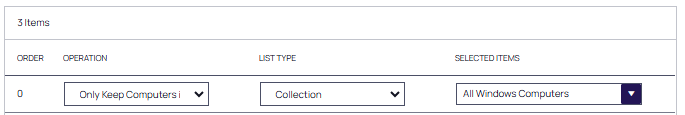
The default Only Keep Computers in rule must appear last. Include Computers In or Remove Computers In rules are used to include or exclude specific computers from the computer group at a more granular level, using a combination of Operation and List Type parameters.
-
Click Add Rule.
-
First, specify an Operation behavior. Options include:
Operation
Behavior Only Keep Computers in Only Keep Computers In removes all computers that are not in the List Type you select.
Include Computers in This operation allows you to add additional computers from a List Type you select.
(This is useful if you have filtered out too many computers in a prior operation and just need to add back a select few.)Remove Computers in This operation allows you to remove certain computers identified in a List Type you select.
(This is useful if you have added too many computers in a prior operation and need to exclude specific computers from that list.) -
In the List Type column, identify the type of computers that the operation will target. Then, click Add to identify specific computers from that list. Options include:
List Type Target Computer List Lists specific computers from your list of registered machines. Collection Lists built-in collections of computers, such as All Windows Desktops or All Windows Servers, as well as any custom Resource Targets and Collections you have created.
OU/Scope The Organizational Units (OUs) available for selection are defined when computers were imported into Verify Privilege Manager. Security Group Security Groups are defined by controls that limit who can view data associated with specific computers. Refer to Security Configuration. The last operation defined in a rule should be Only Keep Computers In for either All Windows Computers or All MacOS Computers to ensure that any incompatible computers will be excluded from the computer group.
Never add Include Computers In for All Windows Computers or All MacOS Computers as the last rule in the computer group. This causes unnecessary entries in the group, resulting in increased processing times in the database.
-
Ensure that the last rule is Only Keep Computers In for All Windows Computers or All MacOS Computers by creating this rule last or moving the default 0 rule to the end of the configuration.
-
Click Save Changes. The new computer group appears in the table.
-
Select the Results tab to verify the computers you have defined in the computer group.
Example
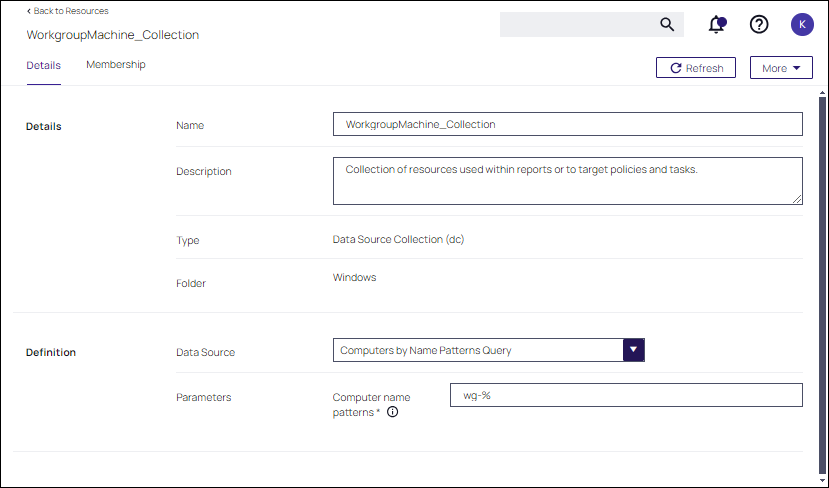
When defining a Collection, you can use the ready-made Items in the Computers Group you have created. (Windows Servers, Windows Desktops, etc.). Or, you can create a custom resources group.
In this example, a custom group for machines whose machine name starts with "wg-" is created.
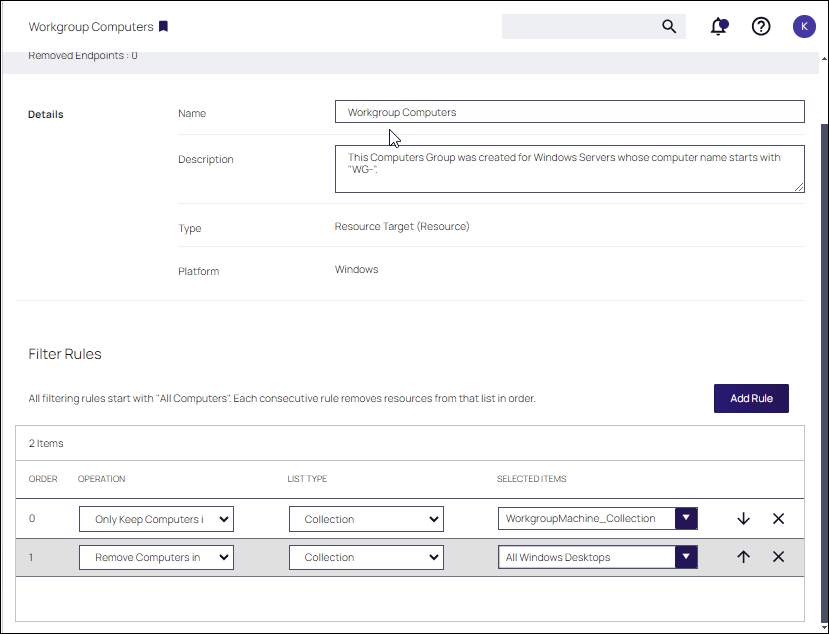
Then, this resource group is added to the computer group.
The computer group must start with Only Keep Computers in. Then, Include Computers In or Remove Computers In rules can be used. In this example, a computer collection whose machine names starts with WG- and are not Windows desktops are added.
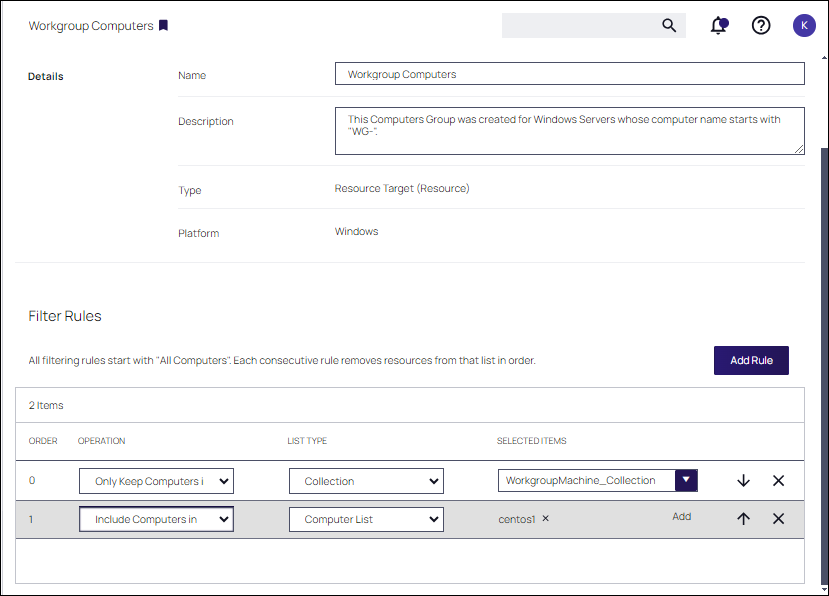
As an alternative to using Collection, you can also use OU/Scope, Security Group and Computer List to Include Computers Inor Exclude Computers In. In this example, the collection of computers whose names starts with wg-, and are named centos1 will be members of this group.
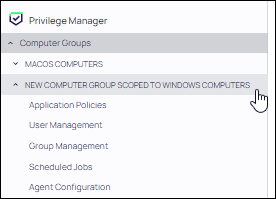
Defining Policies, User Management, and Agents
Expand the left navigation tree for the new computer group. Click the available features (Application Policies, User Management, Group Management, Scheduled Jobs, and Agent Configuration) to further configure the computer group.
For example:
Refer to the following sections:
-
Application Policies (Windows, macOS, Unix/Linux)
- Policies associated with Application Control that you establish using the Create Wizard policy.
- User Management (Windows, macOS)
-
Group Management (Windows, macOS)
- Local security control that pertains to specific groups of users.
-
Scheduled Jobs (Windows, macOS, Unix/Linux)
- Client tasks that you designate to run on certain dates and at certain times. Verify Privilege Managersets many scheduled jobs to Active by default.
-
Agent Configuration (Windows, macOS, Unix/Linux)