Installing Verify Privilege Server Suite
This chapter describes how to install Verify Privilege Server Suite software on Windows computers in a production environment. It includes instructions for installing all identity and privilege management, audit and monitoring service, and multi-factor authentication components. It also describes how to install the Agent for Windows, and how to enable services on agent-managed Windows computers.
If your deployment plan includes identity and privilege management, as well as audit and monitoring service, you should review the details in Planning a deployment before installing any components.
In a production environment, you should use separate computers for different components to ensure scalability and performance. For information about setting up an evaluation environment on a single computer for testing, see the Evaluation Guide for Windows.
Installation Checklist
As a preview of what’s involved in the installation process, the following steps summarize what you need to do and the information you should have on hand for a successful deployment of Verify Privilege Server Suite.
To prepare for installation:
-
Analyze your network topology to determine where to install components and services and any hardware or software updates required.
For a review of the decisions to make and recommended hardware configuration, see Planning a Deployment.
-
Create a list of the computers where you plan to install different components.
For example, list the computers where you plan to install agents, collectors, audit store databases, consoles, and group policy extensions.
If you are installing the audit and monitoring service infrastructure, you should use a dedicated computer for each component, so that the audit collector service, audit store database, and audit management database are on separate computers with high-speed and reliable network connectivity.
For a review of the requirements associated with each component, see Planning a Deployment.
-
Determine the scope of the audit installation.
The most common deployment scenario is a single installation for an Active Directory site, but you can have more than one installation, if needed, and use subnets to limit the scope of the installation. If you are only implementing access management, you can skip this step, Step 4, and Step 7 through Step 10.
For a review of what constitutes an installation, see Deploying Auditing Components in an Audit Installation and decide on the scope of the installation.
-
Create Active Directory security groups for managing the permissions required for the audit and monitoring service infrastructure.
For a review of the Active Directory security groups to create, see Managing Auditing for an Installation. If you are only implementing identity and privilege management, you can skip this step.
-
Install Access Manager on at least one computer that can connect to the Active Directory forest.
-
Open Access Manager and add containers for licenses and zones to the Active Directory forest.
-
Install Microsoft SQL Server.
If you are not a database administrator in your organization, you should submit a service request or contact an administrator who has permission to create databases for assistance. For more information about preparing a SQL Server database engine for auditing, see Installing and configuring Microsoft SQL Server for Auditing. If you are only implementing access management, you can skip this step.
-
Install Audit Manager and Audit Analyzer.
For more information about installing these products, see Installing the Audit Manager and Audit Analyzer Consoles. If you are only implementing identity and privilege management, you can skip this step.
-
Open Audit Manager to create a new installation for auditing.
For more information about using Audit Manager to create a new installation and audit store, see Creating a New Installation. If you are only implementing identity and privilege management, you can skip this step.
-
Install the audit collector service on at least two Windows computers.
You can add collectors to the installation at any time. For more information about installing and configuring collectors, see Installing the Audit Collectors. If you are only implementing identity and privilege management, you can skip this step.
-
Install an Agent for Windows on each Windows computer that you want to manage or audit.
For more information about installing and configuring Agent for Windows, see Installing the Agent for Windows.
-
Install additional consoles on any Windows computer that you want to use for identity and privilege management, or audit and monitoring service.
After the initial deployment, you can add new agents, collectors, audit stores, and audit store databases to the audit installation or create additional installations at any time.
Installing Verify Privilege Server Suite and Updating Active Directory
When you install Verify Privilege Server Suite, components for the following features are installed:
-
The Identity Platform, which enables MFA login, endpoints, and
other platform services.
-
The Privilege Elevation Service, which enables users and
zone-joined computers to have elevated privileges.
-
The Audit & Monitoring Service, which enables audit and monitoring
service data to be collected and stored.
-
The Agent for Windows, which enables each computer where the agent
is installed to be managed by Verify Privilege Server Suite software.
-
The Licensing Service, which works together with Verify Privilege Server Suite
components to monitor and report usage and activity for all types of
licenses. For more information about the licensing service, see the
License Management Administrator’s Guide
You can select which features to install from the IBM Security software setup program.
After Verify Privilege Server Suite are installed, you must enable some or all of them on each agent-managed computer. The enablement step lets you decide which services are available on each agent-managed computer.
Things to remember
-
At least one zone must be created before an agent-managed computer can be
enabled to use the identity and privilege management features that you
install. If no zones are available, the agent-managed computer will not have
the option of being joined to the authentication and privilege elevation
services.
-
When the Agent is upgraded or when it adds the Identity
Platform, a corporate endpoint enrollment is performed in the Privileged
Access Service. The endpoint device moves into the endpoint category and the
device is marked as corporate owned.
Running the Setup Program on a Windows Computer
You can install components for all Verify Privilege Server Suite from the Server SuiteCD or a downloaded ISO or ZIP file. After you access the distribution media, the setup or autorun program copies the necessary files to the local Windows computer. There are no special permissions required to run the setup or autorun program other than permission to install files on the local computer.
To install IBM Security software on Windows:
-
Log on to the computer you have selected for administrative tasks and browse to the location where you have saved downloaded IBM Security software files.
If you have a physical CD, the Getting Started page is displayed automatically. If the page is not displayed, open the autorun.exe file to start the installation of IBM Security software.
-
On the Getting Started page, click Authentication & Privilege to start the setup program for authentication and privilege elevation services.
{b}Note: {/b}The Authentication & Privilege components are the recommended first components to install so that Access Manager is available for you to use to create zones. At least one zone must be created before you can enable the authentication and privilege elevation services on an agent-managed computer.
If any programs must be updated before installing, the setup program displays the updates required and allows you to install them. After updates are complete, you can restart the setup program.
-
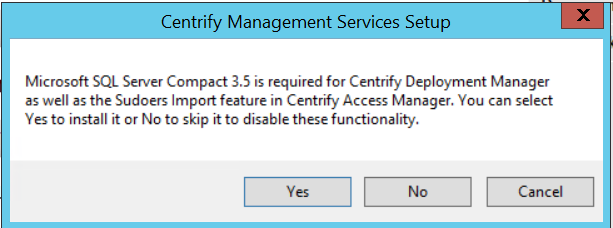
At the following screen, select Yes to install Microsoft SQL Server Compact. The Access Manager console uses the Microsoft SQL Server Compact for storage.
If you select No, Microsoft SQL Server Compact is not installed and some features of Access Manager are not available.
-
At the Welcome page, click Next.
-
Review the terms of the license agreement, click I agree to these terms, then click Next.
-
Type your name and company name, then click Next.
-
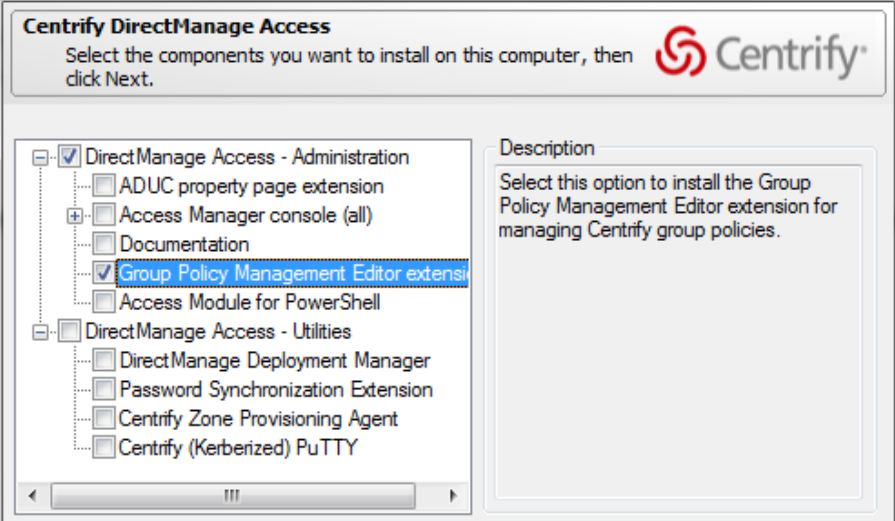
Expand and select the Administration and Utilities components you want to install, then click Next.
If you are only managing identity and privileges for Windows computers, you can install a subset of the components. For a Windows-only deployment, select the following components:
-
ADUC property page extension if you want to include profiles when displaying properties in Active Directory Users and Computers.
-
Access Manager console (all) if you want to use an administrative console to manage zones and roles.
-
Group Policy Management Editor extension if you want to deploy group policies.
Installing Report Services is optional. If you select this option, see Installing and configuring Microsoft SQL Server for Auditing for additional details.
For a Windows-only deployment, you can deselect Utilities to skip the installation of those components.
-
-
Accept the default location for installing components, or click Browse to select a different location, then click Next.
-
Review the components you have selected, then click Next.
The setup program begins installing the selected components.
-
Click Finish to complete installation.
-
Optionally install additional Verify Privilege Server Suite components as follows:
- Licensing Service. This service is installed by default
when you install the Authentication & Privilege components, and usually
does not need to be installed separately. For more information about the
licensing service, see the License Management Administrator’s Guide. - Audit & Monitor. The Auditing and Monitoring Service is not
installed automatically with any other components, and must be installed
separately if you intend to use auditing and monitoring features. For
installation details, see Installing the Audit Manager and Audit Analyzer Consoles. - Agent for Windows. To install the agent on client Windows
computers so that those computers can be managed by Verify Privilege Server Suite, see
Installing the Agent for Windows.
- Licensing Service. This service is installed by default
Opening Access Manager to Update Active Directory
The first time you start Access Manager, a Setup Wizard prepares the Active Directory forest with parent containers for licenses and zones. The Setup Wizard also sets the appropriate permissions for the objects automatically. For more information about using the Setup Wizard to update Active Directory, see Starting Access Manager for the First Time.
Installing and Configuring Microsoft SQL Server for Auditing
If you want to audit user activity on Windows, you must have at least one Microsoft SQL Server database instance for the audit management database and audit store databases. We recommend that you use a dedicated instance of SQL Server for the audit management database. A dedicated SQL Server instance is an instance that does not share resources with other applications. The audit store databases can use the same dedicated instance of SQL Server or their own dedicated instances.
There are three database deployment scenarios for your installation:
-
Evaluation—Use the SQL Server Express with Advanced Services setup program (SQLEXPRADV_x64_ENU.exe) to create a new instance of Microsoft SQL Server Express. You should only use Microsoft SQL Server Express for evaluation or for limited use in a test environment. You should not use SQL Server Express databases in a production environment.
If you choose to install a different version of Microsoft SQL Server Express for an evaluation and the version requires .NET version 3.5 SP1, you will need to manually install the .NET files yourself (the installer doesn't include these files).
-
Manual installation with system administrator privileges—Install a Microsoft SQL Server database instance for which you are a system administrator or have been added to the system administrator role.
-
Manual installation without system administrator privileges—Have the database administrator (DBA) install an instance of Microsoft SQL Server and provide you with system administrator credentials or information about the database instance so that you can create the management database and audit store databases.
Downloading and Installing SQL Server Manually
You can use an existing Microsoft SQL Server database engine or install a new instance. You can download Microsoft SQL Server software from the Microsoft website or through the (Support Portal)[https://www.delinea.com/login/?portal=support]. In selecting a version of Microsoft SQL Server to download, you should be sure it includes Advanced Services. Advanced Services are required to support querying using SQL Server full-text search.
After downloading an appropriate software package, run the setup program using your Active Directory domain account and follow the prompts displayed to complete the installation of the SQL Server database engine.
Configuring SQL Server to Prepare for Audit and Monitoring Service
After you install the SQL Server database engine and management tools, you should configure the SQL Server instance for audit and monitoring service by doing the following:
-
Depending on the version of SQL Server you install, you might need to
manually enable full text search. For example, use SQL Server Surface Area
Configuration for Services and Connections to start the full-text search
service.
-
Use SQL Server Configuration Manager to enable remote connections for
TCP/IP.
-
Use SQL Server Configuration Manager to restart the SQL Server and SQL
Server Browser services.
-
Verify whether SQL Server is using the default TCP port 1433 for network
communications. If you use a different port, you should note the port number
because you will need to specify in the server name when you create the
management and audit store databases.
Installing the Audit Manager and Audit Analyzer Consoles
You can install Audit Manager and Audit Analyzer on the same computer or on different computers. The computers where you install the consoles must be joined to the Active Directory domain and be able to access the audit management database.
In most cases, the consoles are installed together on at least one computer.
To install Audit Manager and Audit Analyzer on the same computer:
-
Log on to the computer you have selected for administrative tasks and browse to the location where you have saved downloaded IBM Security files.
If you have a physical CD that you made from the ISO image file, the Getting Started page is displayed automatically. If the page is not displayed, open the autorun.exe file to start the installation of IBM Security software.
-
On the Getting Started page, click Audit & Monitor to start the setup program for audit and monitoring service components.
In the rare case where the administrator should not have access to the Audit Analyzer, select Audit Manager, then click Next.
After you install Audit Manager, you are prompted to create a new installation. If you want to create the installation at a later time, you can run the setup program again to create a new installation.
Creating a New Installation
Before you can begin audit and monitoring service, you must create at least one installation and a management database. Creating the management database, however, requires SQL Server system administrator privileges on the computer that hosts the SQL Server instance. If possible, you should have a database administrator add your Active Directory domain account to the SQL Server system administrators role.
If you have not been added to the system administrators role, you should contact a database administrator to assist you. For more information about creating a new installation when you don’t have system administrator privileges, see How to Create an Installation without System Administrator Privileges.
To create a new installation and management database as a system administrator:
-
Log on using an Active Directory account with permission to install software on the local computer.
-
Open the Audit Manager console to display the New Installation wizard.
The New Installation wizard displays automatically the first time you start Audit Manager. You can also start it by clicking Action > New Installation or from the right-click menu when you select the Audit Manager node.
-
Type a name for the new installation, then click Next.
Name the installation to reflect its administrative scope. For example, if you are using one installation for your entire organization, you might include the organization name and All or Global in the installation name, such as AcmeAll. If you plan to use separate installations for different regions or divisions, you might include that information in the name, for example AcmeBrazil for a regional installation or AcmeFinance for an installation that audits computers in the Finance department. -
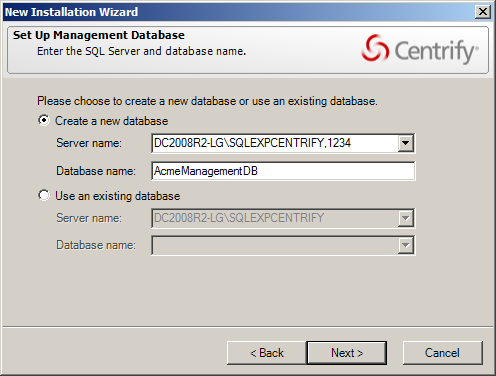
Select the option to create a new management database and verify the SQL Server computer name, instance name, and database name are correct, then click Next.
If the server does not use the default TCP port (1433), you must provide the server and instance names separated by a backslash, then type a comma and the appropriate port number. For example, if the server name is ACME, the instance name is BOSTON, and the port number is 1234, the server name would be ACME\BOSTON,1234.
If you’re connecting to a SQL Server availability group listener, click Options (next to the Server Name) and enter the following connection string parameters:
MultiSubnetFailover=Yes
-
Type the license key you received, then click Add or click Import to import the keys directly from a file, then click Next.
-
Accept the default location or click Browse to select a different Active Directory container to which you want to publish audit-related information, then click Next.
-
Select Enable video capture recording of user activity if you want to capture a full video record of desktop activity on Windows computers when users are audited, then click Next.
Selecting this option enables you to review everything displayed during an audited user session, but will increase the audit store database storage requirements for the installation. You can deselect this option if you are only interested in a summary of user activity in the form of audit trail events. Audit trail events are recorded when users log on, open applications, and select and use role assignments with elevated rights.
-
Review details about the installation and management database, then click Next.
If you have SQL Server system administrator (sa) privileges and can connect to the SQL Server instance, the wizard automatically creates the management database.
-
Select the Launch Add Audit Store Wizard option if you want to start the Add Audit Store wizard, then click Finish.
If you want to create the first audit store database at a later time, you should deselect the Launch Add Audit Store Wizard option and clickFinish.
For more information about adding the first audit store database, see Creating the First Audit Store.
How to Create an Installation without System Administrator Privileges
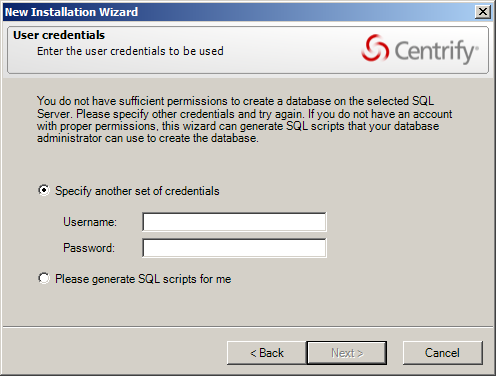
If you do not have the appropriate permission to create SQL Server databases, you cannot use the New Installation wizard to create the management database without the assistance of a database administrator.
If you do not have system administrator privileges, the wizard prompts you to specify another set of credentials or generate SQL scripts to give to a database administrator. For example:
If you don’t have a database administrator immediately available who can enter the credentials for you, you cannot continue with the installation.
To create an installation when you don’t have system administrator privileges:
-
Select the option to generate the SQL scripts, then click Next.
-
Select the folder location for the scripts, then click Next.
-
Review details about the installation and management database you want created, then click Next.
The wizard generates two scripts: Script1 prepares the SQL Server instance for the management database and Script2 creates the database.
-
Click Finish to exit the New Installation wizard.
-
Send the scripts to a database administrator with a service or change control request.
{b}Note: {/b}You should notify the database administrator that the scripts must be run in the proper sequence and not modified in any way. Changes to the scripts could render the database unusable.
-
After the database administrator creates the database using the scripts, open the Audit Manager console to run the New Installation wizard again.
-
Type the name of the installation, then click Next.
-
Select Use an existing database and verify the database server and instance name, then click the Database name list to browse for the database name that the database administrator created for you.
If the server does not use the default TCP port, specify the port number as part of the server name. For example, if the port number is 1234, the server name would be similar to ACME\BOSTON,1234.
-
Select the database name from the list of available databases, click OK, then click Next.
-
You should only select an existing database if the database was created using scripts provided by IBM Security.
-
Type a license key or import licenses from a file, then click Next.
-
Review details about the audit management database to be installed, then click Next.
-
Select the Launch Add Audit Store Wizard option if you want to start the Add Audit Store wizard, then click Finish.
Create the First Audit Store
If you selected the Launch Add Audit Store Wizard at the end of the New Installation Wizard, the Add Audit Store Wizard opens automatically. You can also open the wizard at any time by right-clicking the Audit Stores node in the Audit Manager console and choosing Add Audit Store.
To create the first audit store:
-
Type a display name for the audit store, then click Next.
{b}Tip: {/b}If your plan specifies multiple audit stores, use the name to reflect the sites or subnets serviced by this audit store. Note that an audit store is actually a record in the management database. It is not a separate process running on any computer. You use a separate wizard to create the databases for an audit store.
-
Click Add Site or Add Subnet to specify the sites or subnets in this audit store.
-
If you select Add Site, you are prompted to select an Active Directory site.
-
If you select Add Subnet, you are prompted to type the network address and subnet mask.
The Windows components for DirectAudit now support IPv6. The Add Subnet dialog for subnet-based scopes requires both IPv4 and IPv6 subnets in CIDR format (e.g., 192.168.16.0/24 or fe80::1234::/64). This approach simplifies the UI and accommodates IPv6, which lacks old-style subnet masks. A tooltip displays the required format when hovering over the input field.
After you make a selection or type the address, click OK. You can then add more sites or subnets to the audit store. When you are finished adding sites or subnets, click Next to continue.
The computer you use to host the audit store database should be no more than one gateway or router away from the computers being audited. If your Active Directory sites are too broad, you can use standard network subnets to limit the scope of the audit store.
-
-
Review information about the audit store display name and sites or subnets, then click Next.
-
Select the Launch Add Audit Store Database Wizard option if you want to create the first audit store database, then click Finish.
Create the Audit Store Database
If you selected the Launch Add Audit Store Database Wizard check box at the end of the Launch Add Audit Store Wizard, the Add Audit Store Database Wizard opens automatically. You can also open the wizard at any time from the Audit Manager console by expanding an audit store, right-clicking the Databases node, and choosing Add Audit Store Database.
To create the first audit store database:
-
Type a display name for the audit store database, then click Next.
The default name is based on the name of the audit store and the date the database is created.
-
Select the option to create a new database and verify that the SQL Server computer name, instance name, and database name are correct.
The default database name is the same as the display name. You can change the database name to be different from the display name, if you want to use another name.
If the server does not use the default TCP port, specify the port number as part of the server name. For example, if the port number is 1234, the server name would be similar to ACME\BOSTON,1234.
When entering the SQL Server host computer name, note that you can enter either the server short name (which is automatically resolved to its fully qualified domain name, or FQDN) or the actual server FQDN or the CNAME alias for the server.
If the database is an Amazon RDS SQL Server:
-
Select the This is an Amazon RDS SQL Server option.
-
In the Server Name field, enter the RDS SQL Server database instance endpoint name used for Kerberos authentication.
For example, if the database host name is northwest1 and the domain name is sales.acme.com, then the endpoint name would be northwest1.sales.acme.com.
Click Options to enter additional connection string parameters or to enable data integrity checking.
- You can enable or disable data integrity checking once, when you create
the audit store database. To change the state, you must rotate to a new
audit store database.
-
Connecting to SQL Server on a Remote Computer
To create an audit store database on a remote computer, there must be a one-way or two-way trust between the domain of the computer on which you are running the Add Audit Database wizard and the domain of the computer hosting SQL Server. The Active Directory user account that you used to log on to the computer where the Audit Manager is installed must be in a domain trusted by the computer running SQL Server. If there is no trust relationship, you must log on using an account in the same domain as the computer running SQL Server. If you are accessing the computer running SQL Server remotely, you can use the Run As command to change your credentials on the computer from which you are running the wizard.
Verify Network Connectivity
The computer hosting the SQL Server database for the active audit store server be online and accessible from the Audit Manager console and from the clients in the Active Directory site or the subnet segments you have defined for the audit store. You should verify that there are no network connectivity issues between the computers that will host collectors and those hosting the SQL Server databases.
How to Create the Database without System Administrator Privileges
If you do not have system administrator privileges, the wizard prompts you to specify another set of credentials or generate SQL scripts to give to a database administrator. If you don’t have database administrator credentials or a database administrator immediately available who can enter the credentials for you, you should generate the scripts, then follow the prompts displayed to exit the wizard.
To add the database to the audit store after you have generated the scripts:
-
Send the scripts to a database administrator with a service or change control request.
{b}Note: {/b}You should notify the database administrator that the scripts must be run in the proper sequence and not modified in any way. Changes to the scripts could render the database unusable.
-
After the database administrator creates the database using the scripts, open the Audit Manager console.
-
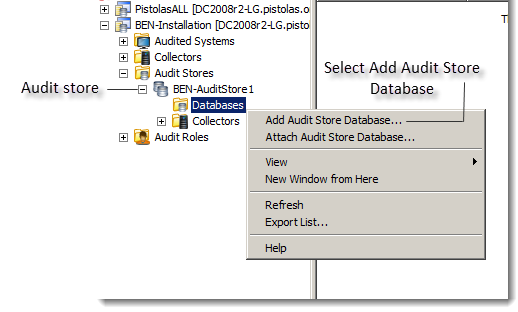
Expand the installation node, then expand Audit Stores and the specific audit store you for which you want a new database.
-
Select Databases, right-click, then click Add Audit Store Database. For example:
-
Type a display name for the audit store database, then click Next.
-
Select Use an existing database and select the database that the database administrator created for you.
Because this is the first audit store database, you also want to make it the active database. This option is selected by default. If you are creating the database for future use and don’t want to use it immediately, you can deselect the Set as active database option.
If the server does not use the default TCP port, specify the port number as part of the server name. For example, if the port number is 1234, the server name would be similar to ACME\BOSTON,1234.
The installation, management database, and first audit store database are now ready to start receiving user session activity. Next, you should install the collectors and, finally, the agents to complete the deployment of the audit and monitoring service infrastructure.
Installing and Configuring Audit Collectors
After you have created a new installation, with an audit management database and at least one audit store and audit store database, you must add the collectors that will receive audit records from the agents and forward those records to the audit store. For redundancy and scalability, you should have at least two collectors. For more information about planning how many collectors to use and the recommended hardware and network configuration for the collector computers, see Deciding Where to Install Collectors and Audit Stores.
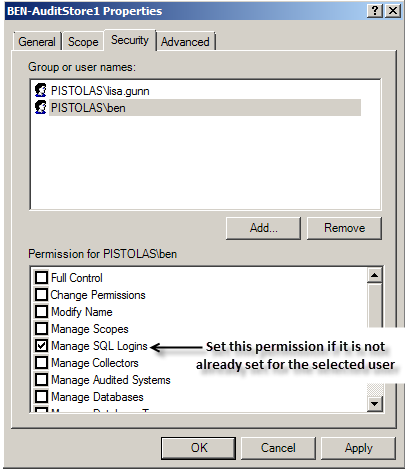
Set the Required Permission
Before you configure a collector, you should check whether your user account has sufficient permissions to add new collector accounts to the audit store database. If you are a database administrator or logged on with an account that has system administrator privileges, you should be able to configure the collector without modifying your account permissions. If you have administrative rights on the computer hosting Audit Manager but are not a database administrator, you can set the appropriate permission before continuing.
To set the permission required to add accounts to the audit store database:
-
Open Audit Manager.
-
Expand the installation, then expand Audit Stores.
-
Select the audit store that the collector will connect to, right-click, then click Properties.
-
Click the Security tab.
-
Click Add to search for and select the user who will configure the collector.
-
Select the Manage SQL Logins right, then click OK.
Install the Collector Service Using the Setup Program
If your user account has sufficient permissions to add new collector accounts to the audit store database, you can install a collector by running the setup program on a selected computer. When prompted to select components, select Audit Collector and deselect all of the other components, then click Next. Follow the instructions in the wizard to select the location for installing files and to confirm your selections, then click Finish to complete the installation.
Configure the Audit Collector Service
By default, when you click Finish, the setup program opens the Collector Configuration Wizard. Alternatively, you can start the configuration wizard at any time by clicking Configure in the Collector Control Panel.
To configure the collector service:
-
Type the port number to use, then click Next.
The default port is 5063 for communication from agents to the collector. If you want to use a different port, the wizard checks whether the port is open in the Windows firewall.
If you’re running another firewall product, open the port with the tools provided by that product. If there’s an upstream firewall—such as a dedicated firewall appliance—between the Collector and the computers to be audited, contact the appropriate personnel to open the port on that firewall.
-
Select the installation of which this collector will be a part, then click Next.
The configuration wizard verifies that the installation has an audit store that services the site that the collector is in and that the collector and its audit store database are compatible.
-
Select whether you want to use Windows authentication or SQL Server authentication when the collector authenticates to the audit store database, then click Next.
In most cases, you should choose Windows authentication to add the computer account to the audit store database as a trusted, incoming user.
If Microsoft SQL server is in a different forest or in an untrusted forest, you should use SQL Server Management Studio to set up one or more SQL Server login accounts for the collector. After you create the SQL Server login account for the collector to use, you can select SQL Server authentication, then type the SQL Server login name and password in the wizard.
-
Choose the maximum number of connections you want for the SQL Server Connection Pool, then click Next.
-
Review your settings for the collector, then click Next.
-
Click Finish to start the collector service and close the wizard.
Installing the Agent for Windows
You must install an agent on every Windows computer that you want to manage or audit. You can install the agent in the following ways:
-
Interactively, by running the setup program on each computer.
When the installation finishes, the agent configuration panel launches automatically. You can configure the agent to enable IBM Security services right away, or exit the configuration panel and configure the agent later. See Installing the Agent for Windows interactively using the setup program for details about this installation method.
-
Silently, by executing appropriate commands in a terminal window on each computer. This method also requires you to configure the agent registry settings on each computer. See Installing the Agent for Windowssilently on remote Windows computers for details about this installation method.
A variation of this method is to use a third-party software distribution product, such as Microsoft System Center Configuration Manager (SCCM), to execute the appropriate command line remotely, so that the software is deployed on remote computers. Using a third-party software distribution product is not covered in this guide.
-
Silently and centrally, by using a Windows group policy to execute installation and registry configuration commands remotely on each computer that is joined to the domain. See Installing the Agent for Windows silently on all domain computers by using group policy for details about this installation method.
Regardless of the deployment method you choose, you should first make sure that the computers where you plan to deploy meet all of the installation prerequisites.
Verifying Prerequisites
Before installing the Agent for Windows, verify the computer on which you plan to install meets the following requirements:
- The computer is running a supported Windows operating system version.
- The computer is joined to Active Directory.
-
The computer has sufficient processing power, memory, and disk space for the
agent to use.
-
The computer has Windows security update KB3033929 installed if it is
running Windows 7 with Service Pack 1 or Windows Server 2008 R2 with Service
Pack 1.
- The computer has .NET 4.6.2 or later installed.
- The computer has Windows Installer version 4.5 or newer.
If you are installing interactively using the setup program, the setup program can check that the local computer meets these requirements and install any missing software required. if you are installing silently or from a Group Policy Object, you should verify the computers where you plan to install meet these requirements.
Installing the Agent Interactively Using the Setup Program
The procedure in this section describes how to use the agent installation wizard to install the agent on a Windows computer. After the agent is installed, you will enable the agent to use one or more services that you installed earlier on the main administrative computer as described in Installing Verify Privilege Server Suite and updating Active Directory.
To install the agent on Windows using the setup program:
-
Insert the distribution CD into the computer on which you wish to install the agent or browse to the location where you have saved downloaded files.
-
On the Getting Started page, click Agent to start the setup program for the agent.
If the Getting Started page is not displayed, open the autorun.exe file to start the installation of IBM Security software.
-
If a previous version of the agent is installed, click Yes when prompted to upgrade the Agent for Windows.
-
At the Welcome page, click Next.
-
Review the terms of the license agreement, click I accept the terms in the License Agreement, then click Next.
-
Accept the default location for installing components, or click Change to select a different location, then click Next.
-
In the Ready to install Agent for Windows page, click Install.
-
Click Finish to complete the installation and start the agent configuration panel.
Go to Configuring the agent for details about using the agent configuration panel to enable IBM Security services and configure how the agent interacts with those services.
Configuring the Agent
By default, when you click Finish, the setup program opens the agent configuration panel. In the agent configuration panel, you can enable the agent to connect to IBM Security services that are installed on the main administrative computer as described in Installing Verify Privilege Server Suite and updating Active Directory. After a service is enabled, you can use the agent configuration panel to configure settings that define how the agent will interact with each service.
The first time the agent configuration panel opens, it does not display any services for you to enable. Services display in the agent configuration panel only after you manually instruct the configuration panel to check for services and display those that are eligible to be enabled.
Only services that are installed and configured as required are eligible to be enabled. For example, if you installed the Privilege Elevation Service earlier (as described in Running the setup program on a Windows computer) but did not create a zone, the Privilege Elevation Service does not display on the list of services that you can enable.
To enable services using the agent configuration panel:
-
If the agent configuration panel is not open, open it by clicking Agent Configuration in the list of applications in the Windows Start menu.
-
In the agent configuration control panel, click Add service.
All IBM Security services that are available to be enabled are displayed.
-
In the list of IBM Security services, highlight a service and click OK.
-
Provide additional information about the service that you are enabling:
-
Audit & Monitoring Service:
In the Select an Audit Installation page, select an audit store from the list of available audit stores. Click Next, and the computer is connected to the audit store.
-
Identity Platform Settings:
- In the Connect to Identity Platform page, type the URL of the
identity platform instance to connect to, or select an instance from
the list of registered platform instances in the forest. Click
Next. - In the Multi-factor authentication for Windows Login page, ensure
that the check box to enable multi-factor authentication is
selected. Next, use the All Active Directory accounts button or
Accounts below button to specify which Active Directory accounts
are enabled for multi-factor authentication login. If you select
Account below, use the Add and Remove buttons to select
accounts. Click Next when you are finished.
- In the Connect to Identity Platform page, type the URL of the
-
Privilege Elevation Service:
-
In the Join to a zone page, type a zone or select a zone from the list of available zones. You can also choose to select the option to retrieve the zone data before the computer restarts. This option can be helpful in situations where you might lose connection to the domain after restarting, such as when you're using a VPN connection.
Click Next, and the computer is joined to the zone.
-
After the computer is joined to a zone, you must reboot the computer to activate all privilege elevation service features on the computer.
If the zone that you select is already configured with a Privileged Access Service tenant, the message Identity Platform enabled displays after the computer joins the zone. In this situation, the instance is managed by the zone, and is shown as read-only.
-
-
-
To add additional services, click Add service and repeat the preceding steps.
When you are done, the services that you enabled are shown in the Enabled services section of the agent configuration panel.
-
If necessary, continue to configure IBM Security services after their initial configuration during enablement as described in these sections:
- Configuring agent settings for the audit and monitoring service
- Configuring agent settings for offline audit and monitoring service storage
- Configuring agent settings for the Identity Platform
- Configuring agent settings for privilege elevation
Configuring Agent Settings for the Audit and Monitoring Service
If you want to reconfigure agent settings for auditing on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the service), you can open the agent configuration panel manually and configure the agent as described in this section.
To configure agent settings for audit and monitoring service:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration panel opens, and displays the IBM Security services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Audit & Monitoring Service, and then click Settings.
-
In the General tab, click Configure.
-
Select the maximum color quality for recorded sessions, then click Next.
See Set Maximum Recorded Color Quality for more information on the configuration of this setting.
-
Specify the offline data location and the maximum percentage of disk that the offline data file should be allowed to occupy, then click Next.
See Installing Interactively Using the Setup Program for more information on the configuration of this setting.
-
Select the installation that the agent belongs to, then click Next.
-
Review your settings, then click Next.
-
Click Finish.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see Monitoring Collector Status.
Selecting the Maximum Color Quality for Recorded Sessions__
Because auditing Windows computers captures user activity as video, you can configure the color depth of the sessions to control the size of data that must be transferred over the network and stored in the database. A higher color depth increases the CPU overhead on audited computers but improves resolution when the session is played back. A lower color depth decreases network traffic and database storage requirements, but reduces the resolution of recorded sessions.
The default color quality is low (8-bit).
Configuring Agent Settings for Offline Audit and Monitoring Service Storage
The “Maximum size of the offline data file” setting defines the minimum percentage of disk space that should be available, if needed, for audit and monitoring service. It is intended to prevent audited computers from running out of disk space if the agent is sending data to its offline data storage location because no collectors are available.
For example, if you set the threshold to 10%, auditing will continue while spooling data to the offline file location as long as there is a least 10% of available disk space on the spool partition. When the available disk space reaches the threshold, auditing will stop until a collector is available.
The agent checks the spool disk space by periodically running a background process. By default, the background process runs every 15 seconds. Because of the delay between background checks, it is possible for the actual disk space available to fall below the threshold setting. If this were to occur, auditing would stop at the next interval. You can configure the interval for the background process to run by editing the
HKLM\Software\Centrify\DirectAudit\Agent\DiskCheckInterval registry setting.
Configuring Agent Settings for the Identity Platform
If you want to reconfigure agent settings for the Identity Platform on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the service), you can open the agent configuration panel manually and configure the agent as described in this section.
To configure agent settings for the Identity Platform:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration panel opens, and displays the IBM Security services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Identity Platform, and then click Settings.
-
In the General tab, review the authentication options in the Features area:
-
Multi-factor authentication:
-
If the status is Enabled, the computer is not joined to a zone, and you can configure all Identity Platform settings that are shown in the General tab.
-
If the status is Enabled per zone settings, the computer is joined to a zone, and most Identity Platform settings are based on the zone configuration.
In this situation, the Browse and Details buttons in the General tab are disabled, because those features are controlled by the zone configuration. The only configuration that you can perform in the General tab is to change the proxy server settings.
Multi-factor authentication displays in the Authentication Source drop-down once the status is Enabled per zone settings.
-
-
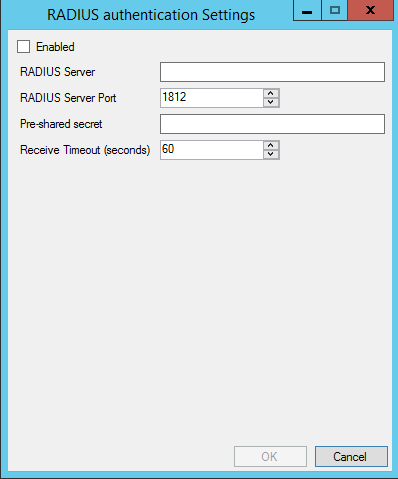
RADIUS authentication:
-
If the status is Enabled, you can select this option to use as the authentication option for privilege elevation. You can enable this option either by group policy or a local configuration setting.
-
If the status is Disabled, click Details to configure and enable the RADIUS server connection.
RADIUS authentication displays in the Authentication Source drop-down once the status is Enabled.
-
-
-
To change proxy server settings:
- Click Change.
- Specify a new proxy server address.
- Click OK.
-
To change to a different Identity Platform instance (only configurable if the computer is not joined to a zone):
- Click Browse.
- Select an instance from the list of registered platform instances in the forest.
- Click OK.
-
To specify which Active Directory accounts require multi-factor authentication (only configurable if the computer is not joined to a zone):
- Click Details.
- Use the All Active Directory accounts button or Accounts below
button to specify which Active Directory accounts are enabled for
multi-factor authentication login. If you select Account below, use
the Add and Remove buttons to select accounts. - Click OK.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see the Troubleshoot Multi-Factor Authentication.
Configuring Agent Settings for Privilege Elevation
If you want to reconfigure agent settings for privilege elevation on a Windows computer after initially configuring them during enablement (or if you did not use the agent configuration panel when you enabled the service), you can open the agent configuration panel manually and configure the agent as described in this section.
If you haven't yet configured the agent settings for privilege elevation, see Configure Multi-Factor Authentication for Privilege Elevation when the Agent Cannot Connect to the Platform for details.
To configure existing agent settings for privilege elevation:
-
In the Windows Start menu, click Agent Configuration in the list of applications.
The agent configuration control panel opens, and displays the services that are currently enabled. You can configure any service listed in the Enabled services section.
-
Click Privilege Elevation Service, and then click Settings.
-
In the General tab, click Change.
-
In Change the zone for this computer, click Browse.
-
Click Find Now to search for an appropriate zone for the agent.
-
Select a zone from the list of search results, then click OK.
-
Click OK to use the zone you selected.
-
Click Close in the General tab to save your changes.
For information about using the Troubleshooting tab, see Troubleshoot Multi-Factor Authentication.
Installing the Agent without MFA Login
If desired, you can install the Agent for Windows without the MFA login feature. This can be useful in situations where either you don't want to enforce multi-factor authentication or you don't use Privileged Access Service.
To install the Agent for Windows without the MFA login feature:
- Run the following command:
msiexec /i "Agent for Windows64.msi" /qn PRIVILEGEONLY=1
Installing the Agent for Windows Silently on Remote Windows Computers
If you want to perform a “silent” (also called unattended) installation of the Agent for Windows, you can do so by specifying the appropriate command line options and Microsoft Windows Installer (MSI) file to deploy. You must execute the commands on every Windows computer that you want to manage or audit.
You can also use a silent installation to automate the installation or upgrade of the agent on remote computers if you use a software distribution product, such as Microsoft System Center Configuration Manager (SCCM), to deploy software packages. However, installing remotely in this way is not covered in this topic.
Deciding to Install with or without Joining the Computer to a Zone
Before you begin a silent installation, you should decide whether you will wait until later to join the computer to a zone, or join the computer to a zone as part of the installation procedure.
If you install without joining a zone during installation:
-
See Configuring Registry Settings for details about the registry settings
that you can configure manually after the installation finishes.
-
See Installing Silently Without Joining a Zone for details about performing
the installation.
If you install and join a zone during installation:
-
You use a transform (MST) file that is provided with Verify Privilege Server Suite to
configure a default set of agent-specific registry keys during the silent
installation.
-
You can optionally edit the MST file before performing the installation to
customize agent-specific registry settings for your environment.
-
You can optionally use the registry editor to configure registry settings
after the installation finishes.
-
See Configuring Registry Settings for details about the registry settings
that you can configure by editing the MST file.
-
See Editing the Default Transform (MST) File for details about how to edit
the MST file before you perform the installation.
-
See Installing Silently Without Joining a Zone for details about performing the
installation.
Configuring Registry Settings
When you perform a silent installation, several registry settings specific to the agent are configured by the default MSI file. In addition, a default transform (MST) file is provided for you to use if you join the computer to a zone as part of the installation procedure. When executed together, the default MSI and MST files ensure that the computer is joined to a zone, and that a default set of agent-specific registry keys is configured.
If your environment requires different or additional registry settings, you can edit the MST file before performing an installation. Then, when you execute the MSI and MST files to perform an installation, your customized registry settings are implemented. For details about how to edit the MST file, see Editing the Default Transform (MST) File.
If you do not join the computer to a zone during installation, you do not use the MST file. In this situation, you can create or edit registry keys manually after the installation finishes by using the registry editor.
The following table describes the agent-specific registry settings that are available for you to configure during installation (by using the MST file) or after installation (by using the or the registry editor). Use the information in this table if you need to configure registry settings differently than how they are configured by the default MSI and MST files. Keep the following in mind as you review the information in the table:
-
The default MSI file is named Agent for Windows64.msi, and is
located in the Agent folder in the IBM Security download location.
-
The default MST file is named Group Policy Deployment.mst, and is located in
the Agent folder in the IBM Security download location.
-
If you want to install the agent without the MFA login feature, use the
Group Policy Deployment-PrivilegeOnly.mst, and is located in the Agent
folder in the IBM Security download location.
-
All of the settings in the following table are optional, although some are
included in the default MSI and MST files so that they are configured when
the MSI and MST files execute during an installation.
-
Settings that are included in the default MSI and MST files are noted in the
table.
-
Some settings are environment-specific, and therefore do not have a default
value. Others are not environment-specific, and do have a default value.
-
The settings described in the table are located in the MSI file’s Property
table.
-
The Setting column shows both the property name in the MSI file, and the
name (in parentheses) of the registry key in the Windows registry.
| Service | Setting | Description |
|---|---|---|
| Auditing and Monitoring | REG_MAX_FORMAT (MaxFormat) | Specifies the color depth of sessions recorded by the agent. The color depth affects the resolution of the activity recorded and the size of the records stored in the audit store database when you have video capture auditing enabled. You can set the color depth to one of the following values: 0 to use the native color depth on an audited computer. 1 for a low resolution with an 8-bit color depth 2 for medium resolution with a 16-bit color depth (default) 4 for highest resolution with a 32-bit color This setting is included in the default MSI file. In the registry, this setting is specified by a numeral (for example, 1). In the MSI file Property table, it is specified by the # character and a numeral (such as #1). The default value is 1. |
| Auditing and Monitoring | REG_DISK_CHECK_THRESHOLD (DiskCheckThreshold) | Specifies the minimum amount of disk space that must be available on the disk volume that contains the offline data storage file. You can change the percentage required to be available by modifying this registry key value. This setting is included in the default MSI file. In the registry, this setting is specified by a numeral (for example, 1). In the MSI file Property table, it is specified by the # character and a numeral (such as #10). The default value is 10, meaning that at least 10% of the disk space on the volume that contains the offline data storage file must be available. If this threshold is reached and there are no collectors available, the agent stops spooling data and audit data is lost. |
| Auditing and Monitoring | REG_SPOOL_DIR (SpoolDir) | Specifies the offline data storage location. The folder location you specify will be where the agent saves (“spools”) data when it cannot connect to a collector. This setting is not included in the default MSI file. To use it, you must edit the default transform (MST) file so that it is processed together with the MSI file during installation, or create it manually in the registry after the installation finishes. |
| Auditing and Monitoring | REG_INSTALLATION_ID (InstallationId) | Specifies the unique global identifier (GUID) associated with the installation service connection point. This setting is not included in the default MSI file. To use it, you must edit the default transform (MST) file so that it is processed together with the MSI file during installation, or create it manually in the registry after the installation finishes. |
| Auditing and Monitoring | REG_LOG_LEVEL_DA (LogLevel) | Specifies what level of information, if any, is logged. Possible values are: off information warning error verbose This setting is included in the default MSI file. The default value is information. |
| Authentication & Privilege | REG_RESCUEUSERSIDS (RescueUserSids) | Specifies which users have rescue rights. Type user SID strings in a comma separated list. For example: user1SID,user2SID,usernSIDThis setting is not included in the default MSI file. To use it, you must edit the default transform (MST) file so that the setting is processed together with the MSI file during installation, or create it manually in the registry after the installation finishes. |
| Authentication & Privilege | REG_LOG_LEVEL_DZ (LoggingLevel) | Specifies what level of information, if any, is logged. Possible values are: off information warning error verbose This setting is included in the default MSI file. The default value is information. |
| Authentication & Privilege | GPDeployment | Specifies whether the computer is joined to the zone where the computer was pre-created. This setting is used only during installation and does not have a corresponding registry key. Possible values are: 0 - The computer is not joined to the zone. 1 - The computer is joined to the zone. This setting is included in the default transform (MST) file. To use it, you must execute the MST file when you execute the default MSI file. The default value is 1, meaning that the pre-created computer is joined to the zone. |
| Authentication & Privilege | ZONEDATA | Specifies the option to retrieve the zone data before the computer restarts. This option can be helpful in situations where you might lose connection to the domain after restarting, such as when you're using a VPN connection. Possible values are: YES NO The default value is NO in the default MSI file. |
Editing the Default Transform (MST) File
This section describes how to edit the default transform (MST) file Group Policy Deployment.mst. You execute the MST file together with the installation (MSI) file during a silent installation if you want to join the computer to a zone as part of the installation.
The MST file specifies registry key settings that are different from those specified in the MSI file. You use the MST file to customize a silent installation for a specific environment. Using an MST file makes it unnecessary to edit registry keys manually after a silent installation.
{b}Note: {/b}By default, auditing features are installed when you install the Agent for Windows. The service is not enabled by default, but the service item in the configuration panel appears if the feature is enabled through group policy.
See Installing Silently Without Joining a Zone for instructions about how and when to execute the MST file.
To edit the default MST file:
-
You will use the Orca MSI editor to edit the MST file. Orca is one of the tools available in the Windows SDK. If the Windows SDK (or Orca) is not installed on your computer, download and install it now from this location:
https://msdn.microsoft.com/en-us/library/aa370557(v=vs.85).aspx
-
Execute Orca.exe to launch Orca.
-
In the Agent folder in the IBM Security download location, copy Group Policy Deployment.mst so that you have a backup.
-
In Orca, select File > Open and open the Agent for Windows64.msi file located in the Agent folder in the IBM Security download location.
-
In Orca, select Transform > Apply Transform.
-
In Orca, navigate to the Agent folder in the IBM Security download location and open Group Policy Deployment.mst.
The file is now in transform edit mode, and you can modify data rows in it.
-
In the Orca left pane, select the Property table.
Notice that a green bar displays to the left of “Property” in the left pane. This indicates that the Property table will be modified by the MST file.
The right pane displays the properties that configure registry keys when the MSI file executes. Notice that the last property in the table, GPDeployment, is highlighted in a green box. This indicates that the GPDeployment property will be added to the MSI file by the MST file.
In order for the computer to join a zone during installation, the Group Policy Deployment.mst file must specify the GPDeployment property with a value of 1.
-
In the right pane, edit or add properties as necessary to configure registry keys for your environment. See the table in Configuring Registry Settings for details about agent-specific properties that are typically set.
- To edit an existing property, double click its value in the Value column and type a new value.
- To add a new property, right-click anywhere in the property table and select Add Row.
-
After you have made all necessary modifications, select Transform > Generate Transform to save your modifications to the default MST file.
Be sure to save the MST file in the same folder as the MSI file. If the MST and MSI files are in different folders, the MST file will not execute when you execute the MSI file.
The MST file is now ready to be used as described in Installing and joining a zone silently.
Installing Silently without Joining a Zone
This section describes how to install the agent silently without joining the computer to a zone. This procedure includes configuring registry settings manually using the registry editor or a third-party tool.
To install the agent and join the computer to a zone during installation, see Installing and Joining a Zone Silently for more information.
Check prerequisites:
-
Verify that the computers where you plan to install meet the prerequisites
described in Verifying prerequisites. If prerequisites are not met, the
silent installation will fail.
-
If you are installing audit and monitoring service, verify that the
following tasks have been completed:
- Installed and configured the SQL Server management database and the SQL Server audit store database.
- Installed and configured one or more collectors.
- Configured and applied the DirectAudit Settings group policy that specifies the installation name.
To install the Agent for Windows silently without joining the computer to a zone:
-
Open a Command Prompt window or prepare a software distribution package for deployment on remote computers.
For information about preparing to deploy software on remote computers, see the documentation for the specific software distribution product you are using. For example, if you are using Microsoft System Center Configuration Manager (SCCM), see the Configuration and Tuning Reference Guide.
-
Run the installer for the Agent for Windows package. For example:
msiexec /qn /i "Agent for Windows64.msi"
By default, none of the services are enabled.
-
Use the registry editor or a configuration management product to configure the registry settings for each agent. See the table in Configuring Registry Settings for details about agent-specific registry keys that you can set.
For example, under
HKEY_LOCAL_MACHINE\Software\Centrify\DirectAudit\Agent, you could set the DiskCheckThreshold key to a value other than the default value of 10%.
Installing and Joining a Zone Silently
This section describes how to install the agent and join the computer to a zone at the same time. The procedure described here includes the following steps in addition to executing the MSI file:
-
You first prepare (pre-create) the Windows computer account in the appropriate zone.
-
You execute an MST file together with the MSI file to join the computer to a zone and configure registry settings during the installation.
{b}Note: {/b}Joining the computer to a domain is applicable only when you are enabling Authentication & Privilege features.
To install the agent without joining the computer to a zone during installation, see Installing Silently Without Joining a Zone for more information.
Check prerequisites:
-
Verify that the computers where you plan to install meet the prerequisites
described in Verifying prerequisites. If prerequisites are not met, the
silent installation will fail.
-
If you are enabling audit and monitoring service in addition to
Authentication & Privilege, verify that the following tasks have been
completed:
- Installed and configured the SQL Server management database and the SQL Server audit store database.
- Installed and configured one or more collectors.
- Configured and applied the DirectAudit Settings group policy that specifies the installation name.
To install the Agent for Windows and add a computer to a zone during installation:
-
Prepare a computer account in the appropriate zone using Access Manager or the PowerShell command New-CdmManagedComputer. See Preparing computer accounts before joining for more information.
-
You will use the default transform file Group Policy Deployment.mst in Step 3 to update the MSI installation file so that the computer is joined to the zone in which it was pre-created in Step 1. You can optionally modify GroupPolicy Deployment.mst to change or add additional registry settings during installation.
If you want to edit Group Policy Deployment.mst to change or add additional registry settings and have not yet done so, edit it now as described in Editing the default transform (MST) file.
In order for the computer to join the zone from Step 1, the Group Policy Deployment.mst file must specify the GPDeployment property with a value of 1.
-
Run the following command:
msiexec /i "Agent for Windows64.msi" /qn TRANSFORMS="Group Policy Deployment.mst"
By default, Privilege Elevation Service is enabled by joining a zone. If the zone is also configured with a platform instance (tenant), Identity Services Platform will also be enabled. If you want to enable auditing, configure the corresponding registry value in the Property page of the MST file: REG_CURRENT_INSTALLATION or via Group Policy.
You can also choose to install the specify the option to retrieve the zone data before the computer restarts. This option can be helpful in situations where you might lose connection to the domain after restarting, such as when you're using a VPN connection. To specify that the agent retrieves zone data before the computer restarts, run the following command:
msiexec /i "Agent for Windows64.msi" /qn TRANSFORMS="Group Policy Deployment.mst" ZONEDATA="YES"
The computer will be restarted automatically to complete the deployment and start the agent.
Installing the Agent for Windows Silently on All Domain Computers by Using Group Policy
You can use a group policy object (GPO) to automate the deployment of the Agent for Windows. Because automated installation fails if all the prerequisites are not met, be sure that all the computers on which you intend to install meet the requirements described in Verifying prerequisites.
If you install the Common Component before you install the agent, information about the installation of the agent can be captured in a log file for troubleshooting purposes.
To create a new group policy object for the deployment of the Agent for Windows:
-
Prepare computer accounts in the appropriate zones using Access Manager or the PowerShell command New-CdmManagedComputer. See Preparing computer accounts before joining for more information.
-
Copy the Agent for Windows64.msi and Group Policy Deployment.mst installer files to a shared folder on the domain controller or another location accessible from the domain controller.
When you select a folder for the agent installer files, right-click and select Share with > Specific people to verify that the folder is shared with Everyone or with appropriate users and groups.
-
Right-click on the Agent for Windows64.msi file, then select Edit with Orca.
-
Select Transform > Apply Transform, then select Group Policy Deployment.mst from the same location as the Agent for Windows64.msi file.
-
Select the Property table on the left hand side and add the following:
Property Value Comments REG_ZONELESS_MFA_TENANT Tenant URL (Ex: https://aaa1111.my.delinea.net:443/) Note: You must include “https://” and “:443/”. REG_ZONELESS_MFA_ENABLED true Default Value = false REG_EFFECTIVE_ZONELESS_MFA_USERS Comma-Separated user or group names, or enter * for All AD users REG_CONNECTOR_BRANDING IBM Security -
Close Orca and save the changes as a new mst file.
Make sure you save it in the same location as the msi file.
-
On the domain controller, click Start > Administrative Tools > Group Policy Management.
-
Select the domain or organizational unit that has the Windows computers where you want to deploy the Agent, right-click, then selectCreate a GPO in this domain, and Link it here.
-
For example, you might have an organizational unit specifically for IBM Security-managed Windows computers. You can create a group policy object and link it to that specific organizational unit.
-
Type a name for the new group policy object, for example, Agent Deployment, and click OK.
-
Right-click the new group policy object and click Edit.
-
Expand Computer Configuration > Policies > Software Settings.
-
Select Software installation, right-click, and select New > Package.
-
Navigate to the folder you selected previously, then select the Agent for Windows64.msi file, and click Open.
-
Select Advanced and click OK.
-
Click the Modifications tab and click Add.
-
Select the .mst file created previously, then click Open, and click OK.
-
Close the Group Policy Management Editor, right-click the Agent Deployment group policy object, and verify that Link Enabled is selected.
By default, when computers in the selected domain or organizational unit receive the next group policy update or are restarted, the agent will be deployed and the computer will be automatically rebooted to complete the deployment of the agent.
If you want to test deployment, you can open a Command Prompt window to log on to a Windows client as a domain administrator and force group policies to be updated immediately by running the following command:
gpupdate /force
After installation, all of the registry settings that were specified in the MSI and MST files are configured. If you need to further configure registry settings, use the registry editor to do so as described in Installing the Agent for Windows silently on remote Windows computers.
Installing the Agent on a Computer Running Server Core
You cannot use the autorun.exe or the setup.exe program to install components on a computer that is configured to run as a Server Core environment. Instead, you must install from Microsoft Installer (.msi) files using the msiexec command-line program.
To install the Agent for Windows on Server Core:
-
Use the Deployment Image Servicing and Management (DISM) or another command-line tool to enable the .NET Framework.
For example, if the .NET Framework is located on the installation media in the D:\sources\sxs folder, use the following command:
DISM /Online /Enable-Feature /FeatureName:NetFx3 /All /LimitAccess /Source:D:\sources\sxs
-
Copy the Agent for Windows files to the Server Core computer.
For example:
copy D:\Common\Centrify* C:\Centrify Agent
copy D:\Agent\* C:\Centrify Agent
-
Install the Common Component service using the .msi file.
For example, to install the Common Component on a computer with 64-bit architecture, you might use the following command:
msiexec /i Centrify Common Component64.msi" /qn
-
Install the Agent for Windows using the .msi file.
For example, to install the Agent for Windows with identity management, privilege elevation, auditing, and monitoring features enabled on a computer with 64-bit architecture, you might run the following command:
msiexec /qn /i "Agent for Windows64.msi" ADDLOCAL=ALL
You can also choose to install the specify the option to retrieve the zone data before the computer restarts. This option can be helpful in situations where you might lose connection to the domain after restarting, such as when you're using a VPN connection. To specify that the agent retrieves zone data before the computer restarts, run the following command:
msiexec /i "Agent for Windows64.msi" /qn TRANSFORMS="Group Policy Deployment.mst" ZONEDATA="YES"
-
Restart the computer with the appropriate shutdown options to complete the installation and start agent services.
For example, you might run the following command:
shutdown /r
Installing Additional Consoles
You can install additional consoles on any domain computers you want to use for managing access using zones or roles, or for managing the audit and monitoring service infrastructure. You also might want to install additional consoles on the computers to be used by auditors. You can install additional consoles from the Management Services setup program or from individual component-specific setup programs. For example, you can use the Audit Analyzer Console.exe setup program to install Audit Analyzer on a computer.
Installing Group Policy Extensions Separately from Access Manager
Group policy extensions are packaged separately from Access Manager, enabling the following installation options:
-
You can install group policy extensions on any Windows domain
computer without also installing Access Manager on the computer.
-
You can install Access Manager on any Windows domain computer without also
installing group policy extensions on the computer.
The group policy extension package has its own .exe and .msi installer files, so that you can install group policy extensions interactively through an installation wizard (by executing the .exe file) or silently from the command line (by executing the .msi file). Additionally, you can select or de-select the group policy extensions for installation when you run the Access Manager installation wizard.
{b}Note: {/b}At the start of an installation, the group policy extension installer checks for previously installed versions of group policy extensions. If it detects a newer version than the version you are trying to install, the installation stops.
To install standalone group policy extensions interactively with the group policy installer:
-
On the Windows domain computer where you will install group policy extensions, navigate to the IBM Security ISO bundle containing the group policy extension installer file.
The installer file is named CentrifyDC_GP_Extension-*#.#.#-architecture.*exe.
For example:
CentrifyDC_GP_Extension-5.2.3-win64.exe
In most distributions, the installer file is located in the following folder in the ISO bundle:
DirectManage\Group Policy Management Editor Extension
-
Double-click the installer file to launch the Group Policy Management Editor Extension Setup Wizard.
-
Follow the wizard installation instructions to install the group policy extensions.
To install standalone group policy extensions interactively with the Management Services installer:
-
On the Windows domain computer where you will install group policy extensions, launch the setup program for ManagementServices components as described in Installing Verify Privilege Server Suite and updating Active Directory.
-
Proceed through the setup program until you reach the wizard page in which to select individual components to install.
-
De-select every component except for Group Policy Management Editor extension for managing group policies:
-
Continue to follow the wizard installation instructions as described in Installing Verify Privilege Server Suite and updating Active Directory until you are finished with the installation.
To install standalone group policy extensions silently without installing Access Manager:
-
Open a Command Prompt window.
-
Execute the group policy extension .msi installer file from the command line.
The installer file is named CentrifyDC_GP_Extension-*#.#.#-architecture.*msi.
For example:
CentrifyDC_GP_Extension-5.2.3-win64.msi
In most distributions, the installer file is located in the following folder in the ISO bundle:
DirectManage\Group Policy Management Editor Extension
The following is a typical command to run the 64-bit .msi installer file:
msiexec /qn /i "CentrifyDC_GP_Extension-5.2.3-win64.msi”
For more information about installing with a .msi file, see Installing Silently Without Joining a Zone silently on remote Windows computers.
To install Access Manager interactively without installing group policies:
-
On the Windows domain computer where you will install group policy
extensions, launch the Management Services setup program and select
Authentication & Privilege as described in Installing Verify Privilege Server Suite and
updating Active Directory.
-
Proceed through the setup program until you reach the wizard page in which
to select individual components to install.
- De-select the Group Policy Management Editor extension component.
-
Continue to follow the wizard installation instructions as described in Installing Verify Privilege Server Suite and updating Active Directory until you are finished with the installation.