Reference content -- Connector Configuration Program
Initial configuration of the IBM Security Connector follows installation with the connector configuration wizard, which launches automatically. To complete the wizard, you must identify a user group whose members can register devices and a container that stores accounts for registered devices. You must also identify a group whose users have permission to manage registered devices and manage the configuration.
The connector configuration program allows you to complete the initial configuration and to make changes when necessary. You can also run this application to monitor the status of your connector.
Privileged Access Service uses all of the available connectors configured for a service. Each server has a connector configuration program that you launch on the computer hosting the connector. Changes made to one connector in an installation (servers registered to the same customer ID), the changes are propagated to all the servers in the installation to ensure that they are all in sync.
The IBM Security Connector Configuration Program is installed on any computer where a connector is installed. You can launch it from the Windows Start menu. The application appears as a window with tabbed panels:
-
Status: Shows server name, IBM Security customer ID, and IBM Security connection status.
-
IBM Security Connector: Provides connector controls and option settings.
Supporting User Authentication for Multiple Domains
You install the connector on a host Windows computer that is joined to a domain controller to authenticate Privileged Access Service users who have an account in that domain. If you want Privileged Access Service to authenticate users in other domains, there are two connector installation models—which one you use depends upon whether the accounts are in trusted domains in a single forest or in multiple, independent domain trees or forests.
Note: If all of your Privileged Access Service users have their accounts in a single domain controller, you can skip this topic.
Configuring Authentication for Trusted Domains
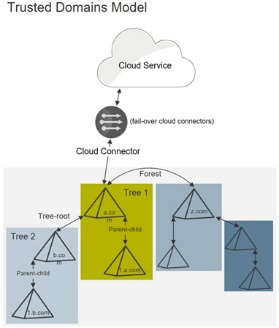
You use this model when the users’ Active Directory accounts are in domains with domain controllers that have a two-way, transitive trust relationship with the domain controller to which the connector is joined.
In this model, you have a single connector for the entire domain tree or forest. Privileged Access Service communicates through this connector for all authentication requests. When the user account is in another domain, the authentication requests are handled according to the tree-root, parent-child, forest, and shortcut trust relationship settings between the domain controllers.
If you are using Active Directory for device and policy management, all object management communications are done through the same connector as well.
By default, two-way transitive trusts are automatically created when a new domain is added to a domain tree or forest root domain by using the Active Directory Installation Wizard. The two default trust types are parent-child trusts and tree-root trusts. When you configure the trust relationship, be sure to select Forest trust. This establishes a transitive trust between one forest root domain and another forest root domain. See How Domain and Forest Trusts Work in Microsoft TechNet for more about trust relationships.
IMPORTANT: For tenants created after the Privileged Access Service 17.1 release, the connector by default does not perform cross forest user lookup from a local forest. To enable this functionality, contact IBM Security Support.
After you install the first connector, you should install one or more on separate host computers. The host computer for each connector must be joined to the same Active Directory domain controller. See Creating Administrator Consoles and Adding Additional Connectors for the details.
Privileged Access Service automatically creates a login suffix for the domain to which the host computer is joined plus all of the domains that the connector can see. Which domains can be seen depends upon two criteria:
-
The trust relationship between the domain controllers.
Only domain controllers with a two-way transitive trust meet this criteria
-
The connector’s user account permissions.
By default the connector is installed as a Local System user account on the Windows host. (See Permissions Required for Alternate Accounts and Organizational Units for more information.) The permissions you grant to this account can affect its ability to see other domains.
When the Admin Portal searches Active Directory domains for users and groups (for example, when you are adding a user or group to a role), it only searches the Active Directory Users container in the domain controllers that can be seen by the connector.
Independent Domains in Multiple Forests
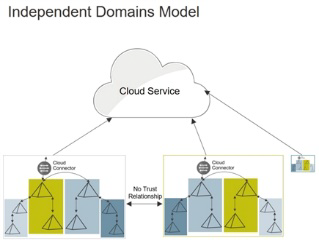
You use this model when the users’ Active Directory accounts are in independent domain trees or forests; that is, there are domain controllers that do not have a two-way, transitive trust relationships with each other.
In this model, you have a separate connector for each independent domain tree or forest. Privileged Access Service picks which connector to use for the authentication request based on the login-suffix-to-domain mapping it creates and maintains. When the user account is in the connector’s domain controller, the authentication requests are handled according to the tree-root, parent-child, forest, and shortcut trust relationship settings between the domain controllers in that forest or domain tree.
After you install the first connector for each independent domain tree or forest, you should install one or more on separate host computers for each one. The host computer for each connector must be joined to the same Active Directory domain controller as the initial connector for this tree or forest. See Creating Administrator Consoles and Adding Additional Connectors for the details.
Privileged Access Service automatically creates a login suffix for the domain to which the host computer is joined plus all of the domains that the connectors for each independent domain can see.
When Admin Portal searches Active Directory domains for users and groups (for example, when you are adding a user or group to a role), it only searches the Active Directory Users container in the domain controllers that can be seen by the connectors. Which domains can be seen depends upon two criteria:
The trust relationship between the domain controllers.
Only domain controllers with a two-way transitive trust meet this criteria. When you configure the trust relationship, be sure to select Forest trust. This establishes a transitive trust between one forest root domain and another forest root domain. See How Domain and Forest Trusts Work in Microsoft TechNet for more about trust relationships. The connector’s user account permissions.
By default the connector is installed as a Local System user account on the Windows host. The permissions you grant to this account can affect its ability to see other domains. See Permissions Required for Alternate Accounts and Organizational Units for more information.
If you are using this model, use the IBM Security directory policy service to set mobile device policies (see How to Select the Policy Service for Device Management and Privileged Access Service roles to enable users to register devices.
Modifying the Default Connector Settings
You use the IBM Security Connector Configuration Program to modify the default setting. See Reference content -- Connector Configuration Program for the description of each tab and how to modify the default settings.
There are several default settings you may need to change right after you install the connector:
| Setting | Tab | To Do This |
|---|---|---|
| Enable auto-update | IBM Security Connector | Configure the connector to automatically poll Privileged Access Service for software updates and install them. You can also specify the polling-update windows. |
| Active Directory user verification interval | IBM Security Connector | Set the polling period between queries for updates to active Active Directory user accounts. |
| Log settings | Logging | After you install a connector, you should configure the connector to log activities to help in troubleshooting in case you have any problems. Go to this tab to enable logging. |
Creating Administrator Consoles and Adding Additional Connectors
You use the same IBM Security Management Suite installer to install the additional connectors for load balancing and failover and administrator consoles to manage users, devices and group policy objects.
About Load Balancing and Failover
You should configure one or more connectors to provide continuous up time for Privileged Access Service services. Each connector you add is listed in Admin Portal on the Settings page in the IBM Security Connector tab.
Privileged Access Service provides load balancing among all connectors with the same services installed. For example, when a request comes in, Privileged Access Service routes the request among the available connectors. If one connector becomes unavailable, the request is routed among the other available connectors providing automatic failover.
Installing Additional Connectors
You use the same procedure to download the installation wizard to the host computer and then run the wizard to install and register additional connectors. After you install and register the connector, it is added to the IBM Security Connector page.
The host computer must be joined to the same Active Directory domain controller as the first connector in the same trust domain or forest.
Creating a Privileged Access Service Administrator Console
You use the same procedure to download the installation wizard to the host computer and then run the wizard. However, you do not install the connector. Instead, you install either or both of the console extensions.
The host computer must be joined to the same Active Directory domain controller as the connectors in the same trust domain or forest.
Using the Status Tab
The Status tab displays the following read-only information about the connector:
-
Server name displays the assigned name of this connector.
-
Customer ID displays the customer ID under which this connector is registered. You can install multiple connectors using the same customer ID for load balancing and failover. All active connectors are used by Privileged Access Service.
Do not change this field.
-
IBM Security Connector is started|stopped shows whether the connector is started (running) or not.
-
Connection to Privileged Access Service shows the date, time, and result of the last connection to Privileged Access Service.
Using the IBM Security Connector Tab
The IBM Security Connector tab reports the customer ID under which the IBM Security Connector is registered and whether or not the server is started. It also offers the following controls:
The Re-register button starts the IBM Security Connector configuration wizard and allows you to re-register this connector. Generally, you re-register the connector under the same customer ID, and then only if the connector is having difficulty communicating with Privileged Access Service and customer support recommends that you re-register to address the issue.
Re-registering under a different ID can destabilize your environment and should be done only after consulting with customer support. Changing the ID moves the connector from one installation to another. If the connector is the only server in an installation, removing the server from the installation will cause any device registration to the installation to fail, and registered devices will no longer receive policy changes.
Click Start to start the connector if it’s stopped.
Click Stop to stop the connector if it’s running.
Select Allow support to access local connector logs to give the identity provider the ability to open the connector log files. These files can help resolve a problem and are the only files the service provider can open. The default is selected.
Click View Log to view the connector log. How to Change Connector Log Settings.
Use the Settings update interval text box to set the number of minutes this connector takes between checks on connector settings with Privileged Access Service.
When any connector in an installation changes its settings, it sends those settings to Privileged Access Service. When a connector checks settings with Privileged Access Service, if there were new settings reported from any of the other connectors in the installation, the checking connector downloads and accepts those settings. This ensures that all connector is in an installation have the same settings.
Use the Active Directory user verification interval text box to set the number of minutes this connector takes between checks for active AD user accounts. When the connector checks Active Directory user accounts, it contacts Active Directory/to see if the user account listed for each registered device is active. If a device’s associated user account is not active (is disabled or removed), Privileged Access Service un-registers the device.
Select the Enable auto-update check box to turn on automatic update for the connector. When auto-update is on, the connector checks with Privileged Access Service periodically to see if there is a connector update. If there is, the connector downloads and installs the update, then restarts. This ensures that connector software is up-to-date. We recommend that you enable this option. See How to Auto-update Connector Software for the details.
Select Use a web proxy server for Privileged Access Service connection check box if your network is configured with a web proxy server that you want to use to connect to Privileged Access Service. Note that the web proxy must support HTTP 1.1 for a successful connection to Privileged Access Service. After you select this option, enter the following information to enable the web proxy connection:
-
Address is the URL of the web proxy server.
-
Port is the port number to use to connect to the web proxy server.
-
Click Credential to enter the user name and password for an account that can log in to the web proxy server.